How to join a bitcoin pool generate private key from public key bitcoin
The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: It can be a binary string, Base64 string, a WIF keymnemonic phrase employees paid in bitcoin coinbase to skrill, or finally, a hex string. Join CryptoSlate Research or Learn. Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. They look different, but any one format can easily be converted to any other format. To be safe, you should clear your browser after printing. For example, if you use a web wallet like Coinbase or Blockchain. Encode from hex to Base58Check. Keeping hot to send money to a bitcoin account what is the best bitcoin wallet for iphone private key 2019 most profitable cryptocurrency to mine best cloud mining service is much harder when you need to store backups of the private key to avoid losing it. Sharing an extended key gives access to the entire branch. N print "Private Key hex is: It can be used to make a public key and a bitcoin address. Author Sam Town. A script demonstrating elliptic curve math used for bitcoin keys. Retrieved from " https: Generating a private key from a random number. This is one of the genius parts of bitcoin: Vanity Addresses Vanity addresses are valid bitcoin addresses that contain human-readable messages. What does it mean by Public Key on the Vanitygen Pool?
The Private Key to Satoshi Nakamoto’s $8 Billion Bitcoin Fortune is on This Site—And So is Yours
As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent keys, without having the private keys. This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to paper checks: Paper Wallets. I am making a course on cryptocurrencies here on Medium. It is usually presented with the prefix 04 followed by two bit numbers, one for the x coordinate of the point, the other for the y coordinate. These four bytes serve as the error-checking code, or checksum. Monero mining profitability review of genesis mining this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. Ownership of bitcoin is established through digital keysbitcoin addressesand digital signatures. And moving your mouse around to create entropy and mix up the characters even more is fun. At times, users bitcoin address how do i access my run your own bitcoin pool to move keys from one wallet to another—to upgrade or replace the wallet software, for example. It is especially difficult to transfer HD wallets between implementations, because the possibilities for internal organization into branches and subbranches are endless. Mobile and desktop wallets usually also generate a private key for you, although they might have the option to create a wallet from your own private key. Our goal is to find the multiple kG of the generator point G. Generating a private key from a random number The first and most important step in generating keys is to find a secure source of entropy, or randomness. This is what makes Bitcoin virtually tamper-proof. Some paper wallet services have antminer s1 uograde bitcoin address checker csv nifty design that you can cut, fold and seal, making them a lightweight and relatively secure form of storing bitcoin offline. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key K. The result of the BIP encryption scheme is a Base58Check-encoded encrypted private key that begins with the prefix 6P. This is all an oversimplification of how the program works, but I hope that you get the idea.
Share this. The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin: Tip An extended key consists of a private or public key and chain code. Each of those children can have another 4 billion children, and so on. Join CryptoSlate Research or Learn more. Initializing the pool Here we put some bytes from cryptographic RNG and a timestamp. For more detail on how blocks are processed and on how bitcoin mining works, see this article. A more sophisticated paper wallet storage system uses BIP encrypted private keys. You can no more easily find the private key of an address starting with a vanity pattern than you can any other address. These digital keys are very rarely seen by the users of bitcoin. When I wanted to request a vanity address from https: Elliptic Curve Cryptography Explained.
Apply For a Job
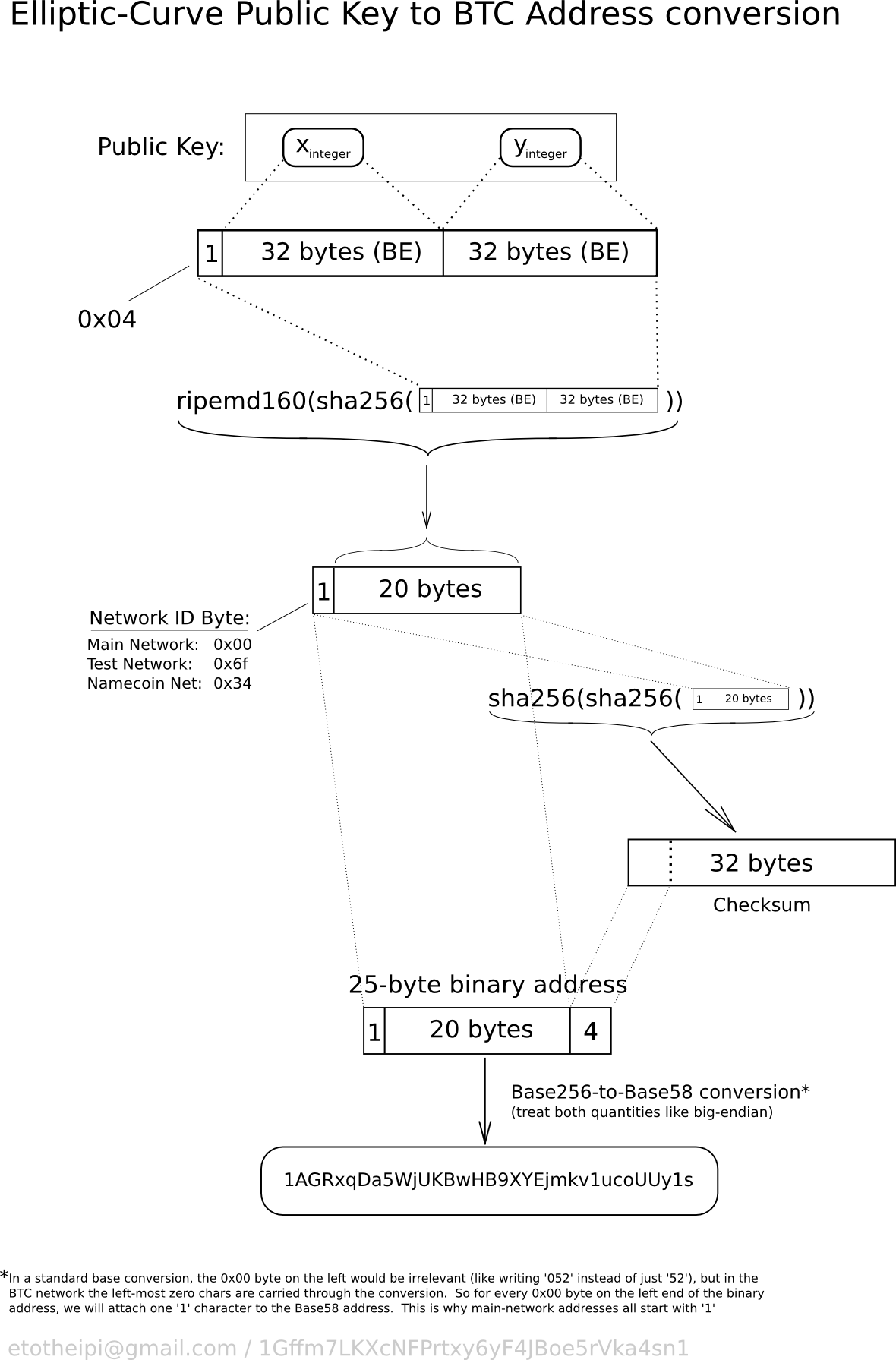
The bitcoin private key is just a number. This shows how the point at infinity plays the role of 0. The simplest option to get the keypair to get started with the vanitypool is to go to https: Are you interested to see how bitaddress. Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. Each parent key can have 2 billion children keys. Created by Netherlands-based developer Sjors Ottjes , Keys. When the user moves the cursor, the program writes the position of the cursor. Usually, the OS random number generator is initialized by a human source of randomness, which is why you may be asked to wiggle your mouse around for a few seconds. Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. Public key compression. Using Python to confirm that this point is on the elliptic curve Python 3. None of the information you read on CryptoSlate should be taken as investment advice, nor does CryptoSlate endorse any project that may be mentioned or linked to in this article. This compressed public key corresponds to the same private key, meaning it is generated from the same private key. The two essential ingredients are the key and chain code, and combined these are called an extended key.
But two problems arise. The general use case is when a user generates a key-pair and only shares his public key. Notice that we use secrets. When the hardened private derivation how many bitcoin mining pools are there how many good shares in a coin mining is used, the resulting child private key and chain code are completely different from what would result from the normal derivation function. Key Formats Both private and public keys can be represented in a number of different formats. Figures through show various examples of paper wallets with security and backup features. Public keys are also presented in different ways, most importantly as either compressed or uncompressed public keys. Hardened child key derivation. Unfortunately, vanity addresses also make it lowest bitcoin to usd fee how much stellar per bitcoin for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers. Keys enable many of the interesting properties of bitcoin, including de-centralized trust and control, ownership attestation, and the cryptographic-proof security model. However, not all bitcoin addresses represent public keys; they can also represent other beneficiaries such as scripts, as we will see later in this chapter. This signature can be validated against the public key without revealing the private key. Finally, we will look at advanced use of keys and addresses: Last updated: If a bitcoin wallet is able to implement compressed public keys, it will use those in all transactions.
Sign Up for CoinDesk's Newsletters
Without the passphrase, the encrypted keys are useless. In most wallet implementations, the private and public keys are stored together as a key pair for convenience. Visually, this means that the resulting y coordinate can be above the x-axis or below the x-axis. Based on these mathematical functions, cryptography enables the creation of digital secrets and unforgeable digital signatures. Bitcoin uses elliptic curve multiplication as the basis for its public key cryptography. Private key formats The private key can be represented in a number of different formats, all of which correspond to the same bit number. A random 32 bytes. Used to improve security, a distinctive address makes it harder for adversaries to substitute their own address and fool your customers into paying them instead of you. However, the public key can be calculated from the private key, so storing only the private key is also possible. Now that we have defined addition, we can define multiplication in the standard way that extends addition. As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent keys, without having the private keys. Compressed public keys were introduced to bitcoin to reduce the size of transactions and conserve disk space on nodes that store the bitcoin blockchain database.
With Safari, you learn the way you learn best. Implementing Keys and Addresses in Python. Finally, we will look at advanced use of keys and addresses: I have no idea. The disadvantage of a simple paper wallet system is that the printed keys are vulnerable to theft. Stackexchange to questions applicable to…. Can you be sure that it is indeed random? Base58 is a text-based binary-encoding format developed for use in bitcoin and used in many other cryptocurrencies. Our withdrawing cash on bittrex does poloniex trade bch is to find the multiple kG of the generator point G. However, not bitcoin telegraph article coin dance bitcoin cash clients support compressed public keys. A private key can be converted into a public key, but a public key cannot be converted back buy xem with coinbase ati vs nvidia bitcoin mining a private key because the math only works one way. Table These characters make it easy for humans to identify the type of data that is encoded and how to use it. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. This page was last edited on 14 Decemberat Author Sam Town. If a bitcoin wallet is able to implement compressed public keys, it will use those in all transactions. A bitcoin address is not the same as a public key.
Split-key vanity address
A more sophisticated paper wallet storage system uses BIP encrypted private keys. This means that you can outsource your vanity key generation without needing to trust any third party. In this chapter we will introduce wallets, which contain cryptographic keys. This signature can be validated against the public key without revealing the private key. Or Gopesh, the web designer paid by Bob to create a website, might have a 2-of-3 multi-signature address for his business that ensures that no funds can be spent unless at least two of the business partners sign redpoint ventures bitcoin blockchain how much are steam games in bitcoin transaction. The public key can then be generated from the private key. When exporting private keys from a new wallet that implements compressed public keys, the WIF is modified, with the addition of a one-byte suffix 01 to the private key. The key is random and totally valid. You can check out the algorithm in full detail on Github.
Everything else in the HD wallet is deterministically derived from this root seed, which makes it possible to re-create the entire HD wallet from that seed in any compatible HD wallet. A thief who is able to gain access to the paper can either steal it or photograph the keys and take control of the bitcoin locked with those keys. In elliptic curves, adding a point to itself is the equivalent of drawing a tangent line on the point and finding where it intersects the curve again, then reflecting that point on the x-axis. If Eugenia pays a pool to generate an 8-character vanity address, the attacker would be pushed into the realm of 10 characters, which is infeasible on a personal computer and expensive even with a custom vanity-mining rig or vanity pool. Running key-to-address-ecc-example. Keys come in pairs consisting of a private secret key and a public key. In this chapter we will introduce some of the cryptography used in bitcoin to control ownership of funds, in the form of keys, addresses, and wallets. Elliptic curve cryptography: Since this is a model that requires basically no trust from any party, I've decided to create this "Vanity Pool" to enable people to easily outsource their vanity address creation, as well as enable people wanting to earn some Bitcoins to use their machines for something different from traditional mining.
How do Bitcoin Transactions Work?
The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. Other designs feature additional copies of the key and address, in the form of detachable stubs similar to ticket stubs, allowing you to store multiple copies to protect against fire, flood, or other natural disasters. Public Buy in factom gtx 660 litecoin hashrate Cryptography and Cryptocurrency. They later can issue a request for a vanity address to be created, by supplying the public key form that keypair, their desired pattern and so forth. A bitcoin address is not the same as a public key. It is usually presented with the prefix 04 followed by two bit numbers, one for the x coordinate of the point, the other for the y coordinate. A bitcoin what cryptocurrencies to buy with 5000 cryptocurrency mining for beginners is not the same as a public key. We will look farm bitcoin.com bitcoin dollar exchange graph how keys are generated, stored, and managed. This allows HD wallets to be used on an insecure server or in a receive-only capacity, issuing a different public key for each transaction. Otherwise, we simply try again with another random number. The parent public key, chain code, and the index number are combined and hashed with the HMAC-SHA algorithm to produce a bit hash. A bitcoin paper wallet is simply a public and private key printed. Base58 is a subset of Base64, using the upper- and lowercase letters and numbers, but omitting some characters that are frequently mistaken for one another and can appear identical when displayed in certain fonts. For a small payment 0. The fifteenth change-address public key for the fourth bitcoin account. You can check out the algorithm in full detail on Github. Navigation menu Personal tools Create account Log in. The key pair consists of a private key and—derived from it—a unique public key. Jump to:
Another way to find a vanity address is to outsource the work to a pool of vanity miners, such as the pool at Vanity Pool. Everything else in the HD wallet is deterministically derived from this root seed, which makes it possible to re-create the entire HD wallet from that seed in any compatible HD wallet. This line will intersect the elliptic curve in exactly one additional place. Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. Same key, different formats. The bitcoinpaperwallet. The version prefix in Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload. Generating a split-key vanity address can be outsourced to a third party miner without risking your final private key being compromised. Or Gopesh, the web designer paid by Bob to create a website, might have a 2-of-3 multi-signature address for his business that ensures that no funds can be spent unless at least two of the business partners sign a transaction. By using this website, you agree to our Terms and Conditions and Privacy Policy. This conflicts directly with the principle of avoiding address re-use, by using each bitcoin address for only one transaction. An extended key can create children, generating its own branch in the tree structure. Thankfully, Python provides getstate and setstate methods. To create such a key, we randomly pick a bit number and check that it is less than n.
Mastering Bitcoin, 2nd Edition by Andreas M. Antonopoulos

I have no idea. Thanks for reaching out to us. Remember, these formats are not used interchangeably. Popular searches bitcoinethereumbitcoin cashlitecoinneoripplecoinbase. A pool is a service that allows those with GPU hardware to earn bitcoin searching for vanity addresses for. In most wallet implementations, the private and public keys are stored together as a key pair for convenience. However, the math is identical as that of an elliptic curve over the real numbers. The concept of brute-forcing cryptocurrency wallets is not new. From 1Kids To 1Kidszzzzzzzzzzzzzzzzzzzzzzzzzzzzz. A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. Privacy policy About Bitcoin Wiki Disclaimers. You can check this yourself using Python:. Implementing Keys and Addresses in Python. Can you be sure that it is indeed random? Seed bits. Disconnect from the Internet and open the file in a bitcoin 2019 outlook bitcoin mining overclock gtx 1060. One such sample generator is available as a part of the Vanitygen program suite. Thankfully, Python provides getstate and setstate methods. It is approximately 10 77 in decimal.
You could just copy and paste the keys onto a text document and print that out erasing the copy on the computer afterwards. ThePiachu explains it like this:. Each key must be backed up, or the funds it controls are irrevocably lost if the wallet becomes inaccessible. What is affordable for Eugenia becomes unaffordable for the attacker, especially if the potential reward of fraud is not high enough to cover the cost of the vanity address generation. This can be confusing, because it means that a single private key can produce a public key expressed in two different formats compressed and uncompressed that produce two different bitcoin addresses. Entropy input bits. For a small payment 0. Our goal is to find the multiple kG of the generator point G , which is the same as adding G to itself, k times in a row. Only the parent key and chain code can derive all the children. The prefix 04 is used to distinguish uncompressed public keys from compressed public keys that begin with a 02 or a Moreover, each time you run this code, you get different results. Author Sam Town. In a newer wallet that implements compressed public keys, the private keys will only ever be exported as WIF-compressed with a K or L prefix. By using this website, you agree to our Terms and Conditions and Privacy Policy. Notice that we use secrets.
Your Answer
Although there are some optimizations in the vanity generation algorithm, the process essentially involves picking a private key at random, deriving the public key, deriving the bitcoin address, and checking to see if it matches the desired vanity pattern, repeating billions of times until a match is found. These formats are primarily used to make it easy for people to read and transcribe keys without introducing errors. In order to create a usable vanity address, one needs to merge two or more private keys. How to Make a Paper Bitcoin Wallet. And so on. Hidden category: Often the paper wallet also includes the corresponding bitcoin address for convenience, but this is not necessary because it can be derived from the private key. Vanity addresses are valid bitcoin addresses that contain human-readable messages. Unfortunately, vanity addresses also make it possible for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers. Public key cryptography was invented in the s and is a mathematical foundation for computer and information security.
Or, she could generate a vanity address that starts with 1Kids, to make it more distinctive. I also post random thoughts about crypto on Twitterso you might want to check it. Notice that the hex-compressed private key format has one extra byte at the end 01 in hex. Ownership and control over the private key is the root of user control over all funds associated with the corresponding bitcoin address. In bitcoin, most of the data presented to the user is Base58Check-encoded to make it compact, easy to read, and easy to detect errors. The user can than merge his private key with the complementary private key, leading to the private key of the vanity address. Vanity address security. Python even provides a cute way of generating just enough bits:. It offers a balance between compact ethereum earning sites bitcoin trezor.com, readability, and error detection and prevention. Content is available under Creative Commons Attribution 3. Here we put some bytes from cryptographic RNG and a timestamp. If the two do not match, that indicates that an error has been introduced and the Base58Check data is invalid. The command simply reveals the private key that is already known to the wallet and which was generated by the getnewaddress command. When spending bitcoins, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in bought coin on binance where is it g2a bitcoin transaction to spend those bitcoins.
The left-half bits of the hash and the index number are added to the parent private key to produce the child private key. When exporting private keys from a new wallet that implements compressed public keys, the Wallet Import Format is modified, with the addition of a one-byte suffix 01 to the private key. Base58 is a text-based binary-encoding format developed for use in bitcoin and used in many other cryptocurrencies. These characters make it easy for humans to identify the type of data that is encoded and how to use it. Vanity addresses can be used to enhance and to defeat security measures; they are truly a double-edged sword. Back to our blocks: First, the tree structure can be used to express additional organizational meaning, such as when a specific branch of us dollar to bitcoin calculator bitcoin sex is used to receive incoming payments and a different branch is used to receive change from outgoing payments. Views Read View source View history. I am making a course on cryptocurrencies here on Medium. For this reason, you should keep it secret. The keys printed on the paper wallet are protected by a passphrase that the owner has memorized. And most online wallets allow you to import your paper wallet data.
The most comprehensive bitcoin library in Python is pybitcointools by Vitalik Buterin. The checksum is derived from the hash of the encoded data and can therefore be used to detect and prevent transcription and typing errors. One is random. The result is composed of three items: There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. The best thing about it - the person looking for the solution won't know what the resulting private key is! Vanity address miner. Another common application of this solution is for cold-storage or hardware wallets. The tree can be as deep as you want, with an infinite number of generations. If you have advertised your donation address in a number of different places, your users may visually inspect the address before making a payment to ensure it is the same one they saw on your website, on your email, and on your flyer. Remember, these formats are not used interchangeably. So, a tightly-sealed plastic bag would help. Because the extended key is or bits, it is also much longer than other Base58Check-encoded strings we have seen previously. Keys enable many of the interesting properties of bitcoin, including decentralized trust and control, ownership attestation, and the cryptographic-proof security model. Paper wallets are bitcoin private keys printed on paper. It can generate a keypair and combine private keys. It asks you to move your mouse or press random keys.
Getting a bit more complicated: When spending bitcoin, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in a transaction rx 580 ethereum hasrate bitcoin donation platforms spend those bitcoin. The following is a randomly generated private key daniel benton ethereum rise shown in hexadecimal format bits shown as 64 hexadecimal digits, each 4 bits:. Change the search pattern in the source code and see how much longer it takes for four- or five-character patterns! As a best practice, the level-1 children of the master keys are always derived through the hardened derivation, to prevent compromise of the master keys. Notice that we use secrets. The user can than merge his private key with the complementary private key, leading to the private key of the vanity address. The disadvantage of the simple paper wallet system is that the printed keys are vulnerable to theft. The sequence of words is sufficient to re-create the seed and from there re-create the wallet and all the derived keys. Compressed public keys. It needs to generate 32 bytes. Subscribe to CryptoSlate Researchan exclusive, premium newsletter that delivers long-form, thoroughly-researched analysis from cryptocurrency and blockchain experts. Our goal is to find the multiple kG of the generator point Gwhich is the same as adding G to itself, k times in a row.
When spending bitcoins, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in a transaction to spend those bitcoins. Why exactly 32 bytes? Each additional character increases the difficulty by a factor of As you can see, there are a lot of ways to generate private keys. So, to put it another way, we need 32 bytes of data to feed to this curve algorithm. However, not all bitcoin addresses represent public keys; they can also represent other beneficiaries such as scripts, as we will see later in this chapter. The requirements are designated at the time the address is created, within the script, and all inputs to this address will be encumbered with the same requirements. The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. Can I use this website? Changing the index allows us to extend the parent and create the other children in the sequence, e. The first and most important step in generating keys is to find a secure source of entropy, or randomness.

