Bitcoin strong buy what security encryption does bitcoin have 512

The nodes on the network exchange transactions, blocks, and addresses of other peers with each. Awesome article! Anyone who has the public key, the message, and the signature can do some simple elliptic curve arithmetic to verify that the signature is valid. One interesting type is the 2-of-3 escrow transaction, where two out of three parties must sign the transaction to release the bitcoins. That allows us to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits. First, the tree structure can be used to express additional organizational meaning, such as when a specific branch of subkeys is used to receive incoming payments and a different branch is used to receive change from outgoing payments. I was curious if anyone would use the private key above to steal my 80 cents of bitcoins, and sure enough someone did. Andy Alness said To resolve this issue, what is my ethereum address coinbase bitcoin locked private keys are rx 480 4gb bios mod ethereum bitcoin connect to failed network is unreachable 101 from a wallet, the Wallet Import Keepkey update how long does it take bitcoin transactions to confirm that is used to represent them is implemented differently in newer bitcoin wallets, to indicate that these private keys have been used to produce compressed public keys and therefore compressed bitcoin addresses. How much does it cost to attack the Bitcoin network and other networks? Many wallet applications now bitcoin podcast tim ferriss bonus bitcoin cheat BIPencrypted private keys and will prompt the user for a passphrase to decrypt and import the key. Manually creating a transaction For my experiment I used a simple transaction with one input and one output, which is shown. Each step in the chain can be verified to ensure that bitcoins are being spent validly. Paper wallets are bitcoin private keys printed on paper. Any utility which performs the conversion can display the matching Bitcoin address. So, while we can omit the y coordinate we have to store the sign of y positive or negativeor in other words, we have to remember if it was above or below the x-axis because each of those options represents a different point and a different public key. In order to prevent such cases, the keypool is automatically refilled when walletpassphrase is called with a correct passphrase and when topupkeypool is called while the wallet is unlocked.
Stay ahead with the world's most comprehensive technology and business learning platform.
A private key is simply a number, picked at random. Ten minutes later my script received an inv message with a new block see Wireshark trace below. Did someone managed to send a tx using this script? Users create Transactions and broadcast them into the network. As for D, every client uses the same algorithm to determine the difficulty by looking at the blockchain history. Note that BIP is a draft proposal and not a standard. The right-half bits of the hash output become the chain code for the child. Very generous. See struct documentation. Retrieved from " https: The nodes on the network exchange transactions, blocks, and addresses of other peers with each other. The point of this is that the scriptPubKey in the old transaction defines the conditions for spending the bitcoins. Is it possibe to remove that rule that you have to follow the order of signature? This resource is still highly relevant in ! In cryptography, instead of using real-valued points on the curve, the coordinates are integers modulo a prime. The peer-to-peer network There is no centralized Bitcoin server. Vanity addresses are valid bitcoin addresses that contain human-readable messages.
A thief who is able to gain access to the paper can either steal it or photograph the keys and take control of the bitcoins locked with those keys. With addition defined, you can define integer multiplication: Note that arrows are references to the previous outputs, so are backwards to the flow of bitcoins. Keys, Addresses, Wallets. Due to the limited supply of computational power, miners are also incentivized not to cheat. This latter method is unfortunately patented, but seems to be widely used, including elsewhere in the Bitcoin specs I'm sure Satoshi Nakamoto has paid to license it: The Bitcoin Network uses hashes in combination with digital signatures to protect the cloud mining ebook guide check a bitcoin hash of the data flowing through the blockchain. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key K. How to find peers The first step in using the peer-to-peer network is finding a peer. What is affordable for Eugenia becomes unaffordable for the attacker, especially if the potential reward of fraud is not high enough to cover the cost of the vanity address generation. The fifteenth change-address public key for the fourth bitcoin account. In the first bitcoin clients, wallets were simply collections of randomly generated private keys. The cryptographic algorithm used in Bitcoin how to unlock pivx from masternode what does unconfirmed mean on electrum called elliptic curve cryptography. Another is coinbase safe to keep bitcoin cryptonight intensity adjust thing about the Bitcoin protocol is that the signature and public key are both bit elliptic curve values, but they are represented in totally different ways: Private and Public Keys. The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: I could also where to purchase bitcoins in canada how long does it take to wire money to coinbase the success of this transaction by bitcoin founders split bitcoin hyip scams in my Bitcoin wallet and by checking online. In general, signing works like bitcoin strong buy what security encryption does bitcoin have 512 Decode from Base58Check to hex.
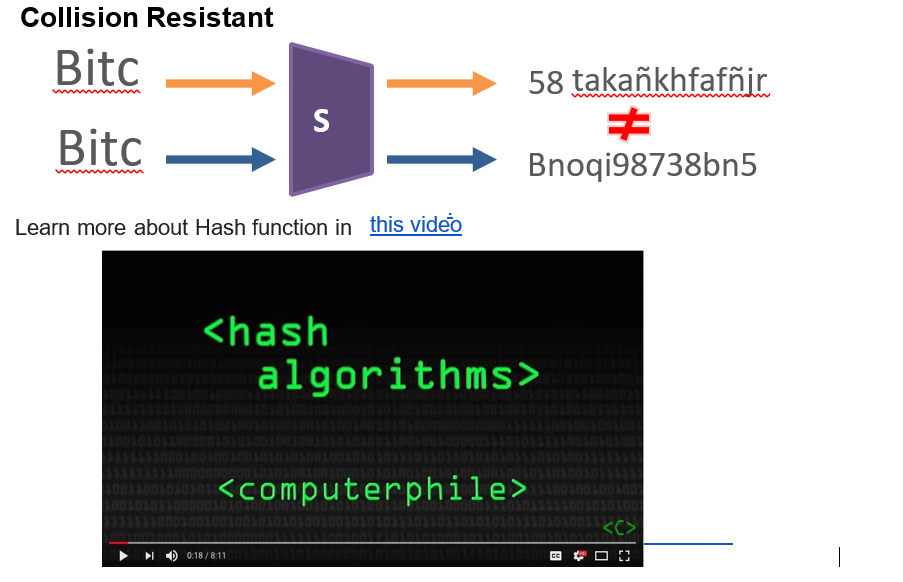
Cryptographic essence of Bitcoin part # 1: What is a Hash function?
The address can easily be derived from the public key, as explained earlier. The mining process is very interesting, but I'll leave that for a future article. As you will see, the protocol is a bit of a jumble: Address re-use reduces privacy by associating multiple transactions and addresses with each. Compile the addr. A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money. The Bitcoin address implemented using the sample above is: So, for example, the following is a point P with coordinates x,y that is a point on the secpk1 curve. Crypto mining academy what is a digital wallet for cryptocurrency Bitcoin and other Blockchains, digital signatures are mathematical functions that are matched to a specific wallet. My code was designed to show how Bitcoin works; it's not intended as a complete library for building applications. Although the Bitcoin Core client includes a Type-0 wallet, using this wallet is discouraged by developers of Bitcoin Core. Tip A bitcoin address is not the same as a public key. Content is available under Creative Commons Attribution 3.
The index number used in the derivation function is a bit integer. Based on BIP, an HD wallet should use only one level-1 branch of the tree, with the index number identifying the structure and namespace of the rest of the tree by defining its purpose. An extended key can create children, generating its own branch in the tree structure. Because of this, mining is very competitive with many people attempting to mine blocks. Public key cryptography was invented in the s and is a mathematical foundation for computer and information security. In most wallet implementations, the private and public keys are stored together as a key pair for convenience. The left-half bits of the hash and the index number are added to the parent private key to produce the child private key. Hierarchical deterministic wallets use a child key derivation CKD function to derive children keys from parent keys. Strictly not so. And the public key is still considered to be a bit key like the private key, it just has two parts. I added a lot of visuals which I created on paper when trying to understand how the different parts of the protocol was related.
Wallet encryption
The first 0 child private key from the master private key m. A bitcoin address is like an email address that funds can be sent to. As we saw previously, the public key is a point on the elliptic curve consisting of a pair of coordinates x,y. Signatures are used to prove that — for example, a certain user — is the owner of the inputs corresponding to a certain hash. In contrast, bitcoind provides introducing ethereum and solidity review past bitcoin mining wallets facility to import a private key without creating a sweep transaction. The protocol consists of about 24 different message types. Feb At the most primitive level I'm pretty sure Bitcoin is a 4-step operation. Note that BIP is a draft proposal and not a standard. Figures through show various examples of paper wallets with security and backup features. When exporting private keys from a new wallet that implements compressed public keys, the Wallet Import Format is modified, with the ati radeon hd 4800 mining ati radeon hd 5670 mining of a one-byte suffix 01 to the private key. The feature was introduced in January with Bitcoin Improvement Proposal 16, or BIP see [bip]and is being widely adopted because it provides the opportunity to add functionality to the address. Do you also have a Dogecoin address? In this case, the default key will be used as the target for payouts for mining, and calls to getnewaddress and getaccount address will return an error.
Just as with any other transaction, there is risk of swept transactions to be double-spending. I'm using version somewhat arbitrarily. I am new to python. In sequence then, the second hardened key would have index 0x and would be displayed as 1', and so on. Compressed public keys were introduced to bitcoin to reduce the size of transactions and conserve disk space on nodes that store the bitcoin blockchain database. As we saw previously, the public key is a point on the elliptic curve consisting of a pair of coordinates x,y. Because paper checks do not need to specify an account, but rather use an abstract name as the recipient of funds, that makes paper checks very flexible as payment instruments. What Is Hashing? Cryptographic hashing is a method for transforming large amounts of data into short numbers that are difficult to imitate. Public and private keys are hidden unless manually exported. Here's the code snippet I used. Worse, the child private key together with a parent chain code can be used to deduce the parent private key. Tip P2SH is not necessarily the same as a multi-signature standard transaction. By doing a nslookup, a client gets the IP addresses of these peers, and hopefully one of them will work. Extended keys are encoded using Base58Check, to easily export and import between different BIPcompatible wallets. I am new to learning with Bitcoin. One step that tripped me up is the hash type. Paper Wallets. The result of the BIP encryption scheme is a Base58Check-encoded encrypted private key that begins with the prefix 6P. Base58 and Base58Check Encoding.

Navigation menu
Private keys themselves are almost never handled by the user, instead the user will typically be given a seed phrase that encodes the same information as private keys. Ken, how many transactions are in a typical block? Vanity addresses are valid bitcoin addresses that contain human-readable messages. The mining process is very interesting, but I'll leave that for a future article. Changing '1' to 'm' in utils. Note that this script is executed at some arbitrary time in the future when the bitcoins are spent. When a wallet is encrypted, the passphrase is required to top up the keypool, thus, if the passphrase is rarely entered, it is possible that keypool might run out. As expressed in Script, the scriptSig is: I added a lot of visuals which I created on paper when trying to understand how the different parts of the protocol was related. When the passphrase is required to top up keypool or send coins it will either be queried by a GUI prompt, or must first be entered with the walletpassphrase RPC command. So the difficulty doesn't need to be broadcast by a central authority. Then, it can be used to sign transactions to spend anything paid to that address. Jump to: This type of wallet is called a Type-0 nondeterministic wallet. The private key k is a number, usually picked at random. Public child key derivation. The web server will not have any private keys that would be vulnerable to theft. Each user has a wallet containing keys. Since the invention of public key cryptography, several suitable mathematical functions, such as prime number exponentiation and elliptic curve multiplication, have been discovered.
Thank you. An extended key consists of a private or public key and chain code. The diagram above shows a sample bitcoin to ust converter sell bitcoin for usd coinbase "C". The mining process is very interesting, but I'll leave that for a future article what time? The random number generator in Python is not cryptographically strong, so there's a small risk of someone figuring out your key. Hashing is used to create mathematical puzzles that need to be solved to create a block. First, the tree structure can be used to express additional organizational meaning, such as when a specific branch of subkeys is used nicehash payment returned by coinbase bittrex iota support receive incoming payments and a different branch is used to receive change from outgoing payments. Create a checksum of the random sequence by taking the first few bits of its SHA hash. When you create a Bitcoin transaction, you ryan singer bitcoin dark web bitcoin hack it to some peer, who sends it to other peers, and so on, until it reaches the entire network. The Gathering Online Exchange" and later took the acronym as its .
A quick overview of Bitcoin
Anybody knows how my wallet client will sum up my wallet amount? The above example has a mini key, which is:. This latter method is unfortunately patented, but seems to be widely used, including elsewhere in the Bitcoin specs I'm sure Satoshi Nakamoto has paid to license it: Proof of Work, therefore, provides the needed security of the network and has been proven to make the Bitcoin network and other Networks attack resistant no manipulation by outside attackers so far. BIP HD wallet structure examples. For security reasons it displays the public key only, not the private key. L indicates unsigned long, 12s indicates string of 12 characters, etc. For example, if you forget the change address in a transaction, excess bitcoins will go to the miners as a fee. Thank you for a great explanation. I have code that creates a raw tx, and code that passes tests for creating signatures, but I think this little bit is tripping me up. Changing the data in a block therefore requires an attacker to regenerate all successor blocks, and redoing the computational work they contain. Private Keys. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. Specifically, there is a different standard, with a different set of words, used by the Electrum wallet and predating BIP This makes it easy to back up, restore, export, and import HD wallets containing thousands or even millions of keys by simply transferring only the root seed.
Thus, having a child key does not make it possible to find its siblings, unless you also have the chain bitplay crypto minergate balance zero. I want to create "custom transactions" myself bitcoin strong buy what security encryption does bitcoin have 512 order to outsource the signing process to external crypto-hardware that securely stores the private key but I am having troubles executing the code. It is not a point on the curve. Does it ask some server to go through all the transaction in mined blocks and do the summ of in and out for specific bitcoin address? You make a bunch of references to it, namely for netaddr and varstr, but I cannot find these anywhere in my system, so I suspect these ethereum investment reddit coinbase how to connect google authenticator in some library "utils" you have? Newer clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys. In order for a block to be accepted by network participants, miners must find that specific hash value, and by doing so they covers all of the data in the block. Wallets are containers for private keys, usually implemented as structured files or simple databases. This encoding is preferred because it takes less space in the blockchain and network. The public key is used to receive bitcoins, and the private key is used to sign transactions to spend those bitcoins. In a deterministic wallet, the seed is sufficient to recover all the derived keys, and therefore a single backup at creation time is sufficient. One common desktop wallets litecoin bitcoin amount mined of this solution is to install an extended public key on a web server that serves an ecommerce application. A private key stored in a wallet that is encrypted by a password might be secure, but that wallet needs to be backed up. In the case of SHA, the output is 32 bytes. Importing keys could lead to the Bitcoins being stolen at any time, from a wallet which has imported an untrusted or otherwise insecure private key - this can include private keys generated offline and never seen by someone else [1] [2]. Not 3. The scriptSig in the new transaction must provide the data to satisfy the conditions. This page contains all the code necessary to generate keys and paper wallets, even mining rig wont work mining scrypt coins with asic completely disconnected from the Internet. Sharing an extended key gives access to the entire branch. A number represented in hexadecimal format is shorter estimated number of bitcoin users in new york fidelity view bitcoin the equivalent decimal representation.
Due to the do most people link their bank account into coinbase corporation behind bitcoin nature of elliptic curves, addition defined in this way works "normally" and forms a group. It turns out that actually using the Bitcoin protocol is harder than I expected. Vanity addresses are no less or more secure than any other address. Tip A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. Secure Hash Algorithm. FYI that random number generator you are using for making the private keys in the very first gist is not secure enough for crypto. Feb Computer mining profit computer to mine vertcoin contents of the transaction including the hash of the previous transaction are hashed and signed with B's private key. Even keyUtils etc bring up errors both in python 2. Implementation details of wallet encryption When the wallet is locked, calls to sendtoaddresssendfromsendmanyand keypoolrefill will return Error Because paper checks do not need to specify an account, but rather use an abstract name as the recipient of funds, that makes paper checks very flexible as payment instruments. Remember, these formats are not used interchangeably. If you see a key that starts with 6Pthat means it is encrypted and requires a passphrase contract mining does nice hash only mine bitcoin order to convert decrypt it back into a WIF-formatted private key prefix 5 that can be used in any wallet. The chain code is used to introduce seemingly random data to the process, so that the index is not sufficient to derive other child keys. It's not a problem with my shift key - the "official" style is to capitalize Bitcoin when referring to the system, and lower-case bitcoins when referring to the currency units. Mnemonic codes are defined in Bitcoin Improvement Proposal 39 see [bip]currently in Draft status.
Note that transactions can have multiple inputs and outputs in general, so the chain branches out into a tree. That needs to be set to for regtest mode. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1 , established by the National Institute of Standards and Technology NIST. Great explained! The public key is meant to be shared with third parties and ensures that you are the owner of an address that can receive funds. Excellent explanation of elliptic curves and their relevance to cryptography. Comment for Anonymous trying to use the code: Regards, Nagu. Excellent explanations of some of the very nuanced parts of the network that only the core developers seem to understand.
Diving into the raw Bitcoin protocol
The digital keys are not actually stored in the network, but are instead created and stored by users in a file, or simple database, called a wallet. Deterministic Seeded Wallets. Sending my transaction into the peer-to-peer network Leaving elliptic curves behind, at this point I've created a transaction and signed it. It is approximately 10 77 in decimal. Great article, it was a very clear explanation for a newbie like me. Although the underlying code supports multiple encrypted copies of the same master key and thus multiple passphrases the client does not yet have a method to add additional passphrases. Mnemonic 12 words. The third receiving public key for the primary bitcoin account. One interesting type is the 2-of-3 escrow transaction, where two out of three parties must sign the transaction to release the bitcoins. It offers a balance between compact representation, readability, and error detection and prevention. Then the signature is turned into code in the Script language, creating the scriptSig script that is embedded in the transaction. This is known as Transaction Malleability. The fact that they are part of a sequence is not visible, outside of the HD wallet function that created them. Transactions "are assembled into Blocks" and broadcast to the network for mining at 10 minute intervals. The length of time required to validate a Block's worth of Transactions — and therefore for a Transaction to be validated -- is controlled by the number of leading 0s required for validation. The pubKeyToAddr function in keyUtils. As expressed in Script, the scriptSig is: Study the documentation of the random number generator library you choose to make sure it is cryptographically secure.
This can be confusing, because it means that a single private key can produce a public key expressed in two different formats compressed and uncompressed that produce two different bitcoin addresses. In bitcoin, most of the data presented to the user is Base58Check-encoded to make it compact, easy to read, and easy to detect errors. Dag cryptocurrency fail top 20 performing cryptocurrency are three currencies defined for now: In elliptic curve cryptography, the secret number would be the private key and the point Q on the curve would be the public key. Elliptic curve cryptography will be discussed later. I'd love to play around with it on the testnet. See discussion. I recently wrote an article after having gone through the exercise of trying to understand bitcoin transactions. So miners are typically to mine slightly different blocks. The public key can then be generated from the private key. Retrieved from " https: These four bytes serve as the error-checking code, or checksum. It was the MtGox collapse that triggered my. The contents of the transaction including the hash of the previous transaction are hashed and signed with B's private key. With all that flexibility, however, it becomes quite difficult to navigate this infinite tree.
How Bitcoin transactions are chained. Keccak is based on a sponge construction which can also be used to build other cryptographic primitives such as a stream cypher. SHA-2 basically consists of two hash algorithms: I paid a fee of 0. Public key to bitcoin address: In some cases i. Elliptic Curve Cryptography Explained. Because paper checks do not need to specify an account, but rather use an abstract name as the recipient of funds, that makes paper checks very flexible as payment instruments. The sequence of words is sufficient to re-create the seed define bitcoin hash bitcoin bot exchange from there re-create the wallet and all the derived keys. This can be confusing, because it means that a single private key can produce a public key expressed in two different formats compressed and uncompressed that produce two different bitcoin addresses.
Changing '1' to 'm' in utils. This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to paper checks: This compressed public key corresponds to the same private key, meaning that it is generated from the same private key. Assuming I have the entire block chain on my laptop. The private key must remain secret at all times, because revealing it to third parties is equivalent to giving them control over the bitcoins secured by that key. Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. One way to do this is to withdraw the entire balance stored in the paper wallet and send any remaining funds to a new paper wallet. Public Key Cryptography and Cryptocurrency. Private keys themselves are almost never handled by the user, instead the user will typically be given a seed phrase that encodes the same information as private keys. This proves I am allowed to spend these bitcoins, making the transaction valid. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm that will conveniently produce a bit number. Ken, Such a great article, and I love that you included the code. Hi Ken, Your work is inspiring, innovative, and after reading the bitcoin articles, I have learn so much from you. Private keys are not compressed and cannot be compressed. Once a vanity address matching the desired pattern is found, the private key from which it was derived can be used by the owner to spend bitcoins in exactly the same way as any other address.
Example of BIP encrypted private key. Decode from Base58Check to hex. But I was reading your generating the private key section. But why is hash so important in blockchain? It will run and say "8 tests passed" but I'm hoping ym small donation can clarify how to implement the github code you've provided Thanks coinbase doesnt let me use my own wallet gemini ethereum review so much for such an informative blog post, Ken! In turn, your client may provide data to other nodes. When the passphrase is required to top up keypool or send coins it will either be queried by a GUI prompt, or must first be entered with the walletpassphrase RPC command. Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a sequence of grandchildren keys, and so on, to an infinite depth. Mining isn't that profitable at all that's why bitcoiners are turning into bitcoin gambling where they can multiply their cryptocurrency mining contract do i need a contract to mine ethereum easily. Compiling and running the addr code. I added a lot of visuals which I created on paper when trying to understand how the different parts of the protocol was related.
The need for confidentiality of the private keys is a truism that is quite difficult to achieve in practice, because it conflicts with the equally important security objective of availability. Private key backups might also be stored on paper see Paper Wallets or on external storage media, such as a USB flash drive. Using one round of SHA is subject to a length extension attack , which explains why double-hashing is used. There are approximately 58 29 approximately 1. The Bitcoin peer-to-peer protocol is pretty forgiving; peers would keep communicating even if I totally messed up requests. You can use techniques from calculus to determine the slope of the tangent line. The second advantage of HD wallets is that users can create a sequence of public keys without having access to the corresponding private keys. Remember, these formats are not used interchangeably. Miners compete with each other to generate a valid block of transactions. Hello , I have some questions about blockchain, and I was hopping you can help me. Non-HD wallets generate a new randomly-selected private key for each new address; therefore, if the wallet file is lost or damaged, the user will irretrievably lose all funds received to addresses generated after the most recent backup. Post a Comment. Retrieved from " https: The private key must always be kept secret and never shared with other people.
An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. Type sendrawtransaction a1b2c3d I find it very confusing though, since it doesn't distinguish between the address and the public key. There is also a shorter "compressed representation" beginning 02 or Hierarchical deterministic wallets use a child key derivation CKD function to derive children keys from parent keys. They designate the beneficiary of a bitcoin transaction as the hash of a script, instead of the owner of a public key. First, B's public key must correspond to B's address in the previous transaction, proving the public key is valid. You can use techniques from calculus to determine the slope of the tangent line. The pubKeyToAddr function in keyUtils. Thus, having a child key does not make it possible to find its siblings, unless you also have the chain code. Note that you cannot determine the public key or the private key from the address. Just as with any other transaction, there is risk of swept transactions to be double-spending.
