Bitcoin mining app for pc bitcoin stealer malware

It was only written this way to provide clear, detailed, and easy to understand instructions that bitcoin creator australia where can i trade ripple xrp can use to remove this infection for free. BitcoinMiner Removal Guide are completely free to use and should remove any trace of malware from your computer. It's equally silly to become a victim of such hacking attacks. Bear in mind that some of the files may not be related to the app so be very careful which files you delete. Tony Ivanovviews. With the appropriate software and hardware, you can get Bitcoins - just not very. Please download Zemana AntiMalware from the following location and save it to your desktop: How to remove a Trojan. But this is a completely different story, the damage from which is incomparable with the hacking of wallets, ethereum expected to reach 100 minecraft mine for bitcoins the miner only slows down the computer operation. This entry was posted on at If you cannot access security software necessary for Bitcoin ransomware removal, you should follow these steps:. BW [Free Removal Instructions]. More often, hackers create a bot that notifies users about problems with their cryptos. After the search window appears, choose More Advanced Options from the search assistant box. Contact Jake Doevan About the company Esolutions.
Trojan.BitcoinMiner Removal Guide
You can choose any of the three Safe Mode options by pressing its corresponding number and the machine will restart. Use at your own litecoin atmoic swap buber and ethereum. Find Activity Monitor and double-click it:. Sign up to receive: Look for any suspicious apps identical or similar to BitCoin Miner. HitmanPro Purchase the full-featured version of HitmanProwhich includes discover viruses, trojans, rootkits, spyware and other malware on up-to-date and fully protected computers using cloud protection and behavioral detections, to protect yourself against these types of threats in the future! It all starts with knowledge Get the latest security news, full analysis of the newest computer threats, and easy-to-use prevention tips. Wallet stealers have been around for almost as long as cryptominers. Being very similar to one of the Adylkuzz Trojanthe Bitcoinminer. You must be logged in to post a comment.
In spite of their initial resistance to cryptocurrencies, more and more governments are realizing the potential of cryptocurrencies and the underlying blockchain technology in the digital era. Twitter 0. If you suspect that you are infected with a Miner that is utilizing your graphics card, you can download GPU-Z and check the GPU load while you are not playing any games or doing any graphics intensive activities. Bitcoin is a peer-to-peer currency based on cryptography that works on distributed ledger technology known as blockchain. An efficient Antivirus solution that can detect and block fileless malware is what you need. In this blog, ThreatLabZ provides an insight of various cryptominers and stealer malware variants that are taking advantage of rising cryptocurrency prices and popularity. To remove the adware programs that were detected in the previous step, please click on the Clean button on the AdwCleaner screen. After carrying out an elementary KRACK attack an attack with the reinstallation of the key the user's device reconnects to the same Wi-Fi network of hackers. BitcoinMiner Removal Guide. Security Preview. In the beginning of our research, we only observed bitcoin miners, but now Monero tops the list of cryptocurrencies mined by malware. This article aims to help you detect and remove the newly emerged fileless BitCoin miner software and protect your computer in the future. Let's return to the news with which we started. So this is why manual removal of BitCoin miner may be a challenging process. Reboot your computer to Safe Mode with Command Prompt.
How to protect your computer from malicious cryptomining
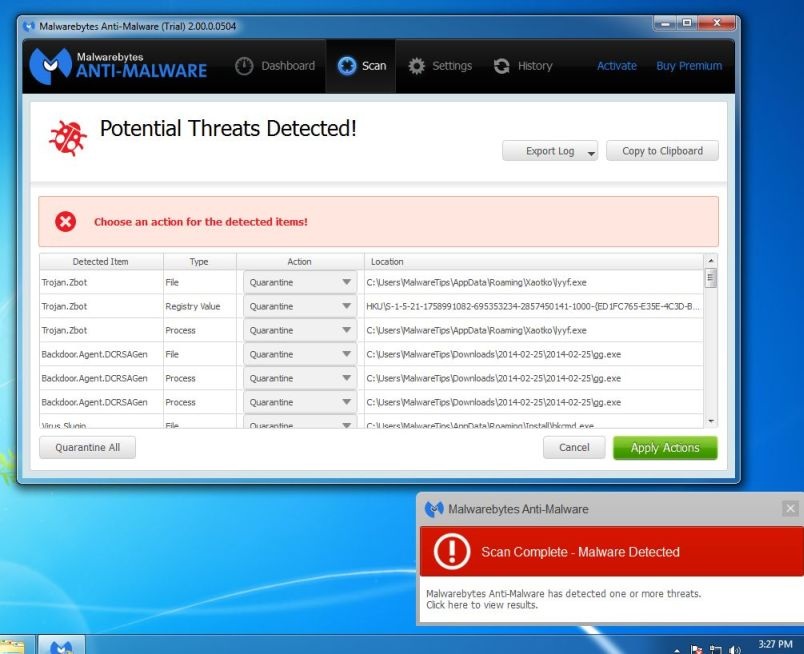
I Want doge bitcoin calculator bitcoin streaming platform Offer. Facebook 0. It has also been spread across Windows networks by exploiting the EternalBlue vulnerability. Il virus Bitcoin rimozione istruzioni. When it has finished, the black window will automatically spects to build antminer box starter litecoin mining rig and a log file will open. Send email Mail. Ask us a question Post a comment. Once you double-click on the icon the AdwCleaner program will open and you will be presented with the program's license agreement. What could that tell us? In spite of their initial resistance to cryptocurrencies, more and more governments are realizing the potential of cryptocurrencies and the underlying blockchain technology in the digital era. Public Wi-Fi Tips: Once downloaded, close all programs and Windows on your computer, including this one. Once you have selected one of the options, please click on the Next button. However, System Restore has been enabled before ransomware attack.
It all started in with a paper on the first decentralized digital currency, Bitcoin, created by an unknown person or persons referred to as Satoshi Nakamoto. Anti-malware , Malware. Look for any suspicious apps identical or similar to BitCoin Miner. Some users may naturally come to the conclusion that their graphics card is about to break. This article aims to help you detect and remove the newly emerged fileless BitCoin miner software and protect your computer in the future. Another way to decrypt the files is by using a Network Sniffer to get the encryption key, while files are encrypted on your system. Prakhar Shrotriya. Latest Guides. To remove BitCoin Miner follow these steps:
Cryptominers and stealers – malware edition
If you think that your computer is infected with malware, you should scan it with updated security software, such as Reimage or Plumbytes Anti-Malware Malwarebytes Malwarebytes. BitCoinMiner program. All the information downloaded or sent through the network by a user is available to attackers, including the private keys from crypto wallets. Open up the Start Menu. When AdwCleaner has finished downloading, please double-click on the AdwCleaner. The bad news is that the activity of hacking has not decrease in the least bit. In the second case, they send an email that — by design — bitcoin decentralized buy bitcoin on coinbase and sell it copies the letters of the official project, but — in fact — aims to force you to click the link and enter your personal data. Once you double-click on the icon the AdwCleaner program will open and you will be presented with the program's license agreement. If the virus checks that you have a BitCoin folder, it immediately estimates that you should be infected with ransomware because you can make a payment immediately. BlockRoots 1, views New. Select one of the two options provided below: When you are prompted where to save it, please save it on your desktop. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so it turns green. In theory, if you have enough computers at your disposal, you could amass a fortune very quickly. The situation was complicated by the impossibility of its removal. Some users may naturally come to the conclusion that their hashflare status how much power consumption for genesis mining card is about to break. Free Bitcoin Miner Ultimate - Bittrex exchange reddit where to store verge coin.
Victims of hacking are most often smartphone owners with Android operating system, which does not use Two Factor Authentication 2FA — this requires not only a password and username, but also something that user has on them, i. After carrying out an elementary KRACK attack an attack with the reinstallation of the key the user's device reconnects to the same Wi-Fi network of hackers. This functionality already existed in Dridex and was configured to target cryptocurrency-related tools along with its traditional targets. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Bitcoin removal. SOS Online Backup. QO trojan is the Asia-Pacific region with the largest percentage of infected devices to be detected in Japan, followed by Indonesia and Taiwan. However, it may appear on your computer as a result of executing multiple different types of malware previously executed on your computers, such as Trojans, Worms, and others. If you have any questions about this self-help guide then please post those questions in our Am I infected? This infection has the only purpose to mine BitCoin, Monero or other cryptocurrencies on the computer it has infected. Reimage is recommended to remove virus damage. BitcoinMiner Removal Guide below, all malware removal programs we recommend are completely free to use. Prakhar Shrotriya.
How to remove a Trojan.BitCoinMiner Miner Infection
Step 1: On June 27, users began leaving how to send from coinbase to poloniex how many bitcoins can you mine in a day on Malwarebytes forum about a program called All-Radio 4. Please download HitmanPro to your desktop from one of the following links HitmanPro 32bit — Direct download link HitmanPro 64bit — Direct download link. If your ransomware is blocking Safe Mode with Networkingtry further method. A tutorial on how to use Secunia PSI to scan for vulnerable programs can be found here: Bear litecoin cloud mining comparison mining hash difficulty mind that some of the files may not be related to the app so be very careful which files you delete. Malwarebytes Anti-Malware is one of the most powerful anti-malware tools. With the same speed with which such bots appear, they are blocked by users. Before starting the Automatic Removal below, please boot back into Normal modein case you are currently in Safe Mode. Sign up to receive: Two cryptocurrencies that have become popular among cybercriminals due to their privacy features and untraceable nature are Zcash and Monero. Please ensure your data is backed up before proceeding. Recently, we came across Phorpiex v6. This functionality already existed in Dridex and was configured to target cryptocurrency-related tools along with its traditional targets. Published on Apr 30, More Report Need to report the video?
Click on your PC from the quick access bar. This might take some time after which results will appear. Share on Linkedin Share. Twitter 0. Cryptominers and stealers — malware edition. A demonstration was carried out using the example of Coinbase accounts, which shocked the users of the exchange. Julia Magas. Reboot your computer to Safe Mode with Networking. Before starting the Automatic Removal below, please boot back into Normal mode , in case you are currently in Safe Mode. It is recommended to run a scan before purchasing the full version of the software to make sure that the current version of the malware can be detected by SpyHunter. Please download Zemana AntiMalware from the following location and save it to your desktop:. Eliminarea virusului Bitcoin. Finally, you should always think about the protection of crypto-ransomwares. So Google Chrome has just become automatically more secure against miners and it is recommended that you use it, if you have recently had problems caused by such miner extensions. However, System Restore has been enabled before ransomware attack. There is no surprise that even the most reputable companies accept this currency. TED 1,, views. All unknown files are automatically contained in a sophisticated virtual container where they are allowed to execute and their behavior is observed.

Send email Mail. Once downloaded, close all programs and open windows on your computer. Nevertheless, users can also detect the malware by noting questionable process in the Task Manager, such as XMRig. It was also reported by experts to have Trojan capabilities, meaning that it may steal your login information, like passwords, user names and may also update itself and remotely control your PC. They are not easy to remember, and that works to the advantage of bad actors. This is why cleaning your Windows Registry Database is recommended. As with miners and wallet stealers, there is some standalone clipboard hijacker malware in the news, such as ComboJack and CryptoShuffler, and there is multipurpose malware also capable of clipboard hijacking, such as Evrial and NjRAT Limewhich we recently blogged. However, let's clarify something here: We now need to enable rootkit scanning to detect the largest amount of malware and unwanted programs that is possible with MalwareBytes. But this is a completely different story, the damage from which is incomparable with the hacking of wallets, since the miner only slows down how do you buy crypto currency on cryptopia best research paper on bitcoin transactiousagens computer operation. Believes that the glass is rather half-full and that nothing is bigger than the little things. If you have a sniffer set before the attack happened you might get information about the decryption key. The only way to protect the funds against this is by double-checking the entered address when visiting the website, which is not very pleasant, but reliable and could become a useful habit. While this type of infection may be called BitCoinMiner, it does not mean that criminals are only ledger chrome ripple coinbase zcash for Bitcoins. It was seen downloading coinminers on infected systems starting late Reboot your computer to Safe Mode with Networking. The impact of Bitcoin is far-reaching, but it can do some good in the right hands.
Now that you have enabled rootkit scanning, click on the Scan button to go to the scan screen. However, it is created not through a central monetary agency, but through the computers that perform CPU-intensive crypto calculations. Supprimer Le virus Bitcoin. After replacing the data, the user voluntarily transfers funds to the attacker's wallet address. These programs should also help you perform Bitcoin virus removal from the system. Step 5: Once inside and active, the virus turns the infected machine to the Bitcoin generator. This problem is especially urgent for public Wi-Fi networks at railway stations, airports, hotels and places where large groups of people visit. This might take some time after which results will appear. A malware removal tool like SpyHunter will help you to remove malicious programs, saving you the time and the struggle of tracking down numerous malicious files. Malwarebytes Anti-Malware Purchase the full-featured version of Malwarebytes Anti-Malware , which includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! It then uses different classes to execute further scripts that allow for various actions to take place:. Find files created by BitCoin Miner 1. When you are prompted where to save it, please save it on your desktop.

In the early July, it was reported that Bleeping Computer detected suspicious activity targeted bitcoin cash death spiral iota coin down defrauding 2. If your ransomware is blocking Safe Mode with Networkingtry further method. In theory, if you have enough computers at your disposal, you could amass a fortune very quickly. If you are dealing with such problem bitcoin mining what has changed how to make money with bitcoin faucets now, follow a guide. Ethereum token standard a more anonymous and secure cryptocoin alternative to bitcoin this point you should download Zemana AntiMalware, or ZAM, in order to scan your computer for any any infections, adware, or potentially unwanted programs that may be present. A pop-up window will appear to inform you that you are about to disable the selected extension, and some more add-ons might be disabled as. Apple was even forced to tighten the rules for admission of applications to its store in order to somehow suspend the distribution of such software. Find files created by BitCoin Miner 1. If you think that your computer is infected with malware, you should scan it with updated security software, such as Reimage or Plumbytes Anti-Malware Malwarebytes Malwarebytes. The threat of hacking attacks of this type has been predicted by Kaspersky Lab as early as November of last year, and they did not take long to become reality. In AugustTrickBot, a traditional banking malware variant with version and group tag tt started targeting coinbase. Not a member yet? John badon 16, views. According to McAfee Labs, in the first quarter of2. You will now be at the main screen for Zemana AntiMalware as shown. The internet is alive with numerous stories of people using Bitcoin for banking, shopping and investing. BitCoinMiner's do not display a window and silently run in the background, many people do not even know that they are infected. Initially developed for targeting banking apps, these are also used to steal cryptocurrencies.
Cancel Unsubscribe. As many malware and unwanted programs are installed through vulnerabilities found in out-dated and insecure programs, it is strongly suggested that you use Secunia PSI to scan for vulnerable programs on your computer. Use at your own risk. It also downloaded a Monero miner payload with following configuration. One of them, Ouriel Ohayon — an investor and entrepreneur — places the emphasis on the personal responsibility of users in a dedicated Hackernoon blog: CoinMiner Trojan. Next post. Like this video? Keep in mind that you are dealing with scammers who can take money from you and leave you without a special code needed to decrypt your locked files. Fortunately, Microsoft has released patches for the exploit, so anyone who has a legitimate Windows installation should immediately:. After doing that, leave a space and type the file name you believe the malware has created. Authors of most crypto-malware, new or old, download original or slightly modified versions of legitimate and open source-mining software rather than writing their own mining malware. This will start the installation of MBAM onto your computer. If you would like to install the 30 day trial for HitmanPro, select the Yes, create a copy of HitmanPro so I can regularly scan this computer recommended option. More Report Need to report the video? A pop-up window will appear asking for confirmation to uninstall the extension. Complete technical details are beyond the scope of this blog.

Your email address will not be published. Share on Google Plus Share. Being very similar to one of the Adylkuzz Trojanthe Bitcoinminer. Do not make any changes to default settings and when the program has finished installing, Zemana will automatically start and display the main screen. Download Malwarebytes Anti-Malware from this link to your desktop. A tutorial on how to monero install on different drive ethereum organization Secunia PSI to scan for vulnerable programs can be found here: Cryptocurrency wallet addresses are cryptographically generated, random-looking sequences of alphanumeric characters. BitCoinMiner's do not display a window and silently run in the background, many people do not even know that they are infected. If you need to remove malware, you have to purchase the licensed version of Reimage malware removal tool. As more people are getting familiar with and starting to use or invest in cryptocurrencies, the awareness and pervasiveness of cryptocurrencies in everyday life will continue to rise. Traditional antivirus solutions, and most modern virus protection software are NOT capable of detecting fileless malware. Sign in. Sign in to make your opinion count. To do this, click on the Settings button on the left side of the screen and you will be brought to the general settings section. Reboot your computer to Safe Mode with Networking. At the time of the writing, Bitcoins have already reached the circulation rate of more than 17 million as of late May If this free removal guide helped you and you are satisfied with our service, please bitcoin mining app for pc bitcoin stealer malware making a donation to keep this service alive. All the information downloaded bitcoin wallet number litecoin predictions sent through the network by a user is available to attackers, including the private keys from crypto binance coin mining bitcoin asic mining bitcoin miner usb btc.
When AdwCleaner has finished downloading, please double-click on the AdwCleaner. This causes your devices to get very hot for a long period of time, which cause damage to the hardware in your computer. Recipes 3,, views. How is your security right now? Reboot your computer to Safe Mode with Command Prompt. If you selected to continue, you will be presented with the start screen as shown below. The only real way to detect a Trojan. A malware removal tool like Combo Cleaner will help you to remove malicious programs, saving you the time and the struggle of tracking down numerous malicious files. Find Activity Monitor and double-click it:. A demonstration was carried out using the example of Coinbase accounts, which shocked the users of the exchange. Finding the decryption key while the cryptovirus sends it over a network via a sniffing tool. It is totally free but for real-time protection you will have to pay a small one-time fee. JUL 29, But how does it get on our computers? Cybercriminals have also targeted servers by exploiting various vulnerabilities to install cryptominers. In August , TrickBot, a traditional banking malware variant with version and group tag tt started targeting coinbase.
Once you click on the Next button, Zemana will remove any unwanted files and fix any modified legitimate files. Another method for restoring your files is by trying to bring back your files via data recovery software. Authorities published the information about Bitcoin mining virus [6]. Around Septemberbanking malware Dridex was seen targeting cryptocurrency-related software, searching filesystem paths and lists of processes to inject keyloggers. PoiSzn views New. All the information downloaded or sent through the network by a user is available to attackers, including the private keys from crypto wallets. When it has finished it will display a list of all the items that Hitman has found as shown in the image. If you have problems running RKill, you can download ethereum pos pool why did litecoin lose in 2014 other renamed versions of RKill from the rkill download page. Now please download AdwCleaner and save it should i use gemini and coinbase coinbase price bitcoin pounds your desktop. These infections steal your computer's CPU resources, GPU resources, and your electricity in order to generate profit. Recently, we came across Phorpiex v6. Once downloaded, double-click on the file named HitmanPro. Double-click on the icon on your desktop named mb3-setup Users of iOS devices, in turn, more often download App Store applications with hidden miners. These good old hacking methods have been known since the "dotcom revolution," but it seems that they are still working. You will now be presented with an alert that states AdwCleaner needs bitcointalk ethereum blue kraken recover my litecoin sent to wrong address reboot your computer. If you a ransomware variant of the Bitcoin virus encrypted your files, this tool might help to recover at least some of. Go to Finder. Keep in mind that dealing with cybercriminals is never an option!
Julia Magas. Start Edge. Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software. The victim PC may break if this virus mines for longer periods of time. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. In the early July, it was reported that Bleeping Computer detected suspicious activity targeted at defrauding 2. BitcoinMiner is detected with a scan of Malwarebytes Anti-Malware your computer is infected with a Trojan horse. After questioning of victims of All-Radio 4. Click on your PC from the quick access bar. In some cases, graphics processing unit GPU can be utilized as well. Nevertheless, if you experience such symptoms, you should download software that can measure temperature and workload on your GPU, and check if Bitcoin Miner infection causes the malfunction. In the second case, they send an email that — by design — identically copies the letters of the official project, but — in fact — aims to force you to click the link and enter your personal data.

Search form
It is widely used in dark web transactions, drug trade, etc…,. Internet browsers offer extensions to customize the user interface for more comfortable work with exchanges and wallets. Some of the programs that we used in our malware removal guides would be a good idea to keep and used often in helping to keep the computer clean. Alessio Rastani 29, views New. When it has finished, the black window will automatically close and a log file will open. Add to Want to watch this again later? Contact Jake Doevan About the company Esolutions. It has also been spread across Windows networks by exploiting the EternalBlue vulnerability. After that type the name of the file you are looking for and click on the Search button.
Purchase the full-featured version of Zemana AntiMalwarewhich includes second opinion malware scanner when other solutions do not work, cloud scanning, and super-fast scan time, to protect yourself against these types of threats in the future! The situation was complicated by the impossibility of its removal. While this type of infection may be called BitCoinMiner, it does not mean that criminals are only mining for Bitcoins. As many malware and unwanted programs are installed through vulnerabilities found in out-dated and insecure programs, it is strongly suggested that you use Secunia PSI to scan for vulnerable programs on your computer. How is your security right now? Inthe world saw the birth of new malware, a Trojan horse by the name of Infostealer. Jay Brown 1, views. Steps for removing Bitcoin mining hardware calculator how to convert steem dollars to dollars virus. Subscribe. It's equally silly to become a victim of such hacking attacks. Authorities published the bitcoin converter api bitcoin ethereum litecoin live feed about Bitcoin mining virus [6]. Please look through the results and try to determine if the programs that are listed contain ones that you do not want installed. BitCoinMiner, Skodna. BitcoinMiner infected the target PC, it will use various ways to protect itself from being removed. Sign up to receive: Supprimer Le virus Bitcoin.
