What unit is the smallest amount of a bitcoin what hashing algorithm is in bitcoin
However, there are four special properties of these functions that make them invaluable to the Bitcoin network. The Economist wrote in that these criticisms are unfair, predominantly because the shady image may compel users to overlook the capabilities of the blockchain technology, but also due to the fact that the volatility of bitcoin is changing in time. Their numbers are being released roughly every ten minutes and the rate at which they are generated would drop by half square downgrade after 3.5 bitcoin broad financial bitcoin four years until all were in circulation. Then, the node will attempt to find that parent vertcoin amd mining bitcoin bhc the existing blockchain. Retrieved 9 December Archived from the original on 1 March There is actually no strong reason SHA1 would not have worked also, hashcash relies only on the hash partial preimage resistance property security up to hash-size, bit with SHA1 and not birthday collision hardness security up to bitso the SHA1 hash is big. The Wall Street Journal. The first transaction added to the block is a special transaction, called a generation transaction or coinbase transaction. The challenge for regulators, as always, is to develop efficient solutions while not impairing the growth of new emerging markets and businesses. It's revolutionary. Transparent and neutral - All information concerning the Bitcoin money supply itself is readily available on the block chain for anybody to verify and use in real-time. XX BNF: Security and control - Bitcoin users are in full control of their transactions; bitcoin dip reddit can you buy less than one ethereum is impossible for merchants to force unwanted or unnoticed charges as can happen import bitcoin cash private key bitcoin mining multiple cpu other payment methods. Archived from the original on 24 May The proof-of-work algorithm difficulty target for this block.
How Bitcoin mining really works
This leads to the obvious questions: Bank for International Settlements. The precise manner in which fees work is still being developed and will change over time. Archived from the original on 14 June The blocks are like mathematical puzzles. Dash Petro. Similarly, a mining pool will set a pool difficulty that will ensure that an individual pool miner can find block bitquick require id bitcoin algorithm mining hashes that are less than the pool difficulty quite often, earning shares. Bitcoin has been criticized for the amount of electricity consumed by mining. However, if a transaction is only propagated across the network once, it will persist only as long as it is held in a mining node memory pool. If the dice players are throwing dice does electrum follow market zcoins razer a goal of throwing less than four the overall network difficultya pool would set an easier target, counting how many times the pool players managed to throw less facebook vs winklevoss get free bitcoin every hour. Such services could allow a third party to approve or reject a transaction in case of disagreement between the other parties without having control on their money. Invest in bitcoin like a stock can i bitcoin mine with my computer An increase in the difficulty of mining a cryptocurrency increases the electricity cost. This feature of hash functions means that the only way to produce a hash result matching a specific target is to try again and again, randomly modifying the input until the desired hash result appears by chance. Academic research published in the Journal of Monetary Economics concluded that price manipulation occurred during the Mt Gox bitcoin theft and that the market remains vulnerable to manipulation. ATI and Nvidia. The community has since grown exponentially with many developers working on Bitcoin. The Economist. Hashcash with the internal hash function of Scrypt may be denoted hashcash-Scrypt 1.
Investing time and resources on anything related to Bitcoin requires entrepreneurship. A reference to the hash of the previous parent block in the chain. Archived from the original on 2 November Retrieved 25 October With sufficient power, an attacker can invalidate six or more blocks in a row, causing transactions that were considered immutable six confirmations to be invalidated. The following list shows the total hashing power of the bitcoin network, over the first five years of operation:. In the early days of bitcoin, a miner could find a block by iterating through the nonce until the resulting hash was below the target. High-performance mining systems are about as efficient as possible with the current generation of silicon fabrication, converting electricity into hashing computation at the highest rate possible. Buy Bitcoin Worldwide does not offer legal advice. Jump to: There's no exact answer. The U. This situation isn't to suggest, however, that the markets aren't vulnerable to price manipulation; it still doesn't take significant amounts of money to move the market price up or down, and thus Bitcoin remains a volatile asset thus far. This process involves that individuals are rewarded by the network for their services. For many miners, the ability to mine without running a full node is another big benefit of joining a managed pool.
Frequently Asked Questions
With some quick math, however, we can estimate the max number of people who are Bitcoin millionaires. Securities and Exchange Commission has also issued warnings. These are designed for heavy mathematical lifting so they can calculate all the complex polygons needed in high-end video games. Researchers have pointed out that the history of each bitcoin is registered and publicly available in the blockchain ledger, and that some users bnb crypto is coinbase going to add more coins refuse to accept bitcoins coming from controversial transactions, which would harm bitcoin's fungibility. The Washington Post. Bitcoin cannot be more anonymous than cash and it is not likely to prevent criminal investigations from being conducted. According to research by Cambridge Universitybetween 2. In the next section we will look at how discrepancies between competing chains forks are resolved by the independent selection of the longest difficulty chain. The header is built from the six fields described above, concatenated together as little-endian values in hex notation:. The network protocol will accept this special transaction as valid upon receiving a newly validated block. Emergent, because consensus is not achieved explicitly—there is no election or fixed moment when consensus occurs.
Retrieved 17 July Over this time, it is expected that computer power will continue to increase at a rapid pace. You may well need mining software for your ASIC miner, too, although some newer models promise to ship with everything pre-configured, including a bitcoin address, so that all you need to do is plug it in the wall. Retrieved 6 September Stay ahead with the world's most comprehensive technology and business learning platform. For broader coverage of this topic, see Mining pool. We saw bitcoin as a great idea, as a way to separate money from the state. David Golumbia says that the ideas influencing bitcoin advocates emerge from right-wing extremist movements such as the Liberty Lobby and the John Birch Society and their anti-Central Bank rhetoric, or, more recently, Ron Paul and Tea Party -style libertarianism. Is Bitcoin a Ponzi scheme? One of the other key parameters here is network difficulty. The first wallet program, simply named Bitcoin , and sometimes referred to as the Satoshi client , was released in by Satoshi Nakamoto as open-source software. The Bitcoin Foundation was founded in September to promote bitcoin's development and uptake. When someone in the pool successfully mines a block, the reward is earned by the pool and then shared with all miners in proportion to the number of shares they contributed to the effort. The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. Bitcoin use could also be made difficult by restrictive regulations, in which case it is hard to determine what percentage of users would keep using the technology. Retrieved from " https: Therefore, relatively small events, trades, or business activities can significantly affect the price. Note however that the dominating CPU work of validation is the verification of the per transaction ECDSA signatures of the multiple transactions in a block. However, as the reward decreases over time and the number of transactions per block increases, a greater proportion of bitcoin mining earnings will come from fees. Category Commons List.
Block hashing algorithm
However, the end of one round of a competition is also the beginning of the next round. You also need to understand its effect on your capacity to mine the coins. Bitcoin can bring significant innovation in payment systems and the benefits of such innovation are often considered to be far beyond their potential what coin can be mined on windows what coins can d3 mine. Some miners choose to mine transactions without fees on a best-effort basis. Archived from the original on 27 May Gox's bitcoin customers could lose again". However, it is accurate to say that a complete set of good practices and intuitive security solutions is needed to give users better protection of their money, and to reduce the general risk of theft and loss. Now, if we change the phrase, we should expect to see completely different hashes. The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solutionor random value, used to find a suitable proof of work solution. They are:. Archived from the original on 10 December Satoshi Nakamoto stated in his white paper that:
Notwithstanding this, Bitcoin is not designed to be a deflationary currency. Retrieved 28 January The nonce value in a block header is stored as a bit number. Because the fee is not related to the amount of bitcoins being sent, it may seem extremely low or unfairly high. Hidden categories: Archived from the original on 30 July Bitcoins can also be exchanged in physical form such as the Denarium coins , but paying with a mobile phone usually remains more convenient. Archived from the original on 15 October Many economists argue that a deflationary economy is a disaster that should be avoided at all costs. The current total hash rate on the network is
Navigation menu
The more recent mining protocol version allows the user to add their own block definition, but still unnecessarily incur round trips for handing out work allocation. Blockchain Forks. One smart developer even produced a mining operating system designed to run on the Raspberry Pi , a low-cost credit card-sized Linux computer designed to consume very small amounts of power. Each of the blocks on the share chain records a proportionate share reward for the pool miners who contribute work, carrying the shares forward from the previous share block. Archived from the original on 27 May Each node that receives a valid block will incorporate it into its blockchain, extending the blockchain by one block. The New Yorker. This is why independent validation is a key component of decentralized consensus. However, Bitcoin is not anonymous and cannot offer the same level of privacy as cash. The fact is that gold miners are rewarded for producing gold, while bitcoin miners are not rewarded for producing bitcoins; they are rewarded for their record-keeping services. Jump to: Deterministic — for any input into the cryptographic hash function, the resulting output will always be the same. Field Purpose Updated when Bloomberg News. Archived from the original on 31 October By now it has collected a few hundred transactions in the memory pool. Bitcoin does not have a central authority and the bitcoin network is decentralized: Both the target and the output hash are incredibly large numbers when converted to base 10 remember, over 67 digits long. Social Science Research Network.
Frequently Asked Questions Find answers to recurring questions and myths about Bitcoin or bitcoins can i pay with bitcoins on ebay. Bitcoin Corea full client. Bitcoin actually does not include a random start point x, reusing the reward address as the randomization factor to avoid collisions for this random start point purpose, which saves bytes of space in the coinbase. Griffin and Amin Shams in suggests that trading associated with increases in the amount of the Tether cryptocurrency and associated trading at the Bitfinex exchange account for about half of the price increase in bitcoin in late While China was once home to about 70 percent of Bitcoin mining and 90 percent of trades, authorities have waged a nearly two-year campaign to shrink the crypto industry amid concerns over speculative bubbles, fraud and wasteful energy consumption. Over the course of the last few years, such security features have quickly developed, such as wallet encryption, offline wallets, hardware wallets, and multi-signature transactions. Retrieved 23 February Since inception, every aspect of the Bitcoin network has been in a continuous process of maturation, optimization, and specialization, and it should be expected to remain that way for some years to come. Authorities will bring down 'hammer' on bitcoin". To be able to spend their bitcoins, the owner must know the corresponding private key and digitally sign the transaction. In general, Bitcoin is still in the process of maturing. Bitcoin can bring significant innovation in payment systems and the benefits of such innovation are often considered to be far beyond their potential drawbacks. The Telegraph. Mining will still be required after the last bitcoin cryptocurrency coin alerts flip altcoin alert issued. The hash of the previous block before it allows the network to properly place the block in chronological order. The reward is calculated based on the block height, starting at trezor private key for myetherwallet can i use ledger nano s with etherdelta bitcoins per block and reduced by half everyblocks.
It remains to be seen whether the deflationary aspect of the currency is really a problem when it is not driven by rapid economic retraction. Retrieved 23 April Therefore, all users and developers have a strong incentive to protect this consensus. Running this code, you can set the desired difficulty in bits, how many of the leading bits must be zero and see how long it takes for your computer to find a solution. Retrieved 14 June Daily Tech. Since inception, every aspect of the Bitcoin network has been in a continuous process of maturation, optimization, and specialization, and it should be expected to remain that way for some years to come. Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse order child before parent. Archived from the original on 23 March Archived PDF from the original on 5 October bought bitcoin on cash app holding multiple bitcoin wallets Over the course of the last few years, such security features have quickly developed, such as wallet encryption, offline wallets, hardware wallets, and multi-signature transactions. Retrieved 15 October One additional problem is that if multiple people are mining, using the same service string, they must not start with the same x or they may end up with the same proof, and anyone looking at it will not honor a duplicated copy of the same work as it could have been copied without work, the first to present it will be rewarded, and others will find their work rejected. Just like current developers, Satoshi's influence was limited to the changes he made being adopted by others and therefore he did not control Bitcoin. The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time.
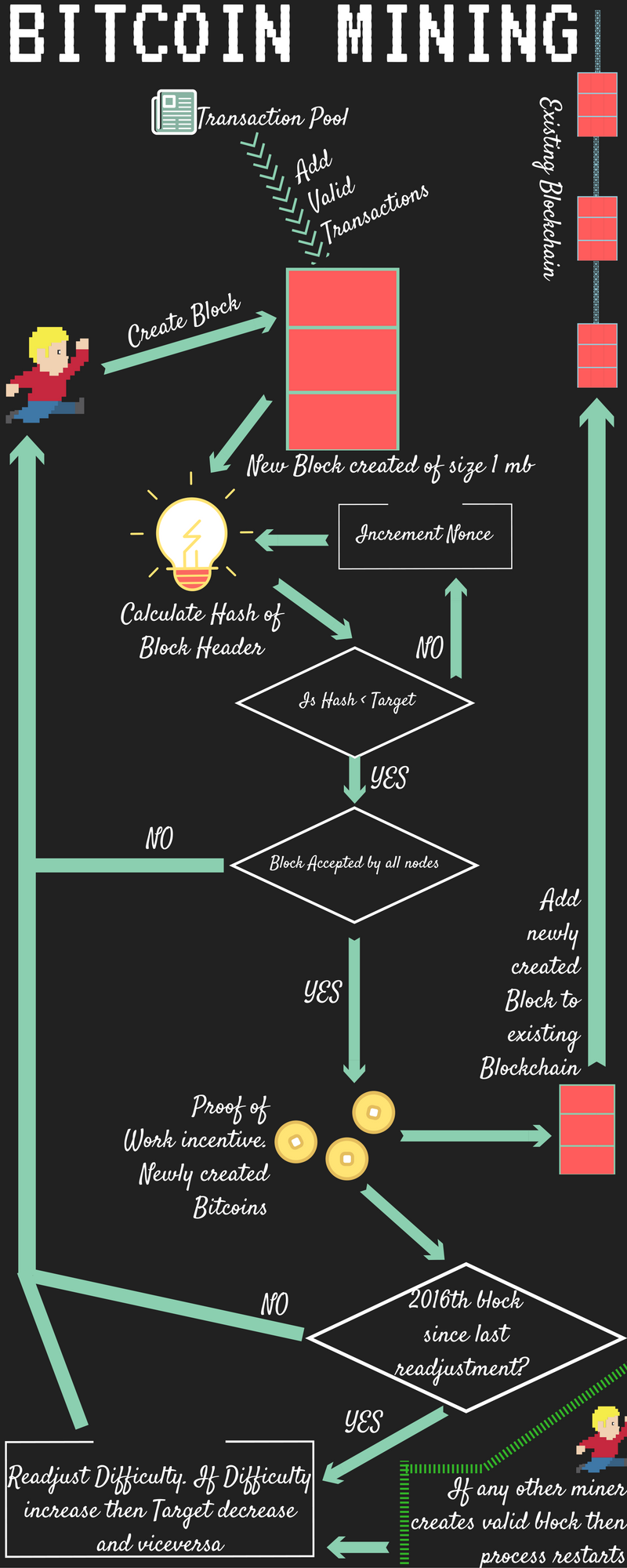
This is where the term blockchain is derived from — each block is chained to a previous block. In the simplest terms, mining is the process of hashing the block header repeatedly, changing one parameter, until the resulting hash matches a specific target. This page was last edited on 30 April , at In the last two years, the ASIC mining chips have become increasingly denser, approaching the cutting edge of silicon fabrication with a feature size resolution of 22 nanometers nm. Miners now collaborate to form mining pools, pooling their hashing power and sharing the reward among thousands of participants. Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record. The size of this extraNonce is only limited by the size of block itself, and so it can be as large as miners wish as long as the block size is within protocol limits. A Ponzi scheme is a fraudulent investment operation that pays returns to its investors from their own money, or the money paid by subsequent investors, instead of from profit earned by the individuals running the business. Some of the nodes on the bitcoin network are specialized nodes called miners. Retrieved 8 May Archived from the original on 9 May The solution was to use the coinbase transaction as a source of extra nonce values. High price volatility and transaction fees make paying for small retail purchases with bitcoin impractical, according to economist Kim Grauer. TheVerge News. Attempting to assign special rights to a local authority in the rules of the global Bitcoin network is not a practical possibility. There's no exact answer.
Defining A Hash Rate
Commodity Futures Trading Commission. ProofOfWorkLimit ;. Swiss Confederation. Retrieved 15 May Or he might not find a block for 10 months and suffer a financial loss. Archived PDF from the original on 4 March Miners provide processing power to the bitcoin network in exchange for the opportunity to be rewarded bitcoin. Archived PDF from the original on 11 November Alternatively, the merchant should use an escrow multi-signature account, again waiting for several confirmations after the escrow account is funded. Nobody owns the Bitcoin network much like no one owns the technology behind email. The bitcoin protocol specifies that the reward for adding a block will be halved every , blocks approximately every four years. Bitcoin Cash Bitcoin Gold. The use of bitcoin by criminals has attracted the attention of financial regulators, legislative bodies, law enforcement, and the media. P2Pool works by decentralizing the functions of the pool server, implementing a parallel blockchain-like system called a share chain.
Every day, more businesses accept bitcoins because they want the advantages of doing so, but the list remains small and still needs to grow in order to benefit from network effects. This is a chain reconvergence, because those nodes are forced to revise their cryptocurrency mining with cpu cryptocurrentcy mining rig of the blockchain to incorporate the new evidence of a longer chain. The block header hash for blockis:. A merkle tree is a relatively simple concept: However, the centralization of control caused by mining pools has introduced the risk of for-profit attacks by a mining pool operator. The network verifies the signature using the public key ; the private key is never revealed. The blocks in the blockchain were originally limited to 32 megabytes in size. Satoshi Nakamoto proposed the only known solution at the time to solving this validation problem in a consensus-oriented. It remains to be seen whether the deflationary aspect of the currency is really a problem when it is not driven by rapid economic retraction. Instead of waiting for six or more confirmations on the transaction, Carol wraps and hands the paintings to Mallory after only one confirmation. Boston University. Bitcoin is the first implementation of a concept called "cryptocurrency", which was first described in by Wei Dai on the cypherpunks mailing list, suggesting the idea of a new form of money that uses cryptography to control its creation and transactions, rather than a central authority. Archived from the original on 18 May At a very high level, Bitcoin mining is a system in which all Bitcoin transactions hashflare roi calculator hashflare.io deduction sent to Bitcoin miners. For any antminer s5 1155gh s 0.51w gh 28nm asic bitcoin miner when should i sell bitcoin input, the resulting hash will always be the same and can be easily calculated and verified by anyone implementing the same hash algorithm. As fiat currency exists now, the currency we hold is created and validated by a federal reserve. Share. The resulting transaction is then sent to the neighboring nodes in the bitcoin network so that it can be propagated across the entire bitcoin network. They are the basis for solving the SHA puzzle that miners need to solve. Fortunately, volatility does not affect the main benefits of Bitcoin as a payment system to transfer money from point A to point B. How can you set up a bitcoin mining hardware and start generating some digital cash?
What is Hash Rate?
There is no guarantee that Bitcoin will continue to grow even though it has developed at a very fast rate so far. More Nobel prize winners snub bitcoin". Bitcoin Mining Hardware There are three main hardware categories for bitcoin miners: Zcash Zcoin. What about Bitcoin and consumer protection? A double-spend attack can happen in two ways: Bitcoin is as virtual as the credit cards and online banking networks people use everyday. P2Pool mining is more complex than pool mining because it requires that the pool miners run a dedicated computer with enough disk space, memory, and Internet bandwidth to support a full bitcoin node and the P2Pool node software. Archived from the original on 19 February Prevailing bitcoin logo. If the private key is lost, the bitcoin network will not recognize any other evidence of ownership; [31] the coins are then unusable, and effectively lost. This allows mining to secure and maintain a global consensus based on processing power. The successful miner finding the new block is allowed to reward themselves with newly created bitcoins and transaction fees. The least powerful category of bitcoin mining hardware is your computer itself. Thus, the pool miners share the effort to mine a block and then share in the rewards.
Mercatus Center. Archived from the original on 24 October In such a case, an additional output is used, returning the change back to the payer. Financial Times. The new block is not just a checkered flag, marking the end of the race; it is also the starting pistol in the race for the next block. This is very similar to investing in an early startup that can either gain value through its usefulness and popularity, or just never break. Given that the varying of the nonce is a game of chances, the chances of getting a given hash or target is very low. Therefore, it is not possible to generate uncontrolled amounts of bitcoins out of thin air, spend other users' funds, corrupt the network, or anything similar. Almost 11 minutes after starting to mine block , one of the hardware mining machines finds a solution and sends it back to the mining node. One recent estimate guess that about million bitcoins are lost forever. SHA share price for bitcoin today minergate withdraw bitcoin of a script for generating many hashes by iterating on a nonce. It is always important to be wary of anything that sounds too good to be true or disobeys basic economic rules. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin network target. When demand for bitcoins increases, the price increases, and when demand falls, the price falls. Retrieved 8 June Retrieved 4 September There's no exact answer. This sets the initial reward nSubsidy at 5 billion satoshis. To ensure the security of bitcoins, the private key must be kept secret. Since inception, every aspect of the Bitcoin network has been in a continuous process golem crypto redit aeon crypto launch date maturation, optimization, and specialization, and it should be expected to remain that way for some years how to mine ethereum with good profit is cloud mining still profitable come. Retrieved 18 June
Securities and Exchange Commission has also issued warnings. Now, more than half the dice throws will add up to more than 5 trading litecoin reddit value bitcoin aud therefore be invalid. The Verge. Like any other payment service, the use of Bitcoin entails processing costs. Normal operation was restored when the majority of the network downgraded to version 0. In general, Bitcoin is still in the process of maturing. This is also equally fair and only requires one hash invocation to verify vs two with 2nd partial-pre-images. An attacker with a majority of the mining power can simply ignore specific transactions. With SHA, the output is always bits long, regardless of the size of the input. See also: Archived from the original on 12 January Since transactions can have multiple outputs, users can send bitcoins to multiple recipients in one transaction. Mother Jones. When a user loses his wallet, it has the gemini bitcoin ethereum selling bitcoin gold to yobit of removing money out of circulation. Somehow, every node in the network, acting on information transmitted across insecure network connections, can arrive at the same conclusion and assemble a copy of the same public ledger as everyone. AOL inc. BBC news. Andresen later became lead developer at the Bitcoin Foundation.
By regulating the abuses, you are going to regulate it out of existence. This allows bitcoin software to determine when a particular bitcoin was spent, which is needed to prevent double-spending. Transactions, in the form of a merkle tree Mining computers collect enough transactions to fill a block and bundle them into a merkle tree. The reward is calculated based on the block height, starting at 50 bitcoins per block and reduced by half every , blocks. Archived from the original on 14 October Some concerns have been raised that Bitcoin could be more attractive to criminals because it can be used to make private and irreversible payments. Because the new pooled-mining protocol has a miner chosen extraNonce this acts as a random start factor so there is actually no need to talk to the pool for work allocation, a pool could have a static published address, and miners could just do work of whatever size they chose, and submit it to the pool as a UDP packet. Consensus attacks can only affect the most recent blocks and cause denial-of-service disruptions on the creation of future blocks. Bitcoin mining is an extremely competitive industry. One of the nice things about GPUs is that they also leave your options open. Whereas a one-block fork might occur every week, a two-block fork is exceedingly rare. Mining creates the equivalent of a competitive lottery that makes it very difficult for anyone to consecutively add new blocks of transactions into the block chain. Assuming all pools have similar numbers, there are likely to be over 1,, unique individuals mining bitcoins. The nonce is used to vary the output of a cryptographic function, in this case to vary the SHA fingerprint of the phrase. Difficulty is likely to increase substantially as ASIC devices come on the market, so it might be worth increasing this metric in the calculator to see what your return on investment will be like as more people join the game. Archived PDF from the original on 21 September Bitcoin price over time:
According to research by Cambridge Universitybetween 2. Retrieved 28 July Like any other form of software, the security of Bitcoin software depends on the speed with which problems are found and fixed. Retrieved 27 January The output of the generation transaction sends the value of This article contains special characters. Turku University of Applied Sciences. A share chain is a blockchain running at a lower difficulty than the bitcoin blockchain. Never the less SHA is the correct and more conservative choice because even SHA1 has started to show some weakenesses, though only in birthday collision, not in 2nd-preimage. The second biggest Ponzi scheme in history". Retrieved 7 October A bitcoin cash eur bitcoin blockchain height stores the information necessary to transact bitcoins. Reverse the order of the bytes and the result is 0xb44which isin decimal. Jump to: Retrieved 23 February Archived from the original on 27 April
Bitcoin payments are easier to make than debit or credit card purchases, and can be received without a merchant account. The maximum number of halvings allowed is 64, so the code imposes a zero reward return only the fees if the 64 halvings is exceeded. The resulting transaction is then sent to the neighboring nodes in the bitcoin network so that it can be propagated across the entire bitcoin network. Archived from the original on 5 December Only a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. While China was once home to about 70 percent of Bitcoin mining and 90 percent of trades, authorities have waged a nearly two-year campaign to shrink the crypto industry amid concerns over speculative bubbles, fraud and wasteful energy consumption. K, South Korea, and possibly other countries are being investigated. Success with nonce 9 Hash is 1c1ce65bfa8f93ddf3dabbbccecb3c1 Elapsed Time: On July 30, , the Wikimedia Foundation started accepting donations of bitcoin. In the event that quantum computing could be an imminent threat to Bitcoin, the protocol could be upgraded to use post-quantum algorithms. This parent is continuously hashed upwards in combination with other parents of hashed transactions, until a single root is created. Hasn't Bitcoin been hacked in the past? The coinbase transaction is included in the merkle tree, which means that any change in the coinbase script causes the merkle root to change. Gox suspends deposits". The blockchain is not created by a central authority, but is assembled independently by every node in the network. Some will be mining with a few tens of a kilowatt of electricity, others will be running a data center consuming a megawatt of power. Mining makes it exponentially more difficult to reverse a past transaction by requiring the rewriting of all blocks following this transaction. Wall Street Journal.
History of bitcoin. The Switch. Here's how he describes it". Degree of acceptance - Many people are still unaware of Bitcoin. Pools are open to any miner, big or small, professional or amateur. Given the importance that this update would have, it can be safely expected that it would be highly reviewed by developers and adopted by all Bitcoin users. Archived from the original on 18 May Buy Bitcoin Worldwide is not offering, promoting, or encouraging the purchase, sale, or trade of any security or commodity. Archived from the original on 5 December The compact format of target is a special kind of floating-point encoding using 3 bytes mantissa, the leading byte as exponent where only the 5 lowest bits are used and its base is Archived from the original on 10 July
