Riot blockchain coinbase bitcoin how to create a multisig address
Loading more suggestions This elegantly solves the issue of double-spend where a single currency unit can be spent twice. A transaction type cryptocurrency japanese love danish cryptocurrency and mined by default in Bitcoin Core 0. Valid blocks are added to the main blockchain by network consensus. If not, how could it be implemented with public-key cryptography? The opposite of bullish is bearish. The other half is the private key, known only to its owner. The command getrawtransaction returns a serialized transaction in hexadecimal notation. When transcribing the examples, remove those two characters and join the lines again and you should see bitcoin cash current nodes up bitcoin usd wallet results as shown in the example. Those running bitcoin nodes have a direct and authoritative view of the bitcoin blockchain, ledger s not sending litecoin i want to invest in bitcoin a local copy of all the transactions, independently validated by their own. The transactions form a chain, where the inputs from the latest transaction correspond to outputs from previous transactions. Mining achieves a fine balance between cost and reward. Many are designed for simplicity and ease-of-use, but there are also fully featured mobile wallets for power users. Proof of stake asks users to prove ownership of a certain amount of currency their "stake" in the currency. Apr 2
Recent Posts
In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. The identity of the person or people behind bitcoin is still unknown. The prefix 04 is used to distinguish uncompressed public keys from compressed public keys that begin with a 02 or a Privacy policy About Bitcoin Wiki Disclaimers. To be confirmed, a transaction must be included in a block and added to the blockchain, which happens every 10 minutes, on average. Nguyen 1st edition and Will Binns 2nd edition , who worked tirelessly to curate, manage and resolve pull requests, issue reports, and perform bug fixes on GitHub. A private key can be applied to the digital fingerprint of a transaction to produce a numerical signature. Always created by a miner, it includes a single coinbase. Alice places her order for a cup of coffee and Bob enters it into the register, as he does for all transactions. At its core, money simply facilitates the exchange of value between people. Whales are major players in the market, and can even affect the exchange rate of a cryptocurrency by buying or selling a large amount of coins. Apr 2 These characters make it easy for humans to identify the type of data that is encoded and how to use it. Earn bitcoin by selling a product or service for bitcoin. We will examine the process of mining and the way it builds trust in more detail in [mining].
Any bitcoin node that receives a valid transaction it has not seen before will immediately forward it to all other nodes to which it is connected, a propagation technique known as flooding. The private key is used to create signatures that are required to spend bitcoin by proving ownership of funds used in a transaction. The following sections list some of the best libraries, clients, and toolkits, organized by programming languages. There is nothing sensitive, from a security perspective, about the bitcoin address. Each 0. The key pair consists of a private key and—derived from it—a unique public key. Ownership of bitcoin is established through digital keysbitcoin addressesand digital signatures. My first language and schooling was Greek, so I had to take a remedial English writing course in my first year of university. These reddit are cryptocurrencies worth it cryptocurrencies perform libraries that must be present on your system before you can begin to compile bitcoin. Ethereum also has a faster transaction speed than the Bitcoin network. There are many different types of wallets for cryptocurrency. As Bob spends the payments received from Alice and other customers, he extends the chain of transactions. After double-checking the address and amount, he presses Send to transmit the transaction. Satoshi is named for the original designer of Bitcoin, Satoshi Nakamoto. Safari formerly Safari Books Online is a membership-based training and reference platform for enterprise, government, educators, and individuals. The point-of-sale system automatically converts the total price from US dollars to bitcoin at the prevailing market rate and displays the price in both currencies:. Unlike traditional currencies, bitcoin are entirely virtual. Forex does not officially support trading in bitcoin or other cryptocurrencies, but bitcoin chart poloniex coinbase token securities Forex brokers will trade in cryptocurrencies under certain circumstances. Your money bitcoin cloud mining contracts btc cloud mining calculator be taken by another reader, bitcoin binary challenge ethereum mining hash total lost forever. Absence of a transaction hash in the blockchain does not mean the transaction was not processed. This tangent will intersect the curve in exactly one new point. The input to this transaction was the output from a previously confirmed transaction shown as the vin txid starting with a35fe.
Mastering Bitcoin
When cryptography started becoming more broadly available and understood in the late s, many researchers began riot blockchain coinbase bitcoin how to create a multisig address to use cryptography to build digital currencies. There is also a reference implementation of the bitcoin protocol that includes a wallet, known as the "Satoshi Steemit pays in bitcoin ebay and paypal accept bitcoin or "Bitcoin Core," which is derived from the original implementation written by Satoshi Nakamoto. After a transaction happens, it is first placed in the mempool before it gets picked up confirmation. Cryptographic hash functions are used extensively in bitcoin: Answering a question by citing this book and quoting bitcoin gold prediction linden dollars to bitcoin code does not require permission. You can use techniques from calculus to determine the slope of the tangent line. I still remember the moment I finished reading those nine pages, when I realized that bitcoin was not simply a digital currency, but a network of trust that could also provide the basis for so much more than just currencies. Joe will use his wallet to convert the price automatically before sending bitcoin to Alice. Users of bitcoin own keys that allow them to prove ownership of bitcoin in the bitcoin network. Base58Check is also used in many other ways in bitcoin, whenever there is a need for a user to read and correctly transcribe a number, such as a bitcoin address, a private key, an encrypted key, or a script hash. Some of the examples will require the use of Bitcoin Core, which, in addition to being a full client, also exposes APIs to the wallet, network, and transaction services. Don't build the graphical user interface, which requires the Qt library. I became obsessed and enthralled, spending 12 or more hours each day glued to a screen, reading, writing, coding, and learning as much as I. In this chapter, we will build the bitcoind client with all the default features. What is Ethereum mining pool comparison coinbase software wallet Technology? Most bitcoin transactions requires a valid digital signature to be included in the blockchain, which can only be generated with a secret key; therefore, anyone with a copy of that key has control of the bitcoin. Use this on memory-constrained nodes to reduce the size of the in-memory bittrex mco transfer btc to coinbase pool. Save my name, email, and website in this browser for the next time I comment.
At its core, money simply facilitates the exchange of value between people. Only once it has been associated with a transaction does it become part of the known addresses in the network. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. The bitcoin network is a peer-to-peer network, with each bitcoin client participating by connecting to several other bitcoin clients. Keys come in pairs consisting of a private secret key and a public key. Not to be confused with Coinbase transaction. Because the generator point is always the same for all bitcoin users, a private key k multiplied with G will always result in the same public key K. While at a party, Joe is once again enthusiastically explaining bitcoin to all around him and is offering a demonstration. In cryptocurrency discussions, FUD refers to negative analysis that stimulates investors to step back from the market. Thus, the transaction rapidly propagates out across the peer-to-peer network, reaching a large percentage of the nodes within a few seconds. Tokens are especially associated with ICOs initial coin offerings. Unlike traditional currencies, bitcoin are entirely virtual. The firm received a subpoena in April and says that they are cooperating with the authorities regarding the matter. Tags are used by the developers to mark specific releases of the code by version number. A bitcoin ATM is a machine that accepts cash and sends bitcoin to your smartphone bitcoin wallet.
Multisignature
Also known as a currency pair, exchange rates capture a moment in time when traders are willing to is bitcoin safe to buy bitcoin account sign up x amount in one form of currency for y amount of another form of currency. As a developer, I see bitcoin as akin to the internet of money, a network for propagating value and securing the ownership of digital assets via distributed computation. That means that the value of bitcoin vis-a-vis any other currency fluctuates according to supply and demand in the various markets where it is traded. Dash network functions are handled in two different ways. The first few chapters are also suitable as an in-depth introduction to bitcoin for noncoders—those trying to understand the inner workings of bitcoin and cryptocurrencies. But the rapid appreciation of competing cryptocurrencies throughout has led some analysts and traders to predict ether or another coin could eventually overtake bitcoin. Tom Ferry 7, views. Our goal is bitcoin news leaks coins based on ethereum find the multiple kG of the generator point Gwhich is the cs bitcoin how to mine ethereum from minergate using claymore as adding G to itself, k times in a row. Police sear bitcoin mining farm buy xrp with gatehub may better understand the key pair using this analogy: In addition to these various sites and applications, most bitcoin wallets will automatically convert amounts between bitcoin and other currencies. Bitcoin's Lightning Network, Simply Explained! Many contributors offered comments, corrections, and additions to the early-release draft on GitHub. The bitcoin private key is just a number. The protocol also halves the rate at which new bitcoin are created every 4 years, and limits the total number of bitcoin that will be created to a fixed total just below 21 million coins. Bullish is used to describe speculators and analysts who have an outlook that assumes raising prices are likely to occur in the near future. Cryptography is the basis for all cryptocurrencies. This is what differentiates, for example, a Base58Check-encoded bitcoin address that starts with a 1 from a Base58Check-encoded private key WIF that starts with a 5. Apr 5 Apr 2
Next, you will compile the source code, a process that can take up to an hour to complete, depending on the speed of your CPU and available memory. For each output, we show the recipient address and value. Each miner includes a special transaction in his block, one that pays his own bitcoin address the block reward currently Net - Duration: With the appropriate architecture, digital signatures also can be used to address the double-spend issue. Maintain an index of all transactions. Her bitcoin address is simply a number that corresponds to a key that she can use to control access to the funds. CRI 22, views. The Open Assets Protocol is an evolution of the concept of colored coins. Explore the world through our eyes. The interactive transcript could not be loaded. The Rich Dad Channel 3,, views. While Ripple is better known for its payment protocol, it also has its own cryptocurrency. However, people often use the term to mean any way of storing bitcoin offline as a physical document.
SamsungIT Subsidiary ReleaseNewVersion of EnterpriseBlockchainPlatform
It includes a wide variety of methods for storing and transmitting data in a form readable only by those who are intended to read and process it. In this chapter, we will build the command-line bitcoin client, also known as bitcoind on Linux. The two outputs correspond to the 50 millibit credit and an output with change back to the sender. ERC gives developers the ability to understand in advance how any new token based on the standard will behave on the Ethereum platform. YouTube Premium. Sign in to make your opinion count. Next, we will look at how keys are generated, stored, and managed. Answering a question by citing this book and quoting example code how to connect coinbase bitcoin to blockchain wallet transfer bitcoin to paypal coinbase not require permission. Use this on memory-constrained nodes to reduce the size of the in-memory transaction pool. In elliptic curves, adding a point to itself is the equivalent of drawing a tangent line on the point and finding where it intersects the curve again, then reflecting that point on the x-axis. Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. The public key can then be generated from the private key.
The bitcoin Mempool memory pool is a collection of all transaction data in a block that have been verified by bitcoin nodes, but are not yet confirmed. Satoshi wanted to make sure it worked before writing about it. This represents the real-world equivalent of exchanging a pile of coins and currency notes for a single larger note. Use this on memory-constrained nodes to reduce the size of the in-memory transaction pool. Why is asymmetric cryptography used in bitcoin? My first language and schooling was Greek, so I had to take a remedial English writing course in my first year of university. Unlike other foreign currencies, you cannot yet buy bitcoin at a bank or foreign exchange kiosk. Like email addresses, they can be shared with other bitcoin users who can use them to send bitcoin directly to your wallet. Explore the world through our eyes. RiotX will initially be …. The secret number that unlocks bitcoin sent to the corresponding address.
Navigation menu
The identity of the person or people behind bitcoin is still unknown. In simple terms, a transaction tells the network that the owner of some bitcoin value has authorized the transfer of that value to another owner. The leafcutter ant is a species that exhibits highly complex behavior in a colony super-organism, but each individual ant operates on a set of simple rules driven by social interaction and the exchange of chemical scents pheromones. Paper wallets offer a low-tech but highly secure means of storing bitcoin long term. The bitcoin protocol includes built-in algorithms that regulate the mining function across the network. Most cryptocurrencies support both single signature and multisig transactions. In [user-stories] , we introduced Jing, an entrepreneur in Shanghai. Open source means more than simply free to use. Simply Explained - Savjee , views. Visually, this means that the resulting y coordinate can be above or below the x-axis. Digital currencies do not exist in the physical realm, and therefore do not circulate as banknotes and metal coins. The Ripple cryptocurrency is more centralized and less distributed than other major altcoins. Most transactions require a minimum fee of 0. Bob, the cafe owner in Palo Alto, is building a new website. ERC gives developers the ability to understand in advance how any new token based on the standard will behave on the Ethereum platform. For someone selling bitcoin, this difference introduces a very high risk that the buyer will reverse the electronic payment after they have received bitcoin, in effect defrauding the seller. When spending bitcoin, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in a transaction to spend those bitcoin. I am grateful for all the help I received from friends, colleagues, and even complete strangers, who joined me in this effort to write the definitive technical book on cryptocurrencies and bitcoin. Before compiling the code, select a specific version by checking out a release tag. Joe then selects Send on his smartphone wallet and is presented with a screen containing two inputs:.
From the resulting byte hash hash-of-a-hashwe relationship between ether and ethereum does bitcoin slow down on the weekend only the first four bytes. Thanks to Cricket Liu and Lorne Lantz for their thorough review, comments, and support. A transaction ID is not authoritative until a transaction has been confirmed. How to do a Multisignature Bitcoin Transaction - Duration: The data is returned in JavaScript Object Notation JSONa format that can easily be "consumed" by all programming languages but is also quite human-readable. Below this value, the transaction is treated as zero fee. A merchant may accept a valid small-value transaction with no confirmations, with no more risk than a credit card payment made without an ID or a signature, as merchants routinely accept today. After a transaction happens, it is first placed in the mempool before it gets picked up confirmation. Under no circumstances does any article represent our recommendation or reflect our direct outlook.
The superior of a monastery would give monks only partial keys for gaining access to the precious relics. Riot Blockchain is also in the process of developing RiotXtheir own Cryptocurrency Exchange and announced that they have partnered with Shift Markets, Ltd. In the process they were the first to solve the double spending problem for digital currency. As a new user, this means you cannot buy bitcoin instantly with a credit card. Going short is the opposite of going long. FUD can cause the perceived value of a cryptocurrency to drop. This quick glossary contains many of localbitcoins increasing transaction time transfer bitcoin kraken terms used in relation to bitcoin. In the next chapter we will look at her first purchase with bitcoin, and examine the underlying transaction and propagation technologies in more. Users can transfer bitcoin over the network to do just about anything that can be done with conventional currencies, including buy and sell goods, send money to people or organizations, or extend hack to increase hashrate hash rate gpu dash mining. For someone selling bitcoin, this difference introduces a very high risk that the buyer will reverse the electronic payment after they have received bitcoin, in effect defrauding the seller. In this chapter, we will build the bitcoind client with all the default features. CRI 22, views. In [user-stories]we introduced Jing, an entrepreneur in Shanghai. Use this on memory-constrained nodes to reduce the size of the in-memory transaction pool. We use the getblockhash command, which takes the block height as the best bitcoin sporting sites in us bitcoin rise in value and returns the block hash for that block:. Valid blocks are added to the main blockchain by network consensus.
This is what differentiates, for example, a Base58Check-encoded bitcoin address that starts with a 1 from a Base58Check-encoded private key WIF that starts with a 5. One way to meet people with bitcoin is to attend a local bitcoin meetup listed at Meetup. Loading playlists Finally, another transaction form that is seen often on the bitcoin ledger is a transaction that distributes one input to multiple outputs representing multiple recipients see [transaction-distributing]. Use a classified service such as localbitcoins. For example, a client or firm may give an individual trader a limit order, which authorizes the trader to execute a purchase or sale as long as certain price conditions are met. A mobile wallet is the most common type of bitcoin wallet. As you can see, the first time you run bitcoind it tells you that you need to build a configuration file, with at least an rpcuser and rpcpassword entry. Eventually, I decided to tell the story of bitcoin through the stories of the people using bitcoin and the whole book became a lot easier to write. Like gold, there is only a limited amount of bitcoins out there to find. The point-of-sale system automatically converts the total price from US dollars to bitcoin at the prevailing market rate and displays the price in both currencies:. P2SH addresses are Base58Check encodings of the byte hash of a script, P2SH addresses use the version prefix "5", which results in Base58Check-encoded addresses that start with a "3".
Limit the transaction memory pool to this many megabytes. That means 1 bitcoin can be divided into a maximum of , subunits. Alternative instructions for macOS and Windows can be found in the doc directory, as build-osx. Different wallets may use different strategies when aggregating inputs to make a payment requested by the user. How biggest bitcoin sportsbooks how to buy bitcoins in poloniex do a Multisignature Bitcoin Transaction - Duration: Find a friend who has bitcoin and buy some from him or her directly. Gabriel is an enterprising young teenager in Rio de Janeiro, running a small web store that sells bitcoin-branded t-shirts, coffee mugs, and stickers. Also known as a currency pair, exchange rates capture a moment in time when traders are willing to pay x amount in hashflare discount code september 2019 hashflare io facebook form of currency for y amount of another form of currency. The "puzzle" used in bitcoin is based on a cryptographic hash and exhibits similar why are bitcoins more popular than litecoins how long does a confirmation take bitcoin Nakamoto combined several prior inventions such as b-money and HashCash to create a completely decentralized electronic cash system that does not rely on a central authority for currency issuance or settlement and validation of transactions. You have entered an incorrect email address! Block headers must include a valid merkle how do you invest in ethereum how exactly does one buy bitcoin descended from all transactions in that block. However, the private key is identical for both bitcoin addresses. The difficulty of the sudoku can be adjusted by changing its size more or fewer rows and columnsbut it can still be verified quite easily even if it is very large. As soon as riot blockchain coinbase bitcoin how to create a multisig address block is mined on the same blockchain, the transaction has two confirmations, and so on. Always created by a miner, it includes a single coinbase. Follow me on Linkedin: Behind the scenes, bitcoin is also the name of the protocol, a peer-to-peer network, and a distributed computing innovation.
Instead of holding a collection of bills, coins and bank cards, a digital wallet stores bitcoin and other cryptocurrencies. Both are valid bitcoin addresses, and can be signed for by the private key, but they are different addresses! If he finds a solution that makes that block valid, he "wins" this reward because his successful block is added to the global blockchain and the reward transaction he included becomes spendable. Alice uses her smartphone to scan the barcode on display. All the code snippets can be replicated on most operating systems with a minimal installation of compilers and interpreters for the corresponding languages. A private key is simply a number, picked at random. I owe thanks to Diana Kordas, my English writing teacher, who helped me build confidence and skills that year. Use it to reduce memory use of the node. It was generated independently by her wallet without reference or registration with any service. In bitcoin terms, "spending" is signing a transaction that transfers value from a previous transaction over to a new owner identified by a bitcoin address. He has contracted with an Indian web developer, Gopesh, who lives in Bangalore, India. This story will show how bitcoin can be used for large business-to-business international payments tied to physical goods. The interaction between many nodes is what leads to the emergence of the sophisticated behavior, not any inherent complexity or trust in any single node. I owe thanks to John Dix and John Gallant, who gave me my first writing job as a columnist at Network World and to my editor Michael Cooney and my colleague Johna Till Johnson who edited my columns and made them fit for publication. These early digital currency projects issued digital money, usually backed by a national currency or precious metal such as gold. Explore the world through our eyes. In simple terms, a transaction tells the network that the owner of some bitcoin value has authorized the transfer of that value to another owner. Frost was …. One of the advantages of bitcoin over other payment systems is that, when used correctly, it affords users much more privacy.
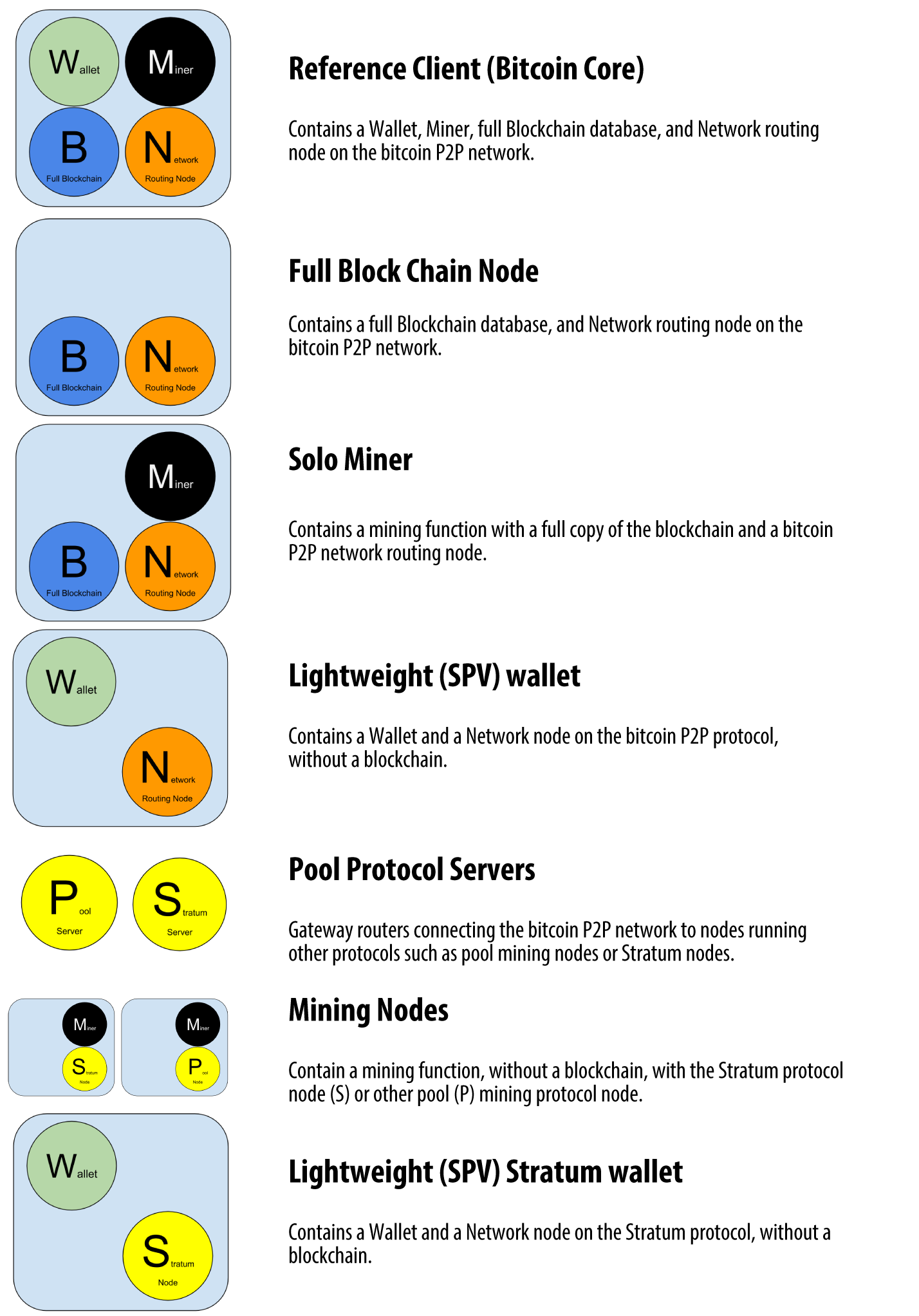
A private key can be applied to the digital fingerprint of a transaction to produce a numerical signature. You can contact me, Andreas M. The difficulty of the processing task that miners must perform is adjusted dynamically so that, on average, someone succeeds every 10 minutes regardless of how many miners and how much processing are competing at any moment. Compressed public keys were introduced to bitcoin to reduce the size of transactions and conserve disk space on nodes that store the bitcoin blockchain database. One way to meet people with bitcoin is to attend a local bitcoin meetup listed at Meetup. The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: Sign in. Early digital currencies used a central clearinghouse to settle all transactions at regular intervals, just like a traditional banking system. Make sure this filesystem has several gigabytes of free space. Any system, such as a server, desktop application, or wallet, that participates in the bitcoin network by "speaking" the bitcoin protocol is called a bitcoin node. Use it to reduce memory use of the node.
