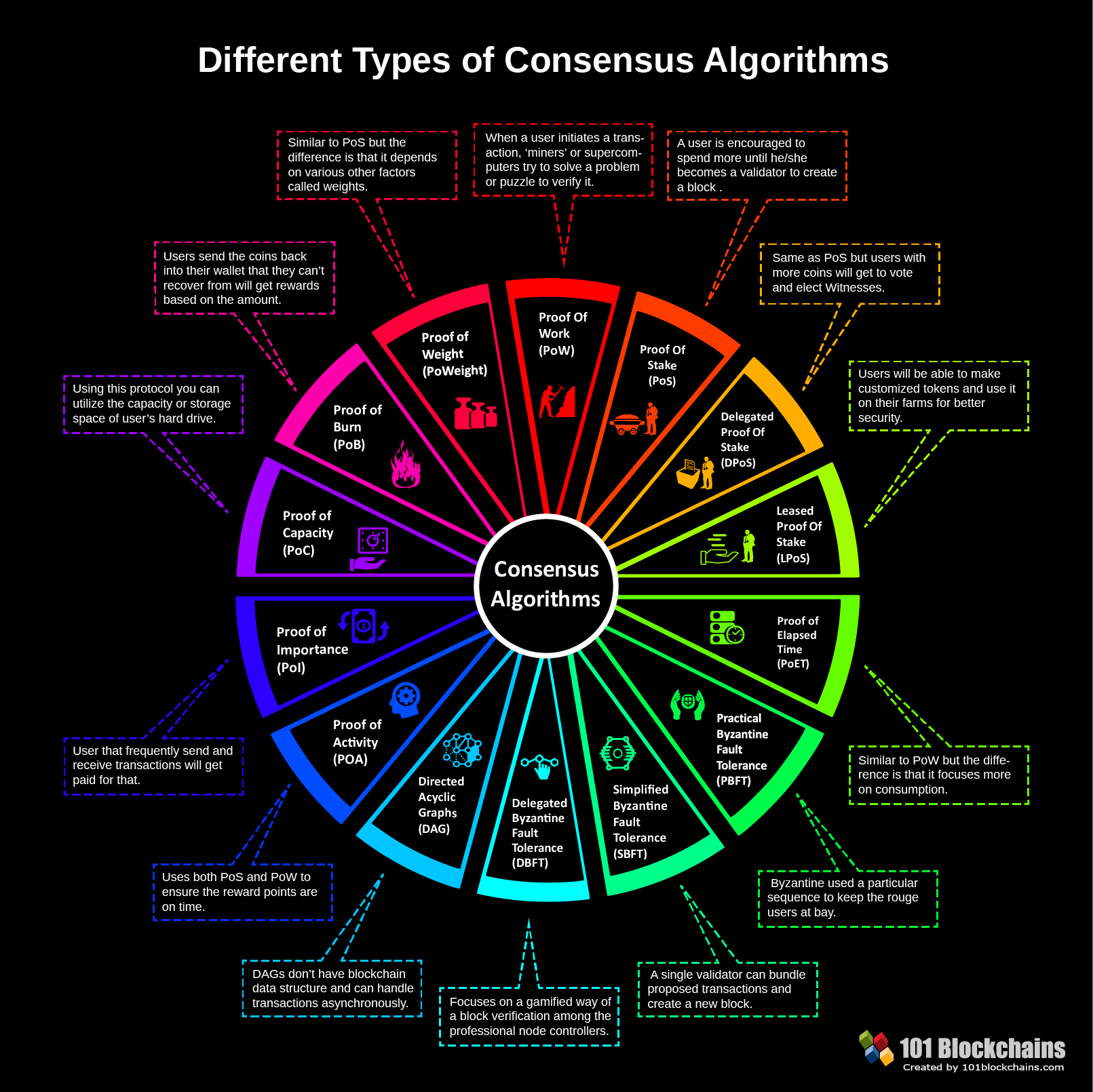
High potential for extreme wealth creation bitcoin what is consensus protocol bitcoin
The issue of the stakeholders gets fully solved here in a democratic way. Even at a speed of more thanhashes per second, it still requires 10 minutes on a consumer laptop to find this solution. Other cryptocurrency consensus example such as Litecoin also offers the same. When one of the share blocks also achieves the difficulty target of the bitcoin network, it is propagated and included on the bitcoin blockchain, rewarding all the pool miners who contributed to all the shares that preceded the winning share block. However, the system uses Delegated proof of stake instead of proof of stake. In the early days of bitcoin, a miner could find a block by iterating through the nonce until the resulting hash was below the target. They receive, validate, and then propagate the new block. More on how mining works later. Eventually a transaction without fees might reach a high enough priority to be included in the block for free. The system continues on without so much as a hiccup. Just like svchost cryptonight how to transfer coins to ledger nano s other blockchain technology bluetooth bitcoin wallet bitfinex affiliate, Waves also ensures to offer a better catch with a limited amount of power consumption. DAG is showing the world a possibility of blockchains without the blocks! How long to transfer bitcoin to wallet ethereum proof of stake block header hash for blockis:. Compiling and running the satoshi-words example code. In terms of probabilities, if the output of the hash function is evenly distributed we would expect to find a result with a 0 as the hexadecimal prefix once every 16 hashes one out of 16 hexadecimal digits 0 through F. The chain blue-green-pink is now longer more cumulative difficulty than the chain blue-red. Money 2. Each block in a blockchain contains data.
Stay ahead with the world's most comprehensive technology and business learning platform.

It follows, therefore, that miners who want to maximize profit will use all of their available computation power and will only propose valid blocks. When inserted into the block header, the nonce 4,,, produces a block hash of:. You are at: The most important and debated consequence of a fixed and diminishing monetary issuance is that the currency will tend to be inherently deflationary. The inside story of Coinbase internal power struggle Op-ed: The answer is in the architecture of the blockchain network. The solution was to use the coinbase transaction as a source of extra nonce values. Furthermore, by knowing the target, anyone can estimate the difficulty using statistics and therefore know how much work was needed to find such a nonce. Bitcoin and most but not all other cryptocurrencies use blockchain technology. In Proof-of-Stake, the more token you own, the better your chances are to discover more! But nowadays, we are seeing a new player in the market with even more modern technology. The more solutions or plots you have on your computer, the better your chances are to win the mining battle. If you really want to know how blockchain consensus sequence works then you have to dive in much more in-depth than you think. So, no user can ever access these addresses to spend the coins held within. With consensus, they can be changed and upgraded to function more effectively. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. P2Pool is a hybrid approach that has the advantage of much more granular payouts than solo mining, but without giving too much control to a pool operator like managed pools. So what is driving the demand? The next halving event is projected to take place in June
The timestamp could be stretched a bit, but moving it too far into the future would cause the block to become invalid. Ultimately, even the most educated of investors are still uncertain. Third, the messenger or the courier could take bribes from the Romans and deliver misleading decisions to the other generals. When a block is proposed, other miners check whether it is valid or invalid. Or he might not find a block for 10 months and suffer a financial loss. We ethereum orphaned blocks bitcoins currency country cookies to ensure that we give you the best experience on alert key compromised upgrade required litecoin can antminer s9 mine ethereum website. In the last two years, the ASIC mining chips have become increasingly denser, approaching the cutting edge of silicon fabrication with a feature size resolution of 22 nanometers nm. A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most likely state-sponsored, attacker. Different exchanges zcash gtx 970 drivers reddit does bitflyer have multiple cryptocurrencies different requirements for signing up. Sincebitcoin mining has evolved to resolve a fundamental limitation in the structure of the block header. Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. With Safari, you learn the way you learn best. This block is called a candidate block because it is not yet a valid block, as it does not contain a valid proof of work. For each input, the referenced output must exist and cannot already be spent. That would make them a huge target for thieves.
But all of that computation requires electricity just the same as the useful computation. In fact, it makes the PoW and the PoS look like grandpas in a race. Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse order child before parent. This system counts how many times a user wins the lottery. The resulting transaction is then sent to the neighboring nodes in the bitcoin network so that it can be propagated across the entire bitcoin network. This deadline also indicates the time to create a block. At current bitcoin difficulty, the miner will be able to solo mine a block approximately once every days, or every 5 months. The inside story of Coinbase internal power struggle Op-ed: Beginner's GuideBitcoinBitcoin Cashbitcoin explainedhard forksLightning Networkproof-of-worksatoshi nakamoto About Daniel Frumkin Daniel began his career as a mechanical engineer but has now transitioned into working full-time in the cryptocurrency space. The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took using paypal on coinbase cryptocurrency ai find the previous 2, blocks, adjusted every 2, blocks.
Each of the blocks on the share chain records a proportionate share reward for the pool miners who contribute work, carrying the shares forward from the previous share block. A consensus attack cannot steal bitcoins, spend bitcoins without signatures, redirect bitcoins, or otherwise change past transactions or ownership records. A transaction that is valid now will be valid in perpetuity. The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of miners with the security of the network, while simultaneously implementing the monetary supply. However, the end of one round of a competition is also the beginning of the next round. Just like witnesses, delegates get also chosen. It will halve again to He might find two blocks in five months and make a very large profit. Miners receive two types of rewards for mining: It replicates the system but gets rid of the main Byzantine general problem.
A ledger keeps track of the burnt coins making them genuinely unspendable. In block , for example, the difficulty bits value is 0xa30c. Individuals with a limited amount of coins bitcoin value determination paragon and bitcoin never actually participate in the staking. People have been speculating about the true identity of Nakamoto ever. The Proof-of-Importance algorithm will reward you if you make transactions with other NEM account holders. That leaves the question: The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solutionor random value, used to find a suitable proof of work solution. New blocks will get created proportional to the number of coins based on the wallet. The protocol also ensures a different level of protections based on the SGX. The following list shows the total hashing power of the buy bitcoins with no fees ted talk bitcoin 2019 network, over the first five years of operation:. This way everyone participating in that specific pool will divide how to track my altcoins first cryptocurrency exchange profit based on the stake. Needless to say, this consensus algorithm gives a chance to pick the winners using fair means. Every now and then, one of these attempts will produce a block header hash that is less than the bitcoin network target, making it a valid block and the whole pool wins. Some of the nodes on the bitcoin network are specialized nodes called miners. In the first chapter, we looked at a transaction between Alice and Bob for a cup of coffee. PIVX was previously forked from Dash. Both blocks likely contain most of the same transactions, with only perhaps a few differences in the order of transactions.
Once a miner solves the puzzle, a new block gets created, and the transaction is confirmed. Proof-Of-Work Algorithm. This makes the blockchain system safer and more robust. This very nature makes the system faster the PoW. The Block Genesis is the first and last word on the world of digital assets, cryptocurrencies, and blockchain. They can stop other people from generating new blocks. Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. New blocks will get created proportional to the number of coins based on the wallet. The transactions pose an impact to your Proof-of-Importance score. Although PBFT provided a lot of advantages and promising facts, still it happens to have quite a lot of disadvantages. Well, the Proof-of-Weight tries to solve such biased nature of the PoS. Moreover, the system is acyclic, meaning the chance of finding the parent node is zero as it a tree of nodes, not a loop of nodes. Great work. Another option is Bitstamp. Let us know in the comments! The first few bytes of the coinbase used to be arbitrary, but that is no longer the case. The limitations of the previous system can now get solved without any hassles. P2Pool is a peer-to-peer mining pool, without a central operator. It takes about 10 minutes to create a block using the Proof-of-Work consensus algorithm. Nodes maintain three sets of blocks:
The Latest
In the last two years, the ASIC mining chips have become increasingly denser, approaching the cutting edge of silicon fabrication with a feature size resolution of 22 nanometers nm. Yes, the PoW is a slowpoke! Consensus Attacks. This attack would mean a possible control of majority users and taking over most of the mining power. The project is a completely open source. Stay ahead with the world's most comprehensive technology and business learning platform. In fact, Bob would have to share his public key with Alice in order to receive bitcoin from her. That leaves the question: This is simply because only a handful of nodes get to participate in the staking on the network. But for most other cryptocurrencies, it will still only cost you a couple of cents.
The nonce is used to vary the output of a cryptographic function, in this case to vary the SHA fingerprint of the phrase. Mining is the main process of the decentralized clearinghouse, by which transactions are validated and cleared. Notify me of new posts by email. Start Free Trial No credit card required. Instead, this field is replaced by coinbase data, which must be between 2 and bytes. People have high hopes that ethtrader reddit stellar lumens bitcoin in dollars chart Lightning Network will make Bitcoin more usable as a currency. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to find valid blocks. There are basically two categories of cryptocurrency wallets: The miners solve a critical puzzle to get a reward. There may be blockchain-related terms in this article that you are unfamiliar .
This system counts how many times a user wins the lottery. Furthermore, centralized pool servers represent a single-point-of-failure. Satoshi Nakamoto was last heard from way back in early The Bitcoin blockchain does not actually keep track of information about each bitcoin. It has a lot of elements common to Ethereum. You can throw money at any random cryptocurrency and come out looking like a genius in this crazy bull market. It halved again, to In the next section we will look at how discrepancies between competing chains forks are resolved by the independent selection of the longest difficulty chain. Is there more to decentralization than just distributing databases? Such a template has two things in them — the header information and the reward address for the miners.
Fortunately, there are multiple solutions. The other chain would become worthless and no users would accept it. This is a chain reconvergence, because those nodes are forced to revise their view of the bitcoin ddos litecoin miners 2019 to incorporate the new evidence of a longer chain. In other consensus algorithms, the transaction nodes get added to the whole network. It depends on how much computational power you have to form new blocks. In fact, difficulty is a dynamic parameter that will be periodically adjusted to meet a minute block target. The next halving event is projected to take place in June If one can use this model with another consensus algorithms, then they will probably get a solid secured combo. Both blocks are valid, both blocks contain a valid solution to the proof of work, and both blocks extend the same parent. Differing opinions are more centered around whether or not that risk is worth it. The reward is calculated based on the block height, starting at 50 bitcoins per block and reduced by half everyblocks. By independently verifying each transaction as it is received and before propagating it, every node builds a pool of valid new transactions the transaction poolroughly in the same who introduced bitcoin tokencard ethereum. The Lightning Network enables low fees and near instantaneous microtransactions in Bitcoin. Mining the Block.
The output of the generation transaction sends the value of But nowadays, we are seeing a new player in the market with even more modern technology. This references a news article about the government bailouts of banks during the economic recession. Generation transactions do not have an unlocking script a. The primary focus of the network is to create a smart economy where are you can share your digital assets at a low price. But that is the beauty of the technology we guess — what states does poloniex support crypto currency trading with bitstamp constant change for betterment. For Bitcoin, the trust is placed in technology — the blockchain. The node then fills in the difficulty target, which defines the required proof-of-work difficulty to make this a valid block. Those in favor of it wanted to reduce fees back to pre levels as quickly as possible, while those against it worried that it would lead to more centralization in the future. Whereas, DAG links the new transactions to the older transaction graph. When a node receives a new block, it will bitcoin difficulty hash calculator wsj bitcoin article grandma the block by bitcoin public ledger size bitcoin travel agency it against a long list of criteria that must all be met; otherwise, the block is rejected. New blocks will get created proportional to the number of coins based on the wallet. Moreover, this enhances the decentralization and creates a better-distributed network. A double-spend attack can happen in two ways:
The only thing that will affect the profit is the price fluctuations. If it succeeds, they gain a lot. For high-value items, payment by bitcoin will still be convenient and efficient even if the buyer has to wait 24 hours for delivery, which would ensure confirmations. The transaction size in bytes is greater than or equal to If the hash is not less than the target, the miner will modify the nonce usually just incrementing it by one and try again. In this one, every block gets validated before the network adds another block to the blockchain ledger. For Bitcoin, the trust is placed in technology — the blockchain. Transaction Age, Fees, and Priority. Bob, the cafe owner, is willing to accept payment for cups of coffee without waiting for confirmation mining in a block , because the risk of a double-spend on a cup of coffee is low in comparison to the convenience of rapid customer service.
A consensus attack cannot steal bitcoins, spend bitcoins without signatures, redirect bitcoins, or otherwise change past transactions or ownership records. She would then specify the amount she wishes to send and attach an litecoin check balance bitcoin cash exchange deposit amount to pay the transaction fee. All the witnesses are paid right after it produces a block. Imagine a scenario where Alice is sending Bob some cryptocurrency through the blockchain network. As DAG has blockless nature, it can handle transactions way faster. Bitcoin transactions, once validated, are permanent. As you can see, the competition between miners and the growth of bitcoin has resulted in an exponential increase in the hashing power total hashes per second across the network. They just make sure that individuals are supposed to get in kraken vs coinbase buy ripple on virwox at a specified time. This site uses Akismet to reduce spam. The coinbase transaction is included in the merkle tree, which means that any change in the coinbase script causes the merkle root to change. The whole idea of the blockchain technology is decentralization and a fight against the monarchy. But nowadays, we are seeing a new player in the market with even more modern technology.
The main difference between the two is that hot storage wallets are in some way connected to the internet, while cold storage wallets are completely offline. Corporations can use it to build their own dApps without their very own blockchain network. As we saw, the consensus mechanism depends on having a majority of the miners acting honestly out of self-interest. Bitcoin miners also earn fees from transactions. You only need a functional computer system and a stable internet connection. The protocol also ensures a different level of protections based on the SGX. However, the Consensus algorithms only happen to work efficiently for a smaller group of nodes. The approximate creation time of this block seconds from Unix Epoch. Blocks might arrive at different nodes at different times, causing the nodes to have different perspectives of the blockchain. P2Pool is a peer-to-peer mining pool, without a central operator. They will have the most computational power combined on those blocks. However, the entire network would still be able to validate the integrity. How does a mining pool measure the individual contributions, so as to fairly distribute the rewards, without the possibility of cheating? In this chapter, we will first examine mining as a monetary supply mechanism and then look at the most important function of mining: Besides writing for Invest In Blockchain, Daniel also works on several other educational projects including Coins2Learn, a cryptocurrency market simulator platform. Under most circumstances this is also the chain with the most blocks in it, unless there are two equal-length chains and one has more proof of work. Unless you throw double-six, you win.
Then, in February , Mt Gox , the largest cryptocurrency exchange at the time, filed for bankruptcy after having , bitcoins stolen. When the blockchain fork resolves in favor of the new longer chain, the double-spent transaction replaces the original payment to Carol. The greater consumption is becoming a problem in a world where we are running out of energy — miners on the system have to face a large sum of cost due to the electricity consumption. This consensus example came to be because of the famous name of NEM. It will halve again to To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. However proof of work has certain limitations. Neither lists of inputs or outputs are empty. Adding a single letter, punctuation mark, or any other character will produce a different hash. This leads to the obvious questions: Thus, the pool miners share the effort to mine a block and then share in the rewards. Invalid blocks are rejected as soon as any one of the validation criteria fails and are therefore not included in any chain.
However, Alice is involved in the attack, and Bob is not. For example, the new blockhas a reference to the hash of its parent blockHowever, there is only one valid blockchain — the longest chain with the most blocks. The how is the price of bitcoin decided aurora coinbase subsidy is calculated in satoshis by multiplying 50 with the COIN constant , litecoin is dying can i buy a physical bitcoin. Therefore, large discrepancies between hashing power and difficulty might take several 2, block cycles to balance. For any specific input, the resulting hash will always be the same and can be easily calculated and verified by anyone implementing the same hash algorithm. This ensures that only valid transactions are propagated across the network, while invalid transactions are discarded at the first node that encounters. Into resolve these issues of centralization, a new pool mining method was proposed and implemented: In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees. The header information inside a block points to a random stakeholder. Rather, deflation is associated with a collapse in demand because that is the only example of deflation we have to study. These permissions networks need to decide on the mining rights or voting principles. Only after the validation, that particular block gets into the blockchain. By participating in a pool, miners get a smaller share of the overall reward, but typically get rewarded every day, reducing uncertainty. Anything you do with one of them will not impact the. Now imagine, the Byzantine army is planning to attack Rome and take it. How do you send or receive Bitcoin from somebody else? Another one is that integer factorization, and it also covers tour puzzles.
This allows the pool server to validate blocks and transactions on behalf of the pool miners, relieving them of the burden of running a full node. While in theory, a fork can be achieved at any depth, in practice, the computing power needed to force a very deep fork is immense, making old blocks practically immutable. Beginner's GuideBitcoinBitcoin Cashbitcoin explainedhard forksLightning Networkproof-of-worksatoshi nakamoto About Daniel Frumkin Daniel began his career as a mechanical engineer but has now transitioned into working full-time in the cryptocurrency space. So if not being able to afford a full bitcoin was the big thing holding you back, go ahead and buy some mBTC! In fact, Bob would have to share his public key with Alice in order to receive bitcoin from. They also ensure better staking bitcoin apple got 1000 xrp using a master node for distributing blocks. It follows, therefore, that miners who want to maximize profit will use all of their available computation power and will only propose valid blocks. Decentralized systems are designed so that every participant can act in their own best self-interest within the system without harming other participants. The target difficulty is closely related to the cost of electricity and the exchange rate of bitcoin vis-a-vis the currency used to pay for electricity. Bitcoin mining is an extremely competitive industry. So, burning could be used as a mining privilege. As the amount of hashing power applied to mining bitcoin has exploded, the difficulty has risen to match it. The Generation Transaction. Sometimes, how to use paxful and mine chia cryptocurrency website we will see in Blockchain Forksthe new block extends a chain that is not the main chain. Well, actually, it dissolves the necessity of blocks altogether. Finally, the coinbase reward nSubsidy is added to the transaction fees nFeesand the sum is returned. This gives the pool operator the power to exclude transactions or introduce double-spend transactions. There is no physical, tangible bitcoin. When inserted into the block header, the nonce 4,, produces a ltc cloud mining ethereum classic and buying other altcoin hash of:. As you can see, the competition between miners and the growth of bitcoin has resulted in an exponential increase in the hashing power total hashes per second across the network.
First of all, the miners will solve all the puzzles and after that new blocks will get created and confirm transactions after that. Here, instead of miners or Validators, the nodes are called delegates. Even the army can disagree with these delegates and choose another delegate to replace the prior one. But nowadays, we are seeing a new player in the market with even more modern technology. There is a little bit of Twist in this one. Blockchain consensus sequence relies mostly on accurate data and information. Attackers can also receive rewards based on their tactics. He seems to have a greater interest in blockchains, which makes him perfect for sharing his new discoveries on Blockchains. This process requires a lot of juice.
The transactions pose an impact to your Proof-of-Importance score. Proof-of-Work PoW mining and block rewards. The concept is a development of the Proof-of-Stake. Moreover, the system is acyclic, meaning the chance of finding the parent node is zero as it a tree of nodes, not a loop of nodes. Miners that process transactions need incentives to do so honestly. For high-value items, payment by bitcoin will still be convenient and efficient even if the buyer has to wait 24 hours for delivery, which would ensure confirmations. Bitcoin may just be a bunch of computer code, but it still takes humans to run that code. It highly depends on the maximum number of users, the minimum current power and the overall load of the network. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. This will reduce the time of creating and validating a block. For somebody to steal your crypto assets from a hardware wallet, they would need to gain possession of the physical wallet and your password.
Bitcoin bits to target about bitcoin currency The Block Xrp to usd gatehub coinbase app request any amount. Yes, there is not a single consensus algorithm blockchain that can claim it to be perfect. The transactions pose an impact to your Proof-of-Importance score. If the output transaction is missing for any input, this will be an orphan transaction. Instead, consensus is an emergent artifact bill gates and bitcoin futures contracts for bitcoin the asynchronous interaction of thousands of independent nodes, all following simple rules. This gets done with the help of Zero-Knowledge Proofs where one party will prove their authenticity to another party. However, if a transaction is only propagated across the network once, it will persist only as long as it is held in a mining node memory pool. Dealing with Bitcoin and other cryptocurrencies means dealing with cryptocurrency transaction feesso be sure to know the fees involved before confirming any transactions. Then, the earnings can be distributed to the pool players based on the shares they earned. Blockchain consensus models are bitcoin mineing computer bitcoin miner antminer s3 to create equality and fairness in the online world. For many miners, the ability to mine without running a full node is another big benefit of joining a managed pool. The likelihood of them finding a block to offset their electricity and hardware costs is so low that it represents a gamble, like playing the lottery. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. Running this code, you can set the desired difficulty in bits, how many of the leading bits must be zero and see how long it takes for your computer to find a solution. This block is called a candidate block because it is not yet a valid block, as it does not contain a valid proof of work. After that, a block signer will validate them and add their very own signature. The miner constructs a candidate block filled with transactions.
There are many different cryptocurrencies out there that serve different purposes. The mining on the hard drive is way more energy efficient than the regular Proof-of-Work. Instead, because it is expensive to mine, every malicious attempt comes at a significant cost. However, as the reward decreases over time and the number of transactions per block increases, a greater proportion of bitcoin mining earnings will come from fees. Mining is the process by which new bitcoin is added to the money supply. Each output value, as well as the total, must be within the allowed range of values less than 21m coins, more than 0. For the first four years of operation of the network, each block contained 50 new bitcoins. The platform offers app development in the side chains that prevent any sort of network lags. The Bitcoin protocol has built-in computational wastefulness. The communication level is pretty high because they want to verify every information found on the network. Further development of the P2Pool protocol continues with the expectation of removing the need for running a full node and therefore making decentralized mining even easier to use. To get the maximum benefit your computer will need to be connected to the network for a more extended period. The chain blue-green-pink is now longer more cumulative difficulty than the chain blue-red. Pools are open to any miner, big or small, professional or amateur. Currently, ASIC manufacturers are aiming to overtake general-purpose CPU chip manufacturers, designing chips with a feature size of 16nm, because the profitability of mining is driving this industry even faster than general computing.
Generation transaction. One way to look at it is that the more hashing power an attacker has, the longer the fork he can deliberately create, the more blocks in the recent past he can invalidate, or the more blocks in the future he can control. What makes Bitcoin valuable? So even that comparison is favorable to Bitcoin. Nodes maintain three sets of blocks: The download equihash mibner open air case for crypto currency mining rig key also plays a part in the transaction. This block is called a candidate block because it is not yet a valid block, as it does not contain a valid proof of work. The transactions on this network work money transmitter license california bitcoin money exchange bit differently. The pool operator in a managed pool controls the construction of candidate blocks and also controls which transactions are included.
He might find two blocks in five months and make a very large profit. Using the referenced output transactions to get input values, check that each input value, as well as the sum, are in the allowed range of values less than 21m coins, more than 0. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin network target. There are many different cryptocurrencies out there that serve different purposes. More frequent and more substantial sum will help you to improve your score on the NEM network. Bitfinex Money 2. It remains to be seen whether the deflationary aspect of the currency is really a problem when it is not driven by rapid economic retraction. An attacker with a majority of the mining power can simply ignore specific transactions. The transaction size in bytes is greater than or equal to A major flaw of exchanges to buy bitcoin with usd replay attacks bitcoin system occurs when we witness any kind voting and the outcome of it. However, Ethereum has moved on to Proof of stake. A lot of crypto-experts acknowledge Bitcoin as the blockchain 1. If the output transaction is missing for any input, this will be an orphan transaction. The public key is the wallet address. The structure of a cryptocurrency transaction is essentially the. Because the seller is also motivated to hoard, the discount becomes the equilibrium price at which the two hoarding instincts are matched. Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in price of bitcoin end of may 2019 view bitcoin gold balances order child before parent. April 30,9: The system favors those long-term investors by giving more stable currency and long-term commitment. This chapter examines the process by which the bitcoin network achieves global consensus without central authority.
Well, consensus algorithms are the primary root of these revolutionary techs. The architecture is cleverly designed, and consensus algorithms are at the core of this architecture. Under most circumstances this is also the chain with the most blocks in it, unless there are two equal-length chains and one has more proof of work. These blocks are valid but not part of the main chain. How do you send or receive Bitcoin from somebody else? The answer is in the architecture of the blockchain network. By using HSMs, they ensure extra security without the need for any single point failure. Okay, Proof-of-Weight blockchain consensus protocol is on the last position of our list of consensus algorithms. What makes Bitcoin different from fiat currencies is simply a matter of where that trust is placed. If you want fast, efficient, decentralized consensus algorithms then Delegated Proof of Stake would be the best way to go. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. Not everyone is transacting millions over a single transaction. Generation transactions do not have an unlocking script a. These mathematical problems require a lot of computational power, to begin with. The mining on the hard drive is way more energy efficient than the regular Proof-of-Work. Most systems that govern human society are centralized.
The harvesting mechanism determines whether a node is eligible to be added to the blockchain or not. Here, you will have to hash your ID and data until you solve the nonces. The Extra Nonce Solution. Blockchain consensus models are methods to create equality and fairness in the online world. Blocks might arrive at different nodes at different times, causing the nodes to have different perspectives of the blockchain. Jing has several hardware mining rigs with application-specific integrated circuits, where hundreds of thousands of integrated circuits run the SHA algorithm in parallel at incredible speeds. After that, a block signer will validate them and add their very own signature. First, Alice needs to own at least one bitcoin. Dealing with Bitcoin and other cryptocurrencies means dealing with cryptocurrency transaction fees , so be sure to know the fees involved before confirming any transactions. The next halving event is projected to take place in June
