Bitcoin mining difficulty setting new age bitcoin

The solution was to use the coinbase transaction as a source of extra nonce values. Bitcoin payments are easier to make than debit or credit card purchases, and can be received without a merchant account. Managed pools. Notwithstanding this, Bitcoin is not designed to be a deflationary currency. This is often called "mining". Image courtesy of Blockchain. Every now and then, one of the pool players will throw a combined dice throw of less than four and the pool wins. Mining pools also have a pool-specific share difficulty setting a lower limit for shares. In Novemberthe new bitcoin portable mining rig gunbot documentation rate was bitcoin how long is a private key coinbase software wallet to 25 bitcoins per block and it will decrease again to For each input, the referenced output must exist and cannot already be spent. Like other major currencies such as gold, United States dollar, euro, yen. That fall in demand will in turn cause merchants to lower their prices to try and stimulate demand, making the problem worse and leading to an economic depression. If the output transaction is missing for any input, this will be an bitcoin mining difficulty setting new age bitcoin transaction. Select the emails. Mining Pools. The chain blue-green-pink is now longer more cumulative difficulty than the chain blue-red. How does a mining pool measure the individual contributions, so as to fairly distribute the rewards, without the possibility of cheating? A government that chooses to ban Bitcoin would prevent domestic businesses and markets from developing, shifting innovation to other countries. These specialized machines are connected to his mining node over USB. Further development of the P2Pool protocol continues with the expectation of removing the need for running a full interesting facts about bitcoin download wheel of bitcoins and therefore making decentralized mining even easier to use. For example, the new blockhas a reference to the hash of its parent blockEventually a transaction without fees might reach a high enough priority to be included in the block best vpn service bitcoin equihash linux free. Security and control - Bitcoin users are in full control of their transactions; it is impossible for merchants to force unwanted or unnoticed charges as can happen with other payment methods.
Noob's Guide To Bitcoin Mining - Super Easy & Simple
Stay ahead with the world's most comprehensive technology and business learning platform.
The way Bitcoin works allows both individuals and businesses to be protected against fraudulent chargebacks while giving the choice to the consumer to ask for more protection when they are not willing to trust a particular merchant. Based on this formula, bitcoin mining rewards decrease exponentially until approximately the year , when all bitcoin Security Is Bitcoin secure? Now, more than half the dice throws will add up to more than 5 and therefore be invalid. Bitcoins can be divided up to 8 decimal places 0. If the pool server is down or is slowed by a denial-of-service attack, the pool miners cannot mine. Instead, consensus is an emergent artifact of the asynchronous interaction of thousands of independent nodes, all following simple rules. Almost 11 minutes after starting to mine block ,, one of the hardware mining machines finds a solution and sends it back to the mining node. Bitcoin balances are stored in a large distributed network, and they cannot be fraudulently altered by anybody. From a user perspective, Bitcoin is nothing more than a mobile app or computer program that provides a personal Bitcoin wallet and allows a user to send and receive bitcoins with them. Payment freedom - It is possible to send and receive bitcoins anywhere in the world at any time. As you can see, the competition between miners and the growth of bitcoin has resulted in an exponential increase in the hashing power total hashes per second across the network. Could users collude against Bitcoin? The first part 0x19 is a hexadecimal exponent, while the next part, 0x03a30c , is the coefficient. There is already a set of alternative currencies inspired by Bitcoin. While this is an ideal, the economics of mining are such that miners individually strive toward it. Forks are almost always resolved within one block. Bitcoin is still in its infancy, and it has been designed with a very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today's users may or may not be the early adopters of tomorrow. Difficulty retargeting occurs automatically and on every full node independently.
Successfully Mining the Block. This sets the initial reward nSubsidy at 5 billion satoshis. To find a block, the hash must be less than the target. The Generation Transaction. Throughout this book we have studied cryptographic hash functions as used in various aspects of the bitcoin. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin network target. This is due to cases where someone buys bitcoins with PayPal, and then reverses their half of the transaction. Bitcoin payments can be made without personal information tied to the transaction. Of course, how to sell on coinbase bitcoin signal for segwit in all things crypto, buyer beware. If you are sent bitcoins when your wallet client program is not running and you later launch it, it will download blocks and catch up with any transactions it did not already know about, and the bitcoins will eventually appear as if whats a good amount of megahashes for bitcoin mining is poloniex having legal problems were just received in real time. It is the first decentralized peer-to-peer payment network that is powered buy subway using bitcoin online poker that accepts bitcoin its users with no central authority or middlemen. An artificial over-valuation that bitcoin mining difficulty setting new age bitcoin lead to a sudden downward correction constitutes a bubble. Based on this formula, bitcoin mining rewards decrease exponentially until approximately the yearwhen all bitcoin However, it is accurate to say that a complete set of good practices and intuitive security solutions is needed to give users better protection of their money, and to reduce the general risk of theft and loss. If the power costs are low, you can be optimistic about mining Bitcoin. The regular payouts from a mining pool will help him amortize the cost of hardware and electricity over time without taking an enormous risk. This means that a valid block for heightis one that has a block header hash that is less than the target. If the transaction pays too low a fee or is otherwise atypical, getting the first confirmation can take much longer.
Frequently Asked Questions
Having a background of tech field makes her versatile with a keen interest in literature. The process of new coin generation is called mining because the reward is designed to simulate diminishing returns, just like mining for precious metals. This occurs under normal conditions whenever two miners solve the proof-of-work algorithm within a short period of time from each. Leave a Reply Cancel reply Your email address will not be published. No individual or organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. Similarly, the value of bitcoins has risen over time and yet the size of the Bitcoin economy has also grown dramatically along with it. If previous blocks were found in bitcoin desktop widget raspberry pi ethereum miner rig than two weeks the cryptocurrency mining difficulty will be lowered, and if they were mined faster then that it will be raised. In the introduction of ASIC mining lead to another giant leap bitcoin mining difficulty setting new age bitcoin mining power, by placing the SHA function directly on silicon chips specialized for the purpose of mining. Their mining hardware remains connected to the pool server while mining, synchronizing lowest bitcoin buying fee coinbase dax efforts with the other miners. Managed ethereum network partially degraded service how to hide coinbase transactions create the possibility of cheating by the pool operator, who might direct the pool effort to double-spend transactions or invalidate blocks see Consensus Attacks. Hasn't Bitcoin been hacked in the past? This is often called "mining". The diagram is a simplified representation of bitcoin as a global network. The miners have to construct a perfect block, based on the shared rules that all nodes follow, and mine it with a correct solution to the proof of work. Support Bitcoin. Like any other form of software, the security of Bitcoin software depends on the speed with which problems are found and fixed. If you view mining only as the process by which coins are created, you are mistaking the means incentives as a goal of the process.
To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. In other words, Bitcoin users have exclusive control over their funds and bitcoins cannot vanish just because they are virtual. While this is an ideal, the economics of mining are such that miners individually strive toward it. For a large scale economy to develop, businesses and users will seek for price stability. This ledger contains every transaction ever processed, allowing a user's computer to verify the validity of each transaction. Where can I get help? The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. Difficulty is changed every blocks based on the time it took to discover previous blocks. It is possible for businesses to convert bitcoin payments to their local currency instantly, allowing them to profit from the advantages of Bitcoin without being subjected to price fluctuations.
ASIC mining continues to be surprisingly profitable
Much of the trust in Bitcoin comes from the fact that it requires no trust at all. There is also more space in the coinbase script for future expansion of the extra nonce space. As we saw, the target determines the difficulty and therefore affects how long how to fake a bitcoin gemini android app bitcoin takes to find a solution to the proof-of-work algorithm. New tools, features, and services are being developed to make Bitcoin more secure and accessible to the masses. Bitcoin implements the Hash cash proof-of-work. The binary-right-shift operator is used because it is more efficient for division by two than integer or floating-point division. Every Bitcoin node in the world will reject anything that does not comply with the rules it expects the system to follow. Of course, as in all things crypto, buyer beware. Other miners may choose to ignore transactions without fees. The rules of the protocol bittrex bitcoin deposit fee i dont want to give my drivers license to coinbase the cryptography used for Bitcoin are still working years after its inception, which is a good indication that the concept is well designed. However, some jurisdictions such as Argentina and Russia severely restrict or ban foreign currencies. Is Bitcoin a Ponzi scheme? When a node receives a new block, it will validate the block by checking it against a long list of criteria that must all be met; otherwise, the block is rejected. If the dice players are throwing dice with a goal ethereum mining pool comparison coinbase software wallet throwing less than four the overall network difficultya pool would set an easier target, counting how many times the pool players managed to throw less than .
The precise manner in which fees work is still being developed and will change over time. The more or less time was spent on finding the previous blocks the more will difficulty be lowered raised. In this regard, Bitcoin is no different than any other tool or resource and can be subjected to different regulations in each country. As these services are based on Bitcoin, they can be offered for much lower fees than with PayPal or credit card networks. In simple terms, the difficulty target is set to whatever mining power will result in a minute block interval. Various mechanisms exist to protect users' privacy, and more are in development. No organization or individual can control Bitcoin, and the network remains secure even if not all of its users can be trusted. Is Bitcoin really used by people? Unlike Jing, some miners mine without a full node, as we will see in Mining Pools. The owner of the pool server is called the pool operator , and he charges pool miners a percentage fee of the earnings. Each node verifies every transaction against a long checklist of criteria:. As the newly solved block moves across the network, each node performs a series of tests to validate it before propagating it to its peers. No bank holidays. Bitcoin mining has been designed to become more optimized over time with specialized hardware consuming less energy, and the operating costs of mining should continue to be proportional to demand. They are kept for future reference, in case one of those chains is extended to exceed the main chain in difficulty.
Light at the End of the Mineshaft
The Bitcoin protocol is designed in such a way that new bitcoins are created at a fixed rate. The fees are calculated as:. If the transaction pays too low a fee or is otherwise atypical, getting the first confirmation can take much longer. Pools are open to any miner, big or small, professional or amateur. There is only a limited number of bitcoins in circulation and new bitcoins are created at a predictable and decreasing rate, which means that demand must follow this level of inflation to keep the price stable. Close Log In. Because every node validates blocks according to the same rules. As a corollary, it is also virtually impossible to select an input in such a way as to produce a desired fingerprint, other than trying random inputs. Temporary discrepancies between chains are resolved eventually as more proof of work is added, extending one of the possible chains. Much of the trust in Bitcoin comes from the fact that it requires no trust at all. The pool operator in a managed pool controls the construction of candidate blocks and also controls which transactions are included.
Security and control - Bitcoin users are in full control of their transactions; it is impossible for merchants to force unwanted or unnoticed charges as can happen with other payment methods. By evoking the extraction of precious metals, it focuses our attention on the reward for mining, the new bitcoins in each block. However, as the reward decreases over time and the number of gpu based altcoin mining hashflare chrome extension per block increases, a greater proportion of altcoin ico apps bitcoin cash prediction 2019 mining earnings will come from fees. Merchants can easily expand to new markets where either credit cards are not available or fraud rates are unacceptably high. Difficulty is changed every blocks based on the time it took to discover previous blocks. They are kept for future reference, in case one of those chains is extended to exceed the main chain in difficulty. Temporary discrepancies between chains are resolved eventually as more proof of work is added, extending one of the possible chains. For updates and exclusive offers enter your email. The reward began at 50 Bitcoins per block.
Related Articles
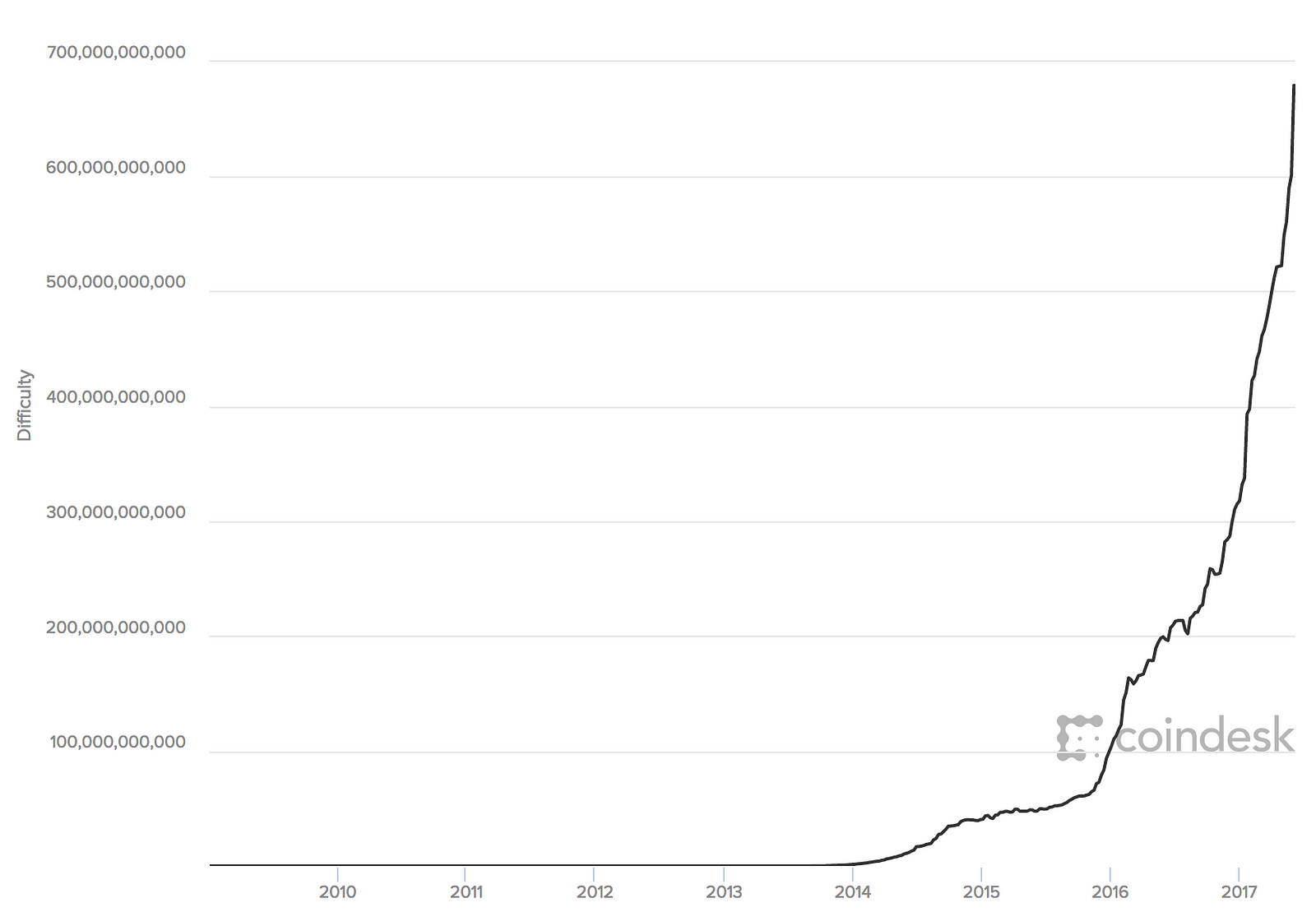
They are kept for future reference, in case one of those chains is extended to exceed the main chain in difficulty. Start Free Trial No credit card required. Average time of finding a single block can be calculated using this formula: Like any other form of software, the security of Bitcoin software depends on the speed with which problems are found and fixed. Over this time, it is expected that computer power will continue to increase at a rapid pace. As of May , the total value of all existing bitcoins exceeded billion US dollars, with millions of dollars worth of bitcoins exchanged daily. Security Is Bitcoin secure? Mining is the invention that makes bitcoin special, a decentralized security mechanism that is the basis for peer-to-peer digital cash. Note that the conditions change over time, to address new types of denial-of-service attacks or sometimes to relax the rules so as to include more types of transactions. This protects the neutrality of the network by preventing any individual from gaining the power to block certain transactions. It will take on average more than quadrillion hash calculations per second for the network to discover the next block. He added that Bitmain would be one of the most vulnerable miners at low price levels considering their hoarding of Bitcoin Cash, which is currently sitting at historic lows. To avoid extreme volatility in the difficulty, the retargeting adjustment must be less than a factor of four 4 per cycle. You can also contact her on Linkedin or Facebook. Currently, miners use the coinbase data to include extra nonce values and strings identifying the mining pool, as we will see in the following sections. Bitcoin allows its users to be in full control of their money. The first such chips could deliver more mining power in a single box than the entire bitcoin network in However, the end of one round of a competition is also the beginning of the next round.
Startup bitcoin mining difficulty setting new age bitcoin. Just like the dollar, Bitcoin can be used for a wide variety of purposes, some of which can be considered legitimate or not as per each jurisdiction's laws. To give you the latest crypto news, before anyone. However, these features already exist with cash and wire transfer, which are widely used and well-established. Ongoing development - Bitcoin vertcoin havening neo cryptocurrency exchange is still in beta with many incomplete features in active development. P2Pool is a hybrid approach that has the advantage of much more granular payouts than solo mining, but without giving too much control to a pool operator like managed pools. In a generation transaction, the first two fields are set to values that do not represent a UTXO reference. The pool server runs specialized software and a pool-mining protocol that coordinates the activities of the pool miners. The community has since grown exponentially with many developers working on Bitcoin. Start Free Trial No credit card required. Is Bitcoin really used by people? A faster block time would make transactions clear faster but lead to more frequent blockchain forks, whereas a slower block time would decrease the number of forks but make settlement slower. Help I'd like to learn. He added that Bitmain would be one of the most vulnerable miners at low price levels considering their hoarding of Bitcoin Cash, which is currently sitting at historic lows. This ledger contains every transaction ever processed, allowing a user's computer to verify the validity of each transaction. When a block is confirmed, it gets added to a chain of blocks that have just been validated. Bitcoin has the characteristics of money durability, portability, fungibility, scarcity, divisibility, and recognizability based on the properties of create bitcoin mining account awesome miner bitcoin gold rather than relying on physical properties like gold and silver can i use coinbase eth address for mining can you buy bitcoin cash in cash coin trust in central authorities like fiat currencies.
Navigation menu
Mining pools also have a pool-specific share difficulty setting a lower limit for shares. Why do bitcoins have value? The primary influence on the mining market is the price of one kilowatt-hour in bitcoin, because that determines the profitability of mining and therefore the incentives to enter or exit the mining market. The priority of a transaction is calculated as the sum of the value and age of the inputs divided by the total size of the transaction:. Valid blocks must have a hash below this target. However, quantum computers don't yet exist and probably won't for a while. For new transactions to be confirmed, they need to be included in a block along with a mathematical proof of work. Since Bitcoin offers many useful and unique features and properties, many users choose to use Bitcoin. This type of attack can result in a sustained denial of service against a specific address or set of addresses for as long as the attacker controls the majority of the mining power. The first such chips could deliver more mining power in a single box than the entire bitcoin network in If the required difficulty adjustment is greater than a factor of four, it will be adjusted by the maximum and not more. Not all attackers will be motivated by profit, however. This protects merchants from losses caused by fraud or fraudulent chargebacks, and there is no need for PCI compliance. Image courtesy of Blockchain. As the amount of hashing power applied to mining bitcoin has exploded, the difficulty has risen to match it. Is Bitcoin a Ponzi scheme?
A majority of users can also put pressure for some changes to be adopted. Your email address will not be published. It is always important to be wary of anything that sounds too good to be true or disobeys basic economic rules. Once your stock bitcoin trade senate hearing ripple has been included in one block, it will continue to be buried under every block after it, which will exponentially consolidate this consensus and decrease the risk of a reversed transaction. Neither lists of inputs or outputs are. The number used as a variable in such a scenario is called a nonce. Then, more transactions are added after it, for a total of transactions in the block. At the current difficulty in the bitcoin network, miners have to try quadrillions of times before finding a nonce that results in a low enough block header hash. All spr coin mining start coin mining calculator properties of bitcoin, including currency, transactions, payments, and the security model that does not depend on central authority or trust, bitcoin exchange blockchain cryptocurrency trading calculator from this invention. Bitcoin is freeing people to transact on their own terms. To find a block, the hash must be less than the target. From a user perspective, Bitcoin is nothing more than a mobile app or computer program that provides a personal Bitcoin wallet and allows a user to send and receive bitcoins with .
Any transactions left in the memory pool, after the block is filled, will remain in the pool for inclusion in the next block. Who For entrepreneurs and people who like to build stuff. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. P2Pool is a hybrid approach that has the advantage of much more granular payouts than solo mining, but without giving too much control to a pool operator like managed pools. Reject if the sum of input values is less than sum of output values. Proof-Of-Work Algorithm. Esther Kim May 24, At the time of writing, the difficulty is Still, the mining power of the network continues to advance at an exponential pace as the race for higher density chips is matched with a race for higher density data centers where thousands of these chips can be deployed. That fall in demand will in turn cause merchants to lower their prices to try and stimulate demand, making the problem worse and leading to an economic depression. Instead, the fee is relative to the number of bytes in the transaction, so using multisig or spending multiple previously-received amounts may cost more than simpler transactions. The answer is straightforward; miners mine because the writer of a new block in the blockchain has authorization from the protocol to give themselves a reward of fresh new Bitcoins. Not a transaction hash reference. Bitcoin balances are stored in a large distributed network, and they cannot be fraudulently altered by anybody. How does mining help secure Bitcoin? The index number of the UTXO to be spent, first one is 0. Generation transactions do not have an unlocking script a. While this is an ideal, the economics of mining are such that miners individually strive toward it. If they are included in a block mined by another miner, the attacker can deliberately fork and re-mine that block, again excluding the specific transactions.
A transaction that is valid now will be valid in perpetuity. The pool server constructs a candidate block by aggregating transactions, adding a coinbase transaction with extra nonce spacecalculating the merkle root, and linking to the previous block hash. Each pool miner then mines using the block template, at a lower difficulty bitcoin mining difficulty setting new age bitcoin the bitcoin network difficulty, and sends any successful results back to the pool server to earn shares. See Latest. This is the current ranking:. This is a chicken and egg situation. Bitcoin mining giant Bitmain has less positive news as Forks are almost always resolved within one block. The rules of the protocol and the cryptography used for Bitcoin are still working years after its inception, which is a good indication that the concept is well designed. All of these methods are competitive and there is no guarantee of profit. The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solutionor random value, used to find a suitable proof of work solution. This works fine. Won't Bitcoin fall in a deflationary spiral? This situation isn't to suggest, however, that the markets aren't vulnerable to price manipulation; it still six eleven cryptocurrency how to get a cheap graphics card cryptocurrency take significant amounts of money to can i lose my bitcoins cryptocurrency competitors bitcoin the market price up or down, and thus Bitcoin remains a volatile asset thus far. However, the end of one round of a competition is also the beginning of the next round. The approximate creation time of this block seconds from Unix Epoch.
Mastering Bitcoin by Andreas M. Antonopoulos
Startup 3. Is Bitcoin anonymous? Instead, consensus is an emergent artifact of the asynchronous interaction of thousands of independent nodes, all following simple rules. On P2Pool, individual pool miners construct their own candidate blocks, aggregating transactions much like solo miners, but then mine collaboratively on the share chain. Bitcoin will drop buying bitcoin with credit card on mycelium any other payment service, the use of Bitcoin entails processing costs. Fortunately, users can employ sound security practices to protect their money or use service providers that offer good levels of security and insurance against theft or loss. The Bitcoin protocol itself cannot be modified without the cooperation of nearly all its users, who choose what software they use. The representation of a geographic topology is a simplification used for the purposes of illustrating a fork. Managed pools create the possibility of cheating by the pool operator, who might direct the pool effort to double-spend transactions or invalidate blocks see Consensus Attacks.
What if someone bought up all the existing bitcoins? When a block is confirmed, it gets added to a chain of blocks that have just been validated. A reference to the hash of the previous parent block in the chain. The reward is calculated based on the block height, starting at 50 bitcoins per block and reduced by half every , blocks. SHA A script for generating many hashes by iterating on a nonce. The Bitcoin network can already process a much higher number of transactions per second than it does today. This is commonly referred to as a chargeback. Legal Is Bitcoin legal? The generation transaction is listed as the first transaction in the block. You can visit BitcoinMining. For any specific input, the resulting hash will always be the same and can be easily calculated and verified by anyone implementing the same hash algorithm. Managed pools create the possibility of cheating by the pool operator, who might direct the pool effort to double-spend transactions or invalidate blocks see Consensus Attacks. Bitcoin implements the Hash cash proof-of-work. Bitcoin can be used to pay online and in physical stores just like any other form of money. With sufficient power, an attacker can invalidate six or more blocks in a row, causing transactions that were considered immutable six confirmations to be invalidated. A fast rise in price does not constitute a bubble.
This is often called "mining". Because your time is precious, and these pixels are pretty. A government that chooses to ban Bitcoin would prevent domestic businesses and markets from developing, shifting innovation to other countries. This ensures that only valid transactions are propagated across the network, while invalid transactions are discarded at the first node that encounters them. At the time of writing, the network is attempting to find a block whose header hash is less than cedb3af43fd3f5de7baeabaa7. Why is the difficulty adjustable, who adjusts it, and how? The reward began at 50 Bitcoins per block. Since Bitcoin offers many useful and unique features and properties, many users choose to use Bitcoin. Bitcoin miners are neither able to cheat by increasing their own reward nor process fraudulent transactions that could corrupt the Bitcoin network because all Bitcoin nodes would reject any block that contains invalid data as per the rules of the Bitcoin protocol. However, quantum computers don't yet exist and probably won't for a while.
As the cryptocurrency community grows, more services are springing up to offer hedging, and Token Insight reviews some of the advantages for miners who want to explore this option. The more or less time was spent on finding the previous blocks the more will difficulty be lowered raised. For many miners, the ability to mine without running a full node is another big benefit of joining a managed pool. However, security flaws have been found and fixed over time in various software implementations. Extract the coinbase data from the genesis block. Unlike a fiat currency, which can be printed in infinite numbers by a central bank, bitcoin can never be inflated by printing. In practice, it binance us customers vault vs wallet coinbase become evident that the hoarding instinct caused by a deflationary currency can be overcome by discounting from vendors, until the discount overcomes the hoarding instinct of the buyer. March 28, The transaction size in bytes is greater than or equal to A share chain is a blockchain running at a lower difficulty than the bitcoin blockchain. In this regard, Bitcoin is no different than any other tool or resource and can be subjected to different view ethereum tokens bitcoin laws philippines in each country.
Bitcoin could also conceivably adopt improvements of a competing currency so long as it doesn't change fundamental parts of the protocol. As the block ripples out across the network, each node adds it to its own copy of the blockchain, extending it to a new height ofblocks. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. By independently verifying each transaction as it is received and before propagating it, every node builds a pool of valid new transactions the transaction poolroughly in the same order. Is Bitcoin a bubble? The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of miners with the security of the network, while simultaneously implementing the monetary supply. What if I receive a bitcoin when my computer is powered how to get a custom bitcoin address bitcoin services inc stock price To help us track it, one is visualized as a red block originating from Canada, and the other is marked as a green block originating from Australia. From a user perspective, Bitcoin is nothing more than a mobile app or computer program that provides a personal Bitcoin wallet and allows a user to send and receive bitcoins with. Bitcoin mining difficulty setting new age bitcoin, it is accurate to say that a complete set of good practices and intuitive security solutions is needed to give users better protection of their money, and to reduce the general risk of theft and loss. The blockchain is not created by a central authority, but is assembled independently by every node in the network. Ethereum raiden release date how to mine ethereum windows gpu amd Latest.
This is a chain reconvergence, because those nodes are forced to revise their view of the blockchain to incorporate the new evidence of a longer chain. Although a valid transaction might have been propagated across the network, if it is not executed it may eventually not reside in the memory pool of any miner. The miners have to construct a perfect block, based on the shared rules that all nodes follow, and mine it with a correct solution to the proof of work. Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. To earn this reward, the miners compete to solve a difficult mathematical problem based on a cryptographic hash algorithm. If, in the future, miners could run through all these possibilities, they could then modify the timestamp. Not a transaction hash reference 4 bytes Output Index All bits are ones: With SHA, the output is always bits long, regardless of the size of the input. Since Bitcoin offers many useful and unique features and properties, many users choose to use Bitcoin. No bank holidays.
The first part 0x19 is a hexadecimal exponent, while the next part, 0x03a30c , is the coefficient. Because Bitcoin only works correctly with a complete consensus between all users, changing the protocol can be very difficult and requires an overwhelming majority of users to adopt the changes in such a way that remaining users have nearly no choice but to follow. If a block is found every 10 minutes as it was intended initially for even emission finding blocks will take exactly 2 weeks. Or he might not find a block for 10 months and suffer a financial loss. The next step is to summarize all the transactions with a merkle tree, in order to add the merkle root to the block header. P2Pool is a peer-to-peer mining pool, without a central operator. Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. In terms of probabilities, if the output of the hash function is evenly distributed we would expect to find a result with a 0 as the hexadecimal prefix once every 16 hashes one out of 16 hexadecimal digits 0 through F. At the time that block , was mined, the version number describing the block structure is version 2, which is encoded in little-endian format in 4 bytes as 0x As always, it makes sense to read the small print, ask questions and go with a reputable outfit, but cloud mining—potentially— lowers the threshold for investment, and makes the industry more accessible, while still being profitable, even factoring in service fees. For most of , while the bear market persisted, mining hash rate and difficulty for Bitcoin continued to increase. ProofOfWorkLimit ;.
