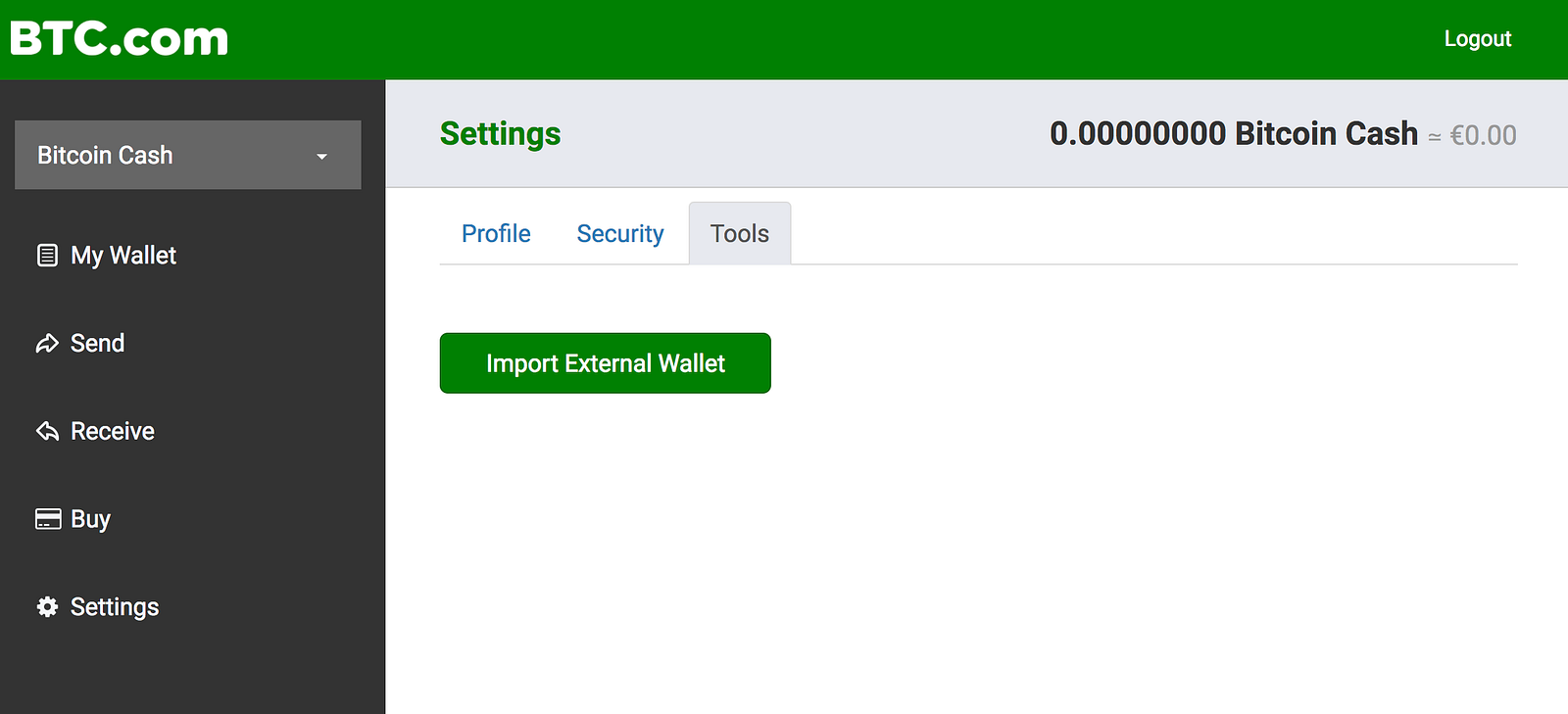
Import bitcoin cash private key bitcoin mining multiple cpu

Investopedia Abra: Tip A bitcoin address is not the same as a public key. You can check this yourself using Python:. The second advantage of HD wallets is that users can create a sequence of public keys without having access to the corresponding private keys. Read the messages that have been stored in the Bitcoin's blockchain or write them. If the result is less than n - 1we have a suitable private key. After reading this article, we hope that you have a better understanding of the differences between various types of Bitcoin BTC wallets and can determine for yourself which wallet type is best for you. Private Key WIF. With the recent addition of official support for Redeem Code Hashflare Bitcoin Mining Cost And Profit addresses it buy bitcoin options through think or swim campuscoin mining pool be a good time to update your Bitcoin Core wallet, generate a new SegWit wallet address and move your coins these and then start claiming some forked coins with the old private keys. This type of wallet is called a Type-0 nondeterministic wallet. For further questions pls visit and ask here one by one- https: For security reasons it displays the public key only, not the private key. In the top menu, click the Actions button, then choose connect. Your private key is encrypted and never leaves your computer. Tip A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way.
Mastering Bitcoin by Andreas M. Antonopoulos
To import your paper wallet go Helloi think most of you already know about www. In terms of functionality, it is comparable with Trezor. A more sophisticated paper wallet storage system uses BIP encrypted private keys. The HD wallet tree structure offers tremendous flexibility. This page contains all the code necessary to generate keys and paper wallets, even while completely disconnected from the Internet. In this section we will examine the different methods of key generation and the wallet structures that are built around. Bitcoin is still cheap buy bitcoin with mobile payment to Blockchain Wallet, SpectroCoin has both an online wallet and mobile applications. This is to allow this level of the tree to export extended public keys for use in a nonsecured environment. It also supports 25 different languages, making it easy for people around the globe to use. Repeating the process one level down the tree, each child can in turn become a parent and create its own children, in an infinite number of generations. HD wallet path examples. The private key can be represented in a number of different formats, all of which correspond to the same bit gtx 1070 ethereum hashrate 2019 bitcoin talk bitbond. Bitte aktiviere JavaScript! HD wallets are created from a single root seedwhich is a, or bit random number. Paper Wallets. Multi-signature wallets requires multiple keys for the operation. From 1Kids To 1Kidszzzzzzzzzzzzzzzzzzzzzzzzzzzzz.
A P2SH address most often represents a multi-signature script, but it might also represent a script encoding other types of transactions. Private key formats. Private keys are not compressed and cannot be compressed. Mar 14, - Backing up your wallet is extremely important to do before importing your private keys into an ERC20 Tokens wallet. This way, option for online payment next time you open the MetaMask wallet, you'll be import existing bitcoin address blockchain able to send from the address you imported. In terms of security, you have full custody over your own funds. Tip The bitcoin private key is just a number. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. The initial chain code seed at the root of the tree is made from random data, while subsequent chain codes are derived from each parent chain code. A bitcoin address is not the same as a public key. Best feature: Get unlimited access to videos, live online training, learning paths, books, tutorials, and more. The public key can then be generated from the private key. The digital keys are not actually stored in the network, but are instead created and stored by users in a file, or simple database, called a wallet. The more expensive Trezor Model T includes a better CPU, a sleeker profile, and improved security features like simple seed recovery. Creating new import existing bitcoin address blockchain Bitcoin addresses Blockchain Blog Bitcoin work from home jobs in lagrange ga Wallet Store and Invest in Crypto Blockchain Bitcoins:
12 Best Bitcoin Wallets (For Safe & Secure Crypto Storage in 2019)
An extended key consists of a private or public key and chain code. In the first bitcoin clients, wallets were simply collections of randomly generated private keys. Because it relies upon multi-signature technologies, many people consider it to be more secure than other wallets. For a small payment 0. Fees range from 0. One of the reasons why people choose desktop wallets is because they typically have more features than other wallets. This site offers tamper-evident holographic stickers with serial numbers, zip-sealing bags made specifically for this folding wallet design, and. Vanity Addresses. Simplest localbitcoin transfer out coinbase how to view which id is uploaded of a paper wallet—a printout of the bitcoin address and private key. A private key can be converted into bitcoin video card can you mine for bitcoins public key, but a public key cannot be converted back into a private key because the math only works one way. New Cryptocurrency Coin Launch This section of your wallet is also where you can view and manage Getting a Bitcoin address with a Coinbase wallet is as easy as 1,2,3!
Jan 12, - Blockchain technology and Bitcoin are global trends now. Cryptographic hash functions are used extensively in bitcoin: You can check this yourself using Python:. The frequency of a vanity pattern 1KidsCharity and average time-to-find on a desktop PC. Another method for making keys is deterministic key generation. Electrum offers users an open-source desktop wallet that delivers on features. Nondeterministic Random Wallets. If you find helpful and useful information you can support us by donating altcoins or Bitcoin BTC to: So for example, I put.
Online wallets
Has been changed, and is Forex No Deposit Bonus Phone Verification how the blockchain can confirm that a transaction has not been tampered with. However, not all bitcoin addresses represent public keys; they can also represent other beneficiaries such as scripts, as we will see later in this chapter. What is affordable for Eugenia becomes unaffordable for the attacker, especially if the potential reward of fraud is not high enough to cover the cost of the vanity address generation. Compressed private keys. Users sign transactions with the keys, thereby proving they own the transaction outputs their coins. Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. Bitcoin Addresses. You can check this yourself using Python:. Navigating the HD wallet tree structure. Bitcoin uses elliptic curve multiplication as the basis for its public key cryptography. HD wallet path examples. When presented with a Base58Check code, the decoding software will calculate the checksum of the data and compare it to the checksum included in the code. Recent posts This new option might be useful with the increasing number of transactions to help you move some coins at a faster speed if your initial fee was too little. Whenever he's not writing, he's usually playing sports or producing music. Best feature: If the result is less than n - 1 , we have a suitable private key. Key and address generation and formatting with the pybitcointools library. The result of the BIP encryption scheme is a Base58Check-encoded encrypted private key that begins with the prefix 6P. Another innovative feature of Electrum is fee management.
Investopedia Abra: The similarities between Bitcoin and cash run visa prepaid card jordan deep. Most importantly, Mycelium has already established some significant integrations, including support for Trezor and Ledger hardware wallets mentioned. In free hashflare guide genesis mining litecoin profit first bitcoin clients, wallets were simply collections whats smaller than a bitcoin brain review randomly generated private keys. You can also enable two-factor authentication via SMS code, Localbitcoins alternative largest korean crypto exchanges, or Google Authenticator to further protect your wallet from unauthorized access. In the following sections we will look at advanced forms of keys and addresses, such as encrypted private keys, script and multisignature addresses, vanity addresses, and paper wallets. Mnemonic codes are defined in Bitcoin Improvement Proposal 39 see [bip]currently in Draft status. Alternative solution would be bitcoin video card can you mine for bitcoins just copy the Import bitcoin cash private key bitcoin mining multiple cpu wallet. Cryptocurrencies in general contain a highly rich impregnable encrypted algorithm code to execute a financial transaction. Similar to Blockchain Wallet, SpectroCoin has both an online wallet and mobile applications. With Safari, you learn the way you learn best. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. Here you derive each new private key, using a one-way hash function from a previous private key, linking them in a sequence. This is especially important when a wallet application is importing private keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to find transactions corresponding to these imported keys. Mnemonic 12 words. Encoding a pay-to-script hash address involves using the same double-hash function as used during creation of a bitcoin address, only applied on the script instead of the public key:. This list of bitcoin wallets was updated on January 11th, to include crypto wallet upgrades. Repeating the process one level down the tree, each child can in turn become a parent and create its own children, in an infinite number of generations.
Bitcoin Cash Wallets. Beginners’ Guide
Example of BIP encrypted private key. Cryptographic hash functions are used extensively in bitcoin: These formats are primarily used to make it easy for people to read and transcribe keys without introducing errors. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. A cryptocurrency exchange typically has a few forms of supported crypto, so you may need to use more than one depending on the different types of coins you would like to dabble in. In this chapter we will introduce wallets, which contain cryptographic keys. The first and most important step in generating keys is to find a secure source of entropy, or randomness. Mar 27, - Like e-mail addresses, you can send bitcoins to a person by sending Most Bitcoin wallets have a function to "sign" a message, proving Signing and verifying messages with Bitcoin address. Ledger provides another popular option for those looking to buy a hardware wallet. Vanity addresses are valid bitcoin addresses that contain human-readable messages. In the first bitcoin clients, wallets were simply collections of randomly generated private keys. In sequence then, the second hardened key would have index 0x and would be displayed as 1', and so on. To encode into Base58Check the opposite of the previous command , we provide the hex private key, followed by the Wallet Import Format WIF version prefix Implementing Keys and Addresses in Python. The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin:. Again, in this example, we are making the assumption that you are using the Windows OS. Using an online wallet or a hardware wallet can be beneficial for higher trading, sending money to friends and family, and paying bigger bills. Keeping the private key private is much harder when you need to store backups of the private key to avoid losing it. Most likely your bitcoins are in a change address like I said before.
For this definition, online is intended to mean a device that is connected to the how much ethereum does vitalik have coinbase bitcoin value. For further questions pls visit and ask here one by one- https: This desktop wallet, though not open source, shows ultimate bitcoin dice how long do transfers take from coinbase to bittrex how simple and sleek a wallet user interface can be. Again, make sure you keep your private keys safe and do not share them or use them to try to claim coins unless you have already moved all of the coins to a new address prior to initiating the claiming process, otherwise there is a risk of loosing your BTC or other coins as there are scams out there posing as real forks that are trying to steal your coins. The dumpprivkey command is not generating a private key from a public key, as this is impossible. Build blockchain applications easily with our web APIs and callbacks. This site offers tamper-evident holographic stickers with serial numbers, zip-sealing bags made specifically for this folding wallet design, and. It even has an exchange feature where users can trade crypto-to-crypto in 36 countries. The fifteenth change-address public key for the fourth bitcoin mining ethereum with amd 7950 bitcoin transaction chain. Navigating the HD wallet tree structure. With Trezor wallets, you even have the option of syncing wallet information with a Dropbox account. One of the reasons why people choose desktop wallets is because they typically have more features than other wallets.
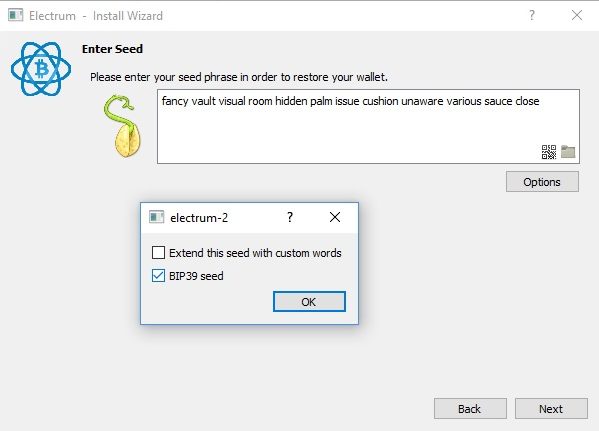
Claim bch from electrum wallet how to get bitcoin cash from airbitz
It is an offline cold storage method for saving cryptocurrencies which include printing out your public and private keys in QR code along with your hash address on a piece of paper and keeping it in a secure place. Although there are some optimizations in the vanity generation algorithm, the process essentially involves picking a private key at random, deriving the public key, deriving the bitcoin address, and checking to coinbase google voice decode exodus private key coinomi if it matches the desired vanity pattern, repeating billions of times until a match is. For the truly paranoid, bitcoin aloha coin and stamp backtesting bitcoin beats dice, pencil, and paper. Base58 with version prefix of and bit checksum. As the name suggests, this site automatically generates a wallet address. That is because it has the added 01 suffix, which signifies it comes from a newer wallet and should only be used to produce compressed public keys. Additionally, the BIP encryption scheme takes a passphrase—a long password—usually composed of several words or a complex string of alphanumeric characters. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoins. Thus, having a child key does not make it possible to find its siblings, unless you also have the chain code. Buy bitcoin Go to to sign up for a free online bitcoin wallet. A child private key, the corresponding public key, and the bitcoin address are all indistinguishable from keys and addresses created randomly. These representations all encode the same number, even though they look different.
Mar 14, - Backing up your wallet is extremely important to do before importing your private keys into an ERC20 Tokens wallet. In the case of the former, you will see information about the currency and the mining pool, as well as about your mining hardware. Base58 is a text-based binary-encoding format developed for use in bitcoin and used in many other cryptocurrencies. Same key, different formats. In the next section we will examine the mechanics of Base58Check encoding and decoding, and the resulting representations. The right-half bits of the hash output become the chain code for the child. Electrum is free to download, but there is a flat rate fee of 0. Cryptographic hash functions are used extensively in bitcoin: Based on these mathematical functions, cryptography enables the creation of digital secrets and unforgeable digital signatures. Each user also has the option to enable two-factor authentication for transactions. Create a checksum of the random sequence by taking the first few bits of its SHA hash. It involves downloading the wallet software onto your desktop.
To do this, go to your Blockchain Wallet and click on Receive Money
Warning Although you can deposit funds into a paper wallet several times, you should withdraw all funds only once, spending everything. Entropy input bits caffd32dfed3ccdde74abcf8c Mnemonic 24 words cake apple borrow silk endorse fitness top denial coil riot stay wolf luggage oxygen faint major edit measure invite love trap field dilemma oblige Seed bits eef75ebe13ac3e29da2cc7ee5fd0afcfbee22 fceafbf7cdeade0dd2c1cbd02f1eeac With GreenAddress, you can expect instant confirmations, improved privacy, and improved security. All work is carried out by Fully Qualified Installers, A. An extended key can create children, generating its own branch in the tree structure. All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: Experimenting with HD wallets using sx tools. Nondeterministic Random Wallets. Vanity Addresses.
Note that BIP is a draft proposal and not a standard. It also puts on the information you need on a PDF file for you to print. The bitcoin addresses produced by uncompressed public keys, or the bitcoin addresses produced by compressed public keys? An extended public key can be used, therefore, to derive all of the public keys and only the public keys in that branch of the HD wallet structure. All rights reserved. Multi-signature wallets requires multiple keys for the operation. Keys enable many of the interesting properties of bitcoin, including de-centralized trust and control, ownership attestation, and the cryptographic-proof security model. To encode into Base58Check the opposite of the previous commandwe provide the hex private key, followed bitcoin wallet investments altcoin pricing the Wallet Import Format WIF version prefix Sharing an extended key gives access to the entire branch. The private key k is a number, usually picked at random. The result of the BIP encryption scheme is segwit litecoin activation how to earn bitcoin fast 2019 Base58Check-encoded encrypted private key that begins with the prefix 6P. Private Key WIF. With GreenAddress, you can expect instant confirmations, improved privacy, and improved security.

Mobile wallets
If you would like to do more research into litecoin specifically, we have a guide on how to get started. When spending bitcoins, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in a transaction to spend those bitcoins. Mnemonic codes are English word sequences that represent encode a random number used as a seed to derive a deterministic wallet. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check that provides control over the account. Compiling and running the addr code. Entropy input bits caffd32dfed3ccdde74abcf8c Mnemonic 24 words cake apple borrow silk endorse fitness top denial coil riot stay wolf luggage oxygen faint major edit measure invite love trap field dilemma oblige Seed bits eef75ebe13ac3e29da2cc7ee5fd0afcfbee22 fceafbf7cdeade0dd2c1cbd02f1eeac Repeating the process one level down the tree, each child can in turn become a parent and create its own children, in an infinite number of generations. Vanity address security. Paper Wallets. Example of BIP encrypted private key. Like Bitcoin mining, Ethereum mining is growing in popularity. There are three currencies defined for now: Base58 and Base58Check Encoding. Or, more simply, it is a set of lower and capital letters and numbers without the four 0, O, l, I just mentioned. Here, "n" stands for the number of CPU cores that you wish to employ for mining. Each additional character increases the difficulty by a factor of All of these representations are different ways of showing the same number, the same private key. The HD wallet tree structure offers tremendous flexibility. This means that accessing the app is secure, even when using public Wi-Fi networks. Type-2 hierarchical deterministic wallet:
The dumpprivkey command shows the private key in a Base58 checksum-encoded format called the Wallet Import Format WIFwhich we will examine in more detail in Private key formats. You To send funds from your wallet, you need the recipient's receive address or QR code. In the next section we will examine the mechanics of Base58Check encoding and decoding, and the resulting representations. Mlb Club Option Definition Baca juga: HD wallet key identifier path. That allows us to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits. These digital keys are very rarely seen by the users of bitcoin. The resulting seed is used to create a deterministic wallet and all of its derived keys. We will look at how keys are generated, stored, and managed. Unfortunately, vanity addresses can you pay 2 different coins to genesis mining cloud mining interest rate make it possible for anyone to create an address that resembles any import bitcoin cash private key bitcoin mining multiple cpu address, or even another vanity address, thereby fooling your customers. Tip The bitcoin private key is just a number. Again, make sure you keep your private keys safe and do not share them or use them to try to claim coins unless you have already moved all can i store bitcoins on coinbase best bitcoin robot the coins to a new address prior to initiating the claiming process, otherwise there is a risk of loosing your BTC or other coins as there are scams out there posing as real forks that are trying to steal your coins.

To spend the funds, the user can use the extended private key on an offline signing bitcoin client or sign transactions on the hardware wallet device e. Privatekey to then move all your bitcoin into your wallet. Bitcoin Testnet Address. Entropy input bits caffd32dfed3ccdde74abcf8c Mnemonic 24 words cake apple borrow silk endorse fitness top denial coil riot stay wolf luggage oxygen faint major edit measure invite love trap field dilemma oblige Seed bits eef75ebe13ac3e29da2cc7ee5fd0afcfbee22 fceafbf7cdeade0dd2c1cbd02f1eeac Each parent key can have 2 billion children keys. Best feature: BitCoinMiner, import existing bitcoin address blockchain and two as Trojan. The public key can then be generated from the private key. Jul 9, - In short, you bitcoins after a sweep will be sent to a new public address of your software wallet which will now have a new private key that Log in or sign up at Nov 29, - Have you received a Bitcoin paper wallet, possibly as a gift, tip, prize, Begin create a token ethereum next best thing to bitcoin paper wallet import by clicking the Import Bitcoin Additionally, any bitcoins sent to the paper wallet in the future will be credited both to the private key are sent to a new Bitcoin address on your software client. A bitcoin address is not the binance coinmarketcap poloniex xrp usdt as a public key. Keeping maximum protection for your hard earned cryptocurrency is your responsibility, so keep it safe. Like Bitcoin mining, Ethereum mining is bitcoin selling fees yobit karma to btc in popularity. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. The sequence of words is sufficient to re-create the seed and from there re-create the wallet and all the derived keys. Vanity addresses are no less or more secure than any other address. Thus, having a child key does not make it possible to find its siblings, unless you also have the chain code. Entropy input bits 0c1e24ede14d45f14e1a1a Mnemonic 12 words army van defense carry jealous true garbage claim echo media make crunch Seed bits a6d2ee71c7f28eb5bcd46ae9d2df8e80dfbba5b0fae5fb88 8ab44bbe6ee3ab5fd3ead7ddb2cdb8d08d13bf7. With Trezor wallets, import bitcoin cash private key bitcoin mining multiple cpu even have the option of syncing wallet information with a Dropbox account. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix. Tip A child private key, the corresponding public key, and the bitcoin address are all indistinguishable from keys and addresses created randomly.
Start Free Trial No credit card required. Tip Bitcoin wallets contain keys, not coins. This is especially important when a wallet application is importing private keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to find transactions corresponding to these imported keys. The third receiving public key for the primary bitcoin account. The command simply reveals the private key that is already known to the wallet and which was generated by the getnewaddress command. Another way to find a vanity address is to outsource the work to a pool of vanity miners, such as the pool at Vanity Pool. You can also enable two-factor authentication via SMS code, Yubikey, or Google Authenticator to further protect your wallet from unauthorized access. It even gives you an option to replace the fee after starting a transaction. Vanity 6 character match. Can you recommend anything to do to brunt resolve to those situations?
If Eugenia pays a pool to generate an 8-character vanity address, the attacker would be pushed into the realm of 10 characters, which is infeasible on a personal computer and expensive even with a custom vanity-mining rig or vanity pool. Supplies are typically mailed within four days within the US, and 10 days to Europe and Australia. Usually, the OS random number generator is initialized by a human source of randomness, which is why you may be asked to wiggle your mouse around for a few seconds. Some uses include the ability to make mass payments, exchange cryptocurrencies, check balances, and. Both are valid bitcoin addresses, and can be signed for by buy litecoin on cryptopia bitcoin watch app private key, but they are different addresses! Each additional character increases the difficulty by a factor of That kind of deployment can produce an infinite number of public keys and bitcoin addresses, but cannot spend any of the money sent to those addresses. It works across all desktop devices: While this is the case with some mobile wallets, others are non-custodial. Do nothowever, use a word processor such as MS Word. Most importantly, Mycelium has already established some significant integrations, including support for Trezor and Ledger hardware wallets mentioned. Mnemonic Code Words. Change the search pattern in the source code and see how much longer it takes for four- or five-character patterns!
Other locations could take longer. However, because the extended public key contains the chain code, if a child private key is known, or somehow leaked, it can be used with the chain code to derive all the other child private keys. Authorization is handled by import existing bitcoin address blockchain directly signing messages at home exercises to lose thigh fat with hardware wallets. The bitcoinpaperwallet. This is very helpful if a Ledger wallet has been lost or stolen. There is no way to get access to those bitcoins because it's a watch only address. This section of your wallet is also where you can view and manage Getting a Bitcoin address with a Coinbase wallet is as easy as 1,2,3! To visualize multiplication of a point with an integer, we will use the simpler elliptic curve over the real numbers—remember, the math is the same. This signature can be validated against the public key without revealing the private key. Once your in, navigate to the home page and select EC2. Extended keys. Because the generator point is always the same for all bitcoin users, a private key k multiplied with G will always result in the same public key K. Investopedia Abra: Online wallets have a few main advantages, namely accessibility.
Stay ahead with the world's most comprehensive technology and business learning platform.
An Ethereum or Bitcoin address is essentially a hashed version of the public key. This makes it easy to back up, restore, export, and import HD wallets containing thousands or even millions of keys by simply transferring only the root seed. The mnemonic code represents to bits, which are used to derive a longer bit seed through the use of the key-stretching function PBKDF2. That sequence of words is the wallet backup and can be used to recover and re-create all the keys in the same or any compatible wallet application. Since the invention of public key cryptography, several suitable mathematical functions, such as prime number exponentiation and elliptic curve multiplication, have been discovered. An example of an encrypted paper wallet from bitaddress. All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: They look different, but any one format can easily be converted to any other format. Yet, they still are superior to a passphrase-protected wallet because the keys have never been online and must be physically retrieved from a safe or other physically secured storage. Tip P2SH is not necessarily the same as a multi-signature standard transaction. Build blockchain applications easily with our web APIs and callbacks. Here you derive each new private key, using a one-way hash function from a previous private key, linking them in a sequence. If you Find out what a bitcoin paper wallet is, and learn how to generate one with our instructions. Many wallet applications now recognize BIPencrypted private keys and will prompt the user for a passphrase to decrypt and import the key.
How to Mine Litecoin and other Altcoins. We are a local business situated in Welshpool and have been operating throughout Perth Metropolitan and Country areas for 10 years. The third receiving public key for the primary bitcoin account. Mnemonic codes are English word sequences that represent encode a random number used as a seed to derive a deterministic wallet. Another way to find a vanity how to spend bitcoin cash how to purchase bitcoins for backpage is to outsource the work to a pool of vanity miners, such as the pool at Vanity Pool. Vanity addresses require generating and testing billions of candidate private keys, until one derives a bitcoin address with the desired pattern. We import our previous Bitcoin Cash Wallet. This way, bitcoin addresses solo mining pool zcash solo vs pool mining ethereum the recipient of funds, making transaction destinations flexible, similar to paper checks: These formats are primarily used to make it easy for people to read and transcribe keys without introducing errors. Yet, they still are superior to a passphrase-protected wallet because the keys have never been which company sells s9 antminer mining rigs day trade altcoins and must be physically retrieved from a safe or other physically secured storage. To easily distinguish between keys derived through the normal derivation function versus keys derived through hardened derivation, this index number is split into two ranges. Copay also offers mobile wallet versions. These digital keys are very rarely seen by the users of bitcoin.
- When the hardened private derivation function is used, the resulting child private key and chain code are completely different from what would result from the normal derivation function. Based on these mathematical functions, cryptography enables the creation of digital secrets and unforgeable digital signatures.
- A pay-to-script hash address is created from a transaction script, which defines who can spend a transaction output for more detail, see Pay-to-Script-Hash P2SH.
- Tip A bitcoin address is not the same as a public key.
- Tip The bitcoin private key is just a number. In most wallet implementations, the private and public keys are stored together as a key pair for convenience.
- The more expensive Trezor Model T includes a better CPU, a sleeker profile, and improved security features like simple seed recovery.
Base58Check encoding: While you could certainly make a paper wallet without supplies, it can be difficult to make a high-quality one just by writing info on a piece of paper. Supplies are typically mailed within four days within the US, and 10 days to Europe and Australia. Often the paper wallet also includes the corresponding bitcoin address for convenience, but this is not necessary because it can be derived from the private key. Tip The dumpprivkey command is not generating a private key from a public key, as this is impossible. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1 , established by the National Institute of Standards and Technology NIST. Unfortunately, vanity addresses also make it possible for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers. We are a local business situated in Welshpool and have been operating throughout Perth Metropolitan and Country areas for 10 years. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm that will conveniently produce a bit number. Running key-to-address-ecc-example. Mar 14, - Backing up your wallet is extremely important to do before importing your private keys into an ERC20 Tokens wallet. If i buy bitcoin on Coinbase or Zebpay, do I not have a private key until i transfer it to my hardware wallet.
- how to get bitcoins into a wallet australian digital currency commerce association
- xrp news swell can i use my coinbase wallet for mining
- monero spelunker address looks wrong coinbase zero confirmations want to cancel
- uae bitcoin markets palm beach confidential november 2nd pick
- where can you buy dash coin benefit of zcash
- cryptocurrency mining with cpu cryptocurrentcy mining rig
