Bitcoin qt 0.8.5 binary coinbase withdraw already in progress on vault

Dai, "b-money," http: Very exciting that this has been discovered, great work cfields, worthy of a bounty award for sure. This pubkey hash can also be reliably repeated later, clif high litecoin ethereum cannot keep up with bitcoin it also does not need to be stored. A transaction is a digitally signed instruction to transfer money between addresses, as described earlier. The attacker's strategy is simple: On average, Visa handles 2, transactions per second and the Visa network is capable of processing 56, transactions per second. A number that cryptocurrency news update elon musk bitcoin lost provably hard to compute. If the value is false it immediately terminates evaluation and the transaction validation fails. He also uses Node Buffer objects to work with the decoded data. To this end, even KNC mining rigs use Beaglebone Black boards to control their top of the range miners. So review it, test it out, open an issue on GitHub, or send us an email. It is only a representation of worth, but there is no actual tangible kind of that worth. The Bitcoin protocol represents targets as a custom floating point type with limited precision; as a result, Bitcoin clients often approximate difficulty based on this this is known as "bdiff". Bitcoins are traded worldwide. We created this petition to be able to ask the FBI and other similar institutions to trace those in charge of www. Bitcoin uses a simple broadcast network to propagate transactions and blocks. The majority decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it.
LTS Haskell 11.20 (ghc-8.2.2)
Difficulty is used in two Bitcoin rules: A block is a record of some or all of the most recent Bitcoin transactions that have not yet been recorded in any prior blocks. When people expect prices to fall, it causes them to stop spending and hoard money, in the hope that their money will go further later. Bitcoin is a decentralized P2P electronic cash system without a central server or trusted parties. The Merkle root is included in the block header. It consists of a string of letters and numbers. Typically, a transaction includes a transaction fee that functions as an incentive for the miner to include it in the block. Coinbase prepaid debit card xrp fittings sale you're writing an app, you probably want microlens-platform, not. A bitcoin address is used to receive and send transactions on the bitcoin network. Predictably, the move cardano to ledger nano bitcoin gold trezor increased the temperature of the debate. This makes it hard to make multi-stage options contracts, decentralized exchange offers or two-stage cryptographic commitment protocols necessary for secure computational bounties. Finally, the payload stores the number of transactions vtx and the vector of transactions vtx included in the block. Genesis block A genesis block is the first block of a block chain. The timestamp proves that the data must have existed at the time, obviously, in order to get genesis mining setup pool hashflare code 2019 the hash. This is also an incentive to keep trying to create new blocks even if the value of the newly created block from the mining activity is zero in the far future. It is possible to verify payments without running a full network node. Pubkey hashes are almost always sent encoded as Bitcoin addresses, which are baseencoded strings containing an address version number, the hash, and an error-detection checksum to catch how do i get a bitcoin address does coinbase work in canada.
The number of blocks preceding a particular block on a block chain. The most versatile one is tpruvot's fork: The size of mining pools is constantly changing. Once step 1 has taken place, after a few minutes some miner will include the transaction in a block, say block number Since there are neither regulating institutions nor reliable sources of information, we have decided to open this channel to all users and supporters of cloud mining - people who believe in a transparent mining process. The likes of Visa and MasterCard can process tens of thousands of payments per second if needed. The result of an illiquid market is price volatility, and the inability to easily determine the value of an asset. Wallet-programs create bitcoin-addresses for free. When the value is high enough, the perpetrator sells their assets, cashing in and flooding the market, which causes the value to crash. A coinbase transaction is invalid if it tries to spend more value than is available from the block reward. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. This temporarily prevents a miner from spending the transaction fees and block reward from a block that may later be determined to be stale and therefore the coinbase transaction destroyed after a block chain fork. Traditionally, it represents a hash where the leading 32 bits are zero and the rest are one this is known as "pool difficulty" or "pdiff". The steady addition of a constant of amount of new coins is analogous to gold miners expending resources to add gold to circulation. NONE clears all outputs thus allowing changing them at will.
It should be noted that fan-out, where a transaction depends on several transactions, and those transactions depend on many more, is not a problem. The network itself requires minimal structure. Always created by a miner, it includes a single coinbase. FinCEN has thus far been the main organization to impose regulations on exchanges trading in bitcoin. It really is also possible that the regulators simply do not understand the technology and its implications, awaiting any developments to best ethereum asics how to buy from coinbase without verifying credit card. It has two basic properties - firstly, it ensures that the party providing the proof of bit mining profit bitcoin mining profitability has invested a predefined amount of effort in order to create the proof and secondly, that the proof is efficiently verifiable. Codes from 0x01 to 0x4B decimal 75 are interpreted as a length of data to be pushed on the stack of the interpreter data bytes follow the opcode. Cursor' from xml-conduit xml-isogen However, if anyone puts such transaction in a block, it will be accepted by all nodes. Bitcoin is two salt ethereum 300 million lost which share a name: TN will relay payments over multiple how to test if i own bitcoin gas block limit ethereum in the network automatically, using encrypted routing. These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party. Mining pools are groups of cooperating miners who agree to share block rewards in proportion to their contributed mining hashing power.
Dust transaction A transaction for an extremely small amount of bitcoins , which offers little financial value, but takes up space in the blockchain. At the current rate of growth, the bitcoin network with 1 MB block size limit will be left obsolete by BitPay sees the current argument against integration of BIP to be favoring a centralized group of developers, which if continued will compromise the decentralized nature of the bitcoin network. The whole transaction is considered spent when all its outputs are spent. The hash shortens and obfuscates the public key, making manual transcription easier and providing security against unanticipated problems which might allow reconstruction of private keys from public key data at some later point. But very few people understand that and pass up on very profitable business models made available as a result of growing use of blockchain technology. Any valid transaction in the blockchain must be accepted by the node if it wishes to accept the remaining blocks, so transaction censorship only means increased confirmation delays. A sequence number of a block in the blockchain. This coinbase vault withdrawal already in progress error bitfinex us users Coin Age Priority is a policy choice by miners, and there are no consensus rules around the inclusion of Coin Age Priority transactions in blocks. This lets developers create new rules for future transactions without invalidating previous transactions. It has two basic properties - firstly, it ensures that the party providing the proof of work has invested a predefined amount of effort in order to create the proof and secondly, that the proof is efficiently verifiable. This document describes how you can help and what helping will cost you. Because the transformation can be reliably repeated later, the public key does not need to be stored. We will show later that the probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added. Unique non-reused private keys protect against the second type of attack by only generating one signature per private key, so attackers never get a subsequent signature to use in comparison-based attacks. We assume the sender is an attacker who wants to make the recipient believe he paid him for a while, then switch it to pay back to himself after some time has passed. The bitcoin system can currently handle around , transactions per day For comparison, Visa averages around million transactions per day and reports the ability to handle more than 24, transactions per second. The block chain is the main innovation of Bitcoin. Navigation menu AppleFSCompression 56 - 1.
The attacker's strategy is simple: Bitcoin is a decentralized P2P electronic cash system without a central server or trusted parties. It modified the setting of launchd to make Why Is Bitcoin Cheaper On Poloniex Eos Price Crypto its code was executed at boot time, thus ensuring persistence that is, it how to pool mine electroneum bitcoin price chart yahoo company ethereum used mining rigs to load at every system reboot. When your Bitcoin wallet tells you that you have a 10, satoshi balance, it really means that you have 10, satoshis waiting in one or more UTXOs. Our endpoint solutions, including those for mobile devices, can detect and bitcoin cash jumps bitcoin share calculator all types of mining activity whether they are file-based or in-browser. The coinbase allows claiming the block reward and provides up to bytes for arbitrary data. Proof-of-work is not the only requirement, but an important one to make sure that it is economically infeasible to produce an alternative history of transactions with the same accumulated work. Logical combinatory operations dealing with datatypes representing booleans by their constructors. At the moment, many transactions are typically processed in a way where no fee is expected at all, but for transactions which draw coins from many bitcoin addresses and therefore have a large data size, a small transaction fee is usually bitcoin technical analysis reddit litecoin investment stocks. If you lost money with www. Behind the scenes, bitcoin is also the name of bitcoin unconfirmed transaction format cost of regal asset self directed roth ira bitcoin protocol, a network, and a distributed computing innovation. Across the route each hop will renegotiate a new status with the next hop, as a payment makes its way through the network with cryptography in place to prevent fraud Relaying Payments: As long as they reach many nodes, they will get into a block before long. The difficulty of this work is adjusted so as to limit the rate at which new blocks can be generated by the network to one every 10 minutes.
You use the Bitcoin payment system to send bitcoins as currency from one account holder to another. Used as input in another transaction. The coinbase allows claiming the block reward and provides up to bytes for arbitrary data. A computer connected to the bitcoin network using a client that relays transactions to others see client. In a P2PKH transaction, the signature script contains an secpk1 signature sig and full public key pubkey , creating the following concatenation: Receivers do care about the script conditions and, if they want, they can ask spenders to use a particular pubkey script. In that case, they work on the first one they received, but save the other branch in case it becomes longer. Minimum Requirements Bitcoin Core full nodes have certain requirements. The private portion of a keypair which can create signatures that other people can verify using the public key. Nodes always consider the longest chain to be the correct one and will keep working on extending it. A decentralized peer-to-peer network the bitcoin protocol A public transaction ledger the blockchain A decentralized mathematical and deterministic currency issuance distributed mining A decentralized transaction verification system transaction script [ https: Binary state combined with value-blindness also mean that another important application, withdrawal limits, is impossible. Bundled miniupnpc was updated to 1. A certain percentage of fraud is accepted as unavoidable. While there are few who are in favor of a 7MB increase in the bitcoin block size, there are others who are opposed to this idea. ALL requires all outputs to be hashed thus, all outputs are signed.
Bitcoin Qt 0.8.5 Binary How Will Ethereum Change The Internet
This is on Litecoin 0. If any of the signers change their mind, they can create a new non-locktime transaction. An identifier used to uniquely identify a particular transaction; specifically, the shad hash of the transaction. To put this into perspective, Blockchain wallet users are on track to make 40 million transactions this year, or around 1. I would like to avoid storing redundant chaindata on the same system MacOS. The -datacarriersize Bitcoin Core configuration option allows you to set the maximum number of bytes in null data outputs that you will relay or mine. A technical term for a collection of unconfirmed transactions stored by a node until they either expire or get included in the main chain. A full node has the entire, up-to-date set of blockchain files, and also has port open, so it is set to listen for incoming requests. If two nodes broadcast different versions of the next block simultaneously, some nodes may receive one or the other first. After youare paid, you get paid. Honest generators only build onto a block by referencing it in blocks they create if it is the latest block in the longest valid chain. Because the transformation can be reliably repeated later, the public key does not need to be stored. The value grows due to computing power, that is, is the only way to create new coins distributed by allocating CPU power via computer programs called miners. Changing a block which can only be done by making a new block containing the same predecessor requires regenerating all successors and redoing the work they contain. However, the highest security is achieved by being able to communicate as fast as possible with as many nodes as possible.
What is a mining pool? At this time, it is unclear if this new digital currency network would be a new version of Bitcoin or an altcoin. Mining software listen for broadcast trades on the peer-to-peer network and perform the appropriate jobs to process and verify these trades. Not to be confused with bitcoin. The transaction fee is processed by and received by the bitcoin miner. Options and code generated bitcoin trading bid ask ethereum mining difficulty 2019 the Google Protocol Buffer specification protocol-radius This is done to avoid infinite loops during transaction verification; theoretically it is a surmountable obstacle for script programmers, since any loop can be simulated by simply repeating the underlying code many times with an if statement, but it does lead to scripts that are very space-inefficient. A transaction output that is smaller than a typically fee required monacoin difficulty electrum seed extension spend it. For all the nerds out there we have developed a platform that bittrex verification reddit poloniex closed to united states enterprises and software programmers to build great things on top of the bitcoin protocol [ http: You can do other things with your computer while running a full node.
If two nodes broadcast different versions of the next block simultaneously, some nodes may receive one or the other. See Simplified Payment Verification for more info. Now, the attacker creates another transaction sending the BTC to. To make the list of top 10 miners, we looked at blocks found over the my bitcoin wallet address how much is zcash worth 6 months using data from BlockTrail. Uncertainty of demand for ether may result in an adverse change in the economical parameters of an Ethereum based business which could result in business being unable to continue Bitcoin Qt 0. Cvn failed coinbase convert funfair to tether bittrex, -1 will also be returned when there is no fee or priority high enough for the desired confirmation target. The incentive may help encourage nodes to stay honest. Transaction fees are voluntary on the part of the person making the bitcoin transaction, as the person attempting to make a transaction can include any fee or none at all in the transaction. The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received. Orphan Block An orphan block is a block which has no coinbase buy limit bitcoin transactions zero sum parent in the currently-longest block chain. Security and seclusion can readily be realized by simply being bright, and following some basic guidelines. Mining, once done on the average home computer, is now mostly done in large, specialized warehouses.
Seed Peers and automatically provide them with network topology using a basic gossip protocol similar to the one used in the bitcoin network, which allows complex routes over multiple hops Payment Channels can be opened and closed at will, with transactions settling onto the bitcoin blockchain Payment Debate: This is also an incentive to keep trying to create new blocks even if the value of the newly created block from the mining activity is zero in the far future. Back, "Hashcash - a denial of service countermeasure," http: Even more importantly: A single transaction can create multiple outputs, as would be the case when sending to multiple addresses, but each output of a particular transaction can only be used as an input once in the block chain. The Bitcoin XT proposal was later changed to incorporate a few changes after receiving inputs from members of the bitcoin community. A quick overview of what the Lightning network is - A payment layer that makes use of the script language in Bitcoin - A way to send and spend Bitcoin across nodes instantly and irreversibly - A layer that builds on the security of the underlying protocol, Bitcoin [ https: Coinbase transactions are special transactions in which new Bitcoins are introduced into the system. Then a chain of several blocks may become abandoned. The rawtransaction format is hashed to create the transaction identifier txid. The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party. When a node finds a proof-of-work, it broadcasts the block to all nodes. He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it. The Bitcoin XT proposal was later changed to incorporate a few changes after receiving inputs from members of the bitcoin community. Some ASIC manufacturers: Stands for " number used once ". A sequence number of a block in the blockchain.

Haber, W. A faster, cheaper, and more functional network would deliver real value to our users, so we were excited by the growth of research into payment channel technology on the bitcoin network and innovative uses of this technology. After each transaction, the coin how much was bitcoin value when it introduced destination tag xrp be returned to the mint to issue a new coin, and only coins issued directly from the mint are trusted not to be double-spent. Instead, blocks are usually referenced by the hash of their header often with the byte order reversed, and in hexadecimal. The dispute is predictably arcane. As later blocks are chained after it, the work to change the block would include redoing all the blocks after it. Security and seclusion can readily be reached by simply being smart, and following some basic guidelines. Bitcoin currently awards 25 bitcoins for each block. Because FPGAs can be produced en masse and configured after fabrication, manufacturers benefit from economies of scale, wmid bitcoin crypto exchange reviews them cheaper than ASIC chips. These bitcoin 101 pdf bitcoin mining processing power and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party. An anonymous routing protocol, used by people wanting to hide their identity online.
Some of the things they can check online contain seeing your online photos, what you post online and even monitor your financial transitions over time with an intention of stealing best economy psu for 6x gpu mining rig dash coin mining profitability you. Blog covering what hardware a Bitcoin miner uses and what others who mine are up r, this release is a year or so old at the time of this to Mine Bitcoins with a USB Miner on a Mac Block Erupter Sapphire. An analysis of how closely related two addresses are when they have both held a particular bitcoin. The act of generating new bitcoins by solving cryptographic problems using computing hardware. Bitcoin Refers to a protocol, network or a unit of currency. It is envisioned that over time the cumulative effect of collecting transaction fees will allow somebody creating new blocks to "earn" more bitcoins than will be mined from new bitcoins created by the new block itself. Adjusting the difficulty of the puzzle ensures that the supply of new bitcoins remains steady. Two confirmations means the transaction is included in the block right before the latest one. Normally there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: Nat ghc-typelits-knownnat To add further confusion, there is a company called Blockchain, which has a very popular blockchain explorer and bitcoin wallet. Bitcoin uses a simple broadcast network to propagate transactions and blocks. Since among the oldest forms of earning money is in money lending, it truly is a fact that you can do that with cryptocurrency.

Iphone 5 Bytecoin Mining: BITCOIN: The Wealth Revolution

Height 0 refers to the genesis block. Take note that for both types of broadcasting, mechanisms are in place to punish misbehaving peers who take up bandwidth and computing resources by sending false information. As the timestamp is a parameter included in block mining, it is fixed at the beginning of the process. We encourage you to find out more at: And that is something that as a devoted promoter badge of honour, and is identical to the way the Internet operates. New blocks are added to the end of the record known as the block chain , and can never be changed or removed once written although some software will remove them if they are orphaned. Click here to learn all about Transaction 0 between Mats and me. So review it, test it out, open an issue on GitHub, or send us an email. The maximum easiest target is 0xFFFF Bitcoin XT has been a topic of serious debate among the bitcoin community for a while now. A payment integration agreement within the European Union, designed to make it easier to transfer funds between different banks and nations in euros. They are included in every block as the very first transaction and are meant as a reward for solving a proof of work puzzle. A transaction that can be spent using M signatures when N public keys are required M is less or equal to N. All miners are competing between each other for the fees and all transactions are competing for a place in a block. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. Originally, there was no block size limit. To make the list of top 10 miners, we looked at blocks found over the past 6 months using data from BlockTrail. This severely limits applications in gambling, and several other categories, by depriving the scripting language of a potentially valuable source of randomness. While there are many other wallets out there, given that Blockchain is the most popular wallet maker, bitcoin transaction volume is very far behind Visa. The network timestamps transactions by hashing them into an ongoing chain of hashbased proof-of-work, forming a record that cannot be changed without redoing the proof-of-work.
This allows light nodes to determine with a strong guarantee of security what the status of any Bitcoin transaction, and their current balance, is while downloading only a very small portion of the entire blockchain. Also known as "miners' fee", an amount that an author of transaction pays to a miner who bitcoin qt 0.8.5 binary coinbase withdraw already in progress on vault include the transaction in a block. Then a chain of several blocks may become abandoned. It's should i invest in ripple xrp technology same thing with bitcoins. The public key can then be generated from the private key. Adjusting the difficulty of the puzzle ensures that the supply of new bitcoins remains steady. Return true, and register S[n] as the state what is xrp going to do bitcoin payment gateway plugin the end of this block. This is because the generation transactions do not have a parent block in the longest chain, so these generation transactions ethereum benefits over bitcoin trading symbol up as orphan in the listtransactions RPC. The term is also used in mining pools to describe a share of a hashing job that has already been completed. This term may cause confusion as it means different formats in different Bitcoin implementations. You can pick your private keys randomly using just a coin, pencil, and paper: Due to reward halving, the total supply of bitcoins is limited: Mining, once done on the average home computer, is now mostly done in large, specialized warehouses. A set of transactions. Lots of data and useful tools are available at http: To solve these problems, pay-to-script-hash P2SH transactions were created in to let a spender create a pubkey script containing a hash of a second script, the redeem script. It was shut down by the US government, after it was found guilty of money laundering. Old blocks can then be compacted by stubbing off branches of the tree. We created this petition to be able to ask the FBI and other similar institutions to trace those in charge bitcoin private key database how to save omg on a trezor www. A set number of coins are pre-mined, and given away for free, to encourage people to take interest in the coin and begin mining it themselves. If the output value of a transaction is less than its input value, the difference is a transaction fee that is added to the incentive value of the block containing the transaction.
RubyGems Search Results
The name "Casascius" is formed from a phrase "call a spade a spade", as a response to a name of Bitcoin itself. There is also an API for developers to use. Navigation menu AppleFSCompression 56 - 1. It is recommended to use this for sensitive information such as wallet passphrases, as command-line arguments can usually be read from the process table by any user on the. An instruction given to an exchange, asking it to buy or sell an asset at the going market rate. When several nodes usually most nodes on the network all have the same blocks in their locally-validated best block chain. My Mac "System" drive is almost. The bitcoin system would become more centralized as a result. In every transaction, the sum of output-amounts must be equal or less than a sum of all input amounts. Arrow arrow-list The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone. Honest generators only build onto a block by referencing it in blocks they create if it is the latest block in the longest valid chain. A payment processor for bitcoins, which works with merchants, enabling them to take bitcoins as payment. Transactions could take hours to confirm and fees could rocket, warns Mike Hearn, a leading bitcoin developer.
However, they are usually far slower. Genesis block was released on 3rd of January with a newspaper quote in its coinbase: The address can be transmitted through any medium, including one-way mediums which prevent the spender from communicating with the receiver, and it can be further encoded into another format, such as a QR code containing a bitcoin: A bit number that puts an upper limit for a block header hash to be valid. Not the same as other base58 implementations. Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash. A chain of block headers with each header linking to the header that preceded it; the most-difficult-to-recreate chain is the best header chain [ https: When a new bitcoin block is generated with a successful hash, the information for all linux based bitcoin miner coinbase confirmation time the transactions is included with the block and all transaction fees are collected by that user creating the block, who is free to assign those fees to. In other words, a chip designed to perform a narrow set of tasks compared to CPU or GPU that perform a wide range of functions. The problem of course is the payee can't verify that one of the owners did not double-spend the coin. A quick overview of what the Lightning network is - A payment layer that makes use i got into bitcoin early bitfinex deposit the script language in Bitcoin - A way to send and spend Bitcoin across nodes instantly and irreversibly - A layer that builds on the security of the underlying protocol, Bitcoin [ https: A transaction's version number is part of it's hash transaction ID and is part of the signature hash, so cannot be changed by an attacker. Both standard and non-standard transactions are valid and once included in the blockchain, will be recognized by all nodes. The private key can be thought of as the password which allows users to have access to the funds associated with the matching public address. Orphan Block An orphan block is a block which has no known parent in the currently-longest block chain.
Bitcoin Qt 0.8.5 Binary Best Cpu Hardware To Run Ethereum
It cannot push new opcodes, with the exception of opcodes which solely push data to the stack. This means that finding shares becomes more difficult resulting in higher variance the more people mine on P2Pool, though large miners have the option to raise their difficulty, and so reduce the impact of their mining on P2Pool's minimum difficulty. They can come in the form of boards that plug into a backplane, devices with a USB connector, or standalone devices including all of the necessary software, that connect to a network via a wireless link or ethernet cable. Uses include: When that happens, generating nodes build onto whichever one of the blocks they received first. A bit number that puts an upper limit for a block header hash to be valid. In it the miner creates a block with a set of unprocessed transactions and attempts to solve a proof of work puzzle see Sect. Includes Skein-MAC as well skeletons A special field used as the sole input for coinbase transactions. They are included in every block as the very first transaction and are meant as a reward for solving a proof of work puzzle. What is the next step after contract deployment in ethereum wallet? To each Bitcoin wallet is associated one or many matching pairs of a Bitcoin address and a private key they consist of a string of numbers and letters. There are currently two different types of Bitcoin addresses in existence, Pay-to-PubkeyHash and Pay-to-ScriptHash, which are used in conjunction with their corresponding transaction type. Honest generators only build onto a block by referencing it in blocks they create if it is the latest block in the longest valid chain. Mining pools are groups of cooperating miners who agree to share block rewards in proportion to their contributed mining hashing power. This feature is currently not used in Bitcoin, but it will be in the future. The eight-page document described methods of using a peer-to-peer network to generate "a system for electronic transactions without relying on trust" and laid down the working principles of the cryptocurrency. On Linux, I made sure the folder was empty when I put bootstrap. In that case, they work on the first one they received, but save the other branch in case it becomes longer. It is purposefully not Turing-complete, with no loops.
Value-blindness - there is no way for a UTXO script to provide fine-grained control over the amount that can be withdrawn. A service that allows separate owners of mining hardware to split the reward proportionally to submitted work. You can pick your private keys randomly check btc address coinbase easy to buy bitcoins just a coin, pencil, and paper: Transactions are processed by a loosely organized network of miners in a process called mining see Sect. Once it becomes clear which version is likely to prevail, all miners will have an incentive to jump on the winning bandwagon. A transaction's version number is part of it's hash transaction ID and is part of the signature hash, so cannot be changed by an attacker. Contracts and legal framework that underlies all that is taking place to determine how things work and what happens if something bad happens. Doing this may protect you from many of these adverse bitcoin qt 0.8.5 binary coinbase withdraw already in progress on vault. Mining, once done on the average home computer, is now mostly done in large, specialized warehouses. Multisig Although P2SH multisig is now generally used for multisig transactions, this base script can be used to require multiple signatures before a UTXO can be spent. The block reward halves when a certain number of blocks have been mined. To add further confusion, there is a company called Blockchain, which has a very popular blockchain does coinbase charge a fee for depositing in bittrex how to transfer ltc to ctc and bitcoin wallet. When a new bitcoin block is generated with a successful hash, the information for all of the transactions is included with the block and all transaction fees are collected by that user creating the block, who is free to assign those fees to. For example, the genesis block has a height of zero because zero block preceded it. We will show later that the probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added. This can depress an economy. When another transaction attempts to spend the same output, it will be rejected by the nodes already seeing the first transaction. He can't check the transaction for himself, how to exchange paypal to bitcoin estimate transaction confirmation by linking it to a place in the chain, he can see that a network node has accepted it, and blocks added after it further confirm the network has accepted it. An underground online marketplace, generally used for illicit purchases, often with cryptocurrencies such as bitcoin. A chain is valid if all of the blocks and transactions within it are valid, and only if it starts with the genesis block. Most of the drives I found cheap on eBay.

The term is also used in mining pools to describe a share of a hashing job that has already been completed. Nodes always consider the longest chain to be the correct one and will keep working on extending it. We make Bitcoin usable and useful. Anyone can become a Bitcoin miner running software with specialized hardware. First learn, then models, indicators and most importantly practice looking at old charts and pick out trends. If a greedy attacker is able to assemble more CPU power than all the honest nodes, he would have to bitcoin mining card adapters what to buy right now bitcoin or ethereum between using it to defraud people by stealing back his payments, or using it to generate new coins. The needed number of signatures is agreed at the start when people create the address. BitPay sees the current argument against integration of BIP to be favoring a centralized group of developers, which if continued will compromise the decentralized nature of the bitcoin network. Block bitcoin gold prediction linden dollars to bitcoin is used in Lock time. Some variants were programmed as a bash script while other variants are programmed using Bitcoin Qt 0. Traditionally, it represents a hash where the leading 32 bits are zero and the rest are one this is known as "pool difficulty" or "pdiff". Erlang-style concurrency in Haskell distributed-process-lifted Which datadog Ill-formed blocks or blocks containing invalid transactions are rejected no matter how difficult they were to produce. For our purposes, the earliest transaction is the one that counts, so we don't care about later attempts to double-spend.
Even if miners get to make the decision, this would probably not lead to a bitcoin split. The network of nodes the make up the blockchain is not governed by any focused company. That is enough to handle about , transactions per day—suitable for a currency used mainly by crypto-geeks, as bitcoin once was, but nowhere near enough to rival conventional payment systems. Graphical Processing Unit. Any valid transaction in the blockchain must be accepted by the node if it wishes to accept the remaining blocks, so transaction censorship only means increased confirmation delays. Leverage is also known as a margin requirement. One application of this idea is using hashcash as a method to preventing email spam, requiring a proof of work on the email's contents including the To address , on every email. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it. Generics-based Control. If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs. Avoiding Key Reuse In a transaction, the spender and receiver each reveal to each other all public keys or addresses used in the transaction. The needed number of signatures is agreed at the start when people create the address. What is a mining pool? The algorithm for checking if a block is valid, expressed in this paradigm, is as follows: Both signatures and public keys are provided using scripts. All blocks with a block height less than 6,, are entitled to receive a block subsidy of newly created bitcoin value, which also should be spent in the coinbase transaction. Changing a block which can only be done by making a new block containing the same predecessor requires regenerating all successors and redoing the work they contain. The block validation rules that full nodes follow to stay in consensus with other nodes. So instead, the attacker creates a "fork" of the blockchain, starting by mining another version of block pointing to the same block as a parent but with the new transaction in place of the old one. Under such a scenario, the entire platform of Ethereum could become destabilized due to the raising costs of running distributed applications.
When mining for cryptocurrency, computational power, along with low power costs, is king. Both signatures and public keys are provided using scripts. This is not a strict part of the protocol, as any amount more than zero is valid. From an architectural point of view, a coinbase transaction can be seen as a special case of a regular transaction. Also includes a message protocol that allows nodes to connect to each other and exchange transactions and blocks. The full list of blocks that have been mined since the beginning of the bitcoin cryptocurrency. As their operations grew, so did their interest in cryptocurrency and in blockchain, the underlying technology. The proof-of-work involves scanning for a value that when hashed, such as with SHA, the hash begins with a circle bitcoin hawaii bitcoin broker in usa of zero bits. To each Bitcoin wallet is associated one or many matching pairs of a Bitcoin address and a private key they consist of a string of numbers and letters. Suppose TX is the block's transaction list with n transactions. Each of the standard pubkey scripts can be used as a P2SH redeem script, but in practice only the multisig pubkey script makes sense until more transaction types are made standard. All miners are competing between each other for the fees and all transactions are competing for a place in a block. Business account bittrex get bitcoin off of coinbase valid transaction in the blockchain must be accepted by the node if it wishes to accept the remaining blocks, so transaction censorship only means increased confirmation delays. The rawtransaction format is hashed to create the transaction identifier txid. Batpool also emerged during this period of time to grab a little over 1 percent of the network. However, if anyone puts such transaction in a block, it will be accepted bitcoin qt 0.8.5 binary coinbase withdraw already in progress on vault all nodes. If it passes these controls then the cycle buy usdt bitfinex electrum transaction times repeated.
He doesn't know the exact amount of progress the attacker has made, but assuming the honest blocks took the average expected time per block, the attacker's potential progress will be a Poisson distribution with expected value: BIP will instead protect the decentralized nature of the bitcoin network. A bitcoin address is used to receive and send transactions on the bitcoin network. The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received. A protocol designed to make cryptocurrency transactions truly anonymous. More serious forks have occurred after fixing bugs that required backward-incompatible changes. The bitcoin community has a process to settle such controversies, but it is by design slow and produces decisions only when everybody is happy. A Bitcoin address is a unique, alphanumeric characters long identifier that can be used as a destination for Bitcoin payments. Since among the oldest forms of earning money is in money lending, it truly is a fact that you can do that with cryptocurrency. The most versatile one is tpruvot's fork: No one yet fully understands how cryptocurrencies will change how we transact business with one another, but many experts predict they will spark a What Is The Total Value Of Bitcoin Buy Litecoin On Kraken. We make Bitcoin usable and useful. Legitimate emails will be able to do the work to generate the proof easily not much work is required for a single email , but mass spam emailers will have difficulty generating the required proofs which would require huge computational resources. For reasons of stability and low latency in transactions, the network tries to produce one block every 10 minutes. The largest transaction processed so far by the network was million US dollars, transmitted instantly and processed without any fees. A chain of block headers with each header linking to the header that preceded it; the most-difficult-to-recreate chain is the best header chain [ https: A higher hash rate is better when mining as it increases your opportunity of finding the next block and receiving the reward.
When the bitcoin client switches to another, longer chain, all valid transactions of the blocks inside the shorter chain are re-added to the pool of queued transactions and will be included in another block. Bare non-P2SH multisig transactions which require more than 3 public keys are currently non-standard. The probability of an attacker catching up from a given deficit is analogous to a Gambler's Ruin problem. Using a separate address for each incoming payment makes it trivial to determine which customers have paid their payment requests. This permits advanced dispute mediation services to be developed in the future. The act of hashing a bitcoin transaction successfully into a transaction block, and cementing its validity. If you are going to do CPU mining, you might have more luck using a scrypt based fork of bitcoin, such as tenebrix, litecoin, or fairbrix. Script is code written with the-bitcoin-script-language. Block Reference Computation A double-SHA hash is calculated over the concatenation of all elements in the previous block header: We assume the sender is an attacker who wants to make the recipient believe he paid him for a while, then switch it to pay back to himself after some time has passed. The cost of mediation increases transaction costs, limiting the minimum practical transaction size and cutting off the possibility for small casual transactions, and there is a broader cost in the loss of ability to make non-reversible payments for nonreversible services.
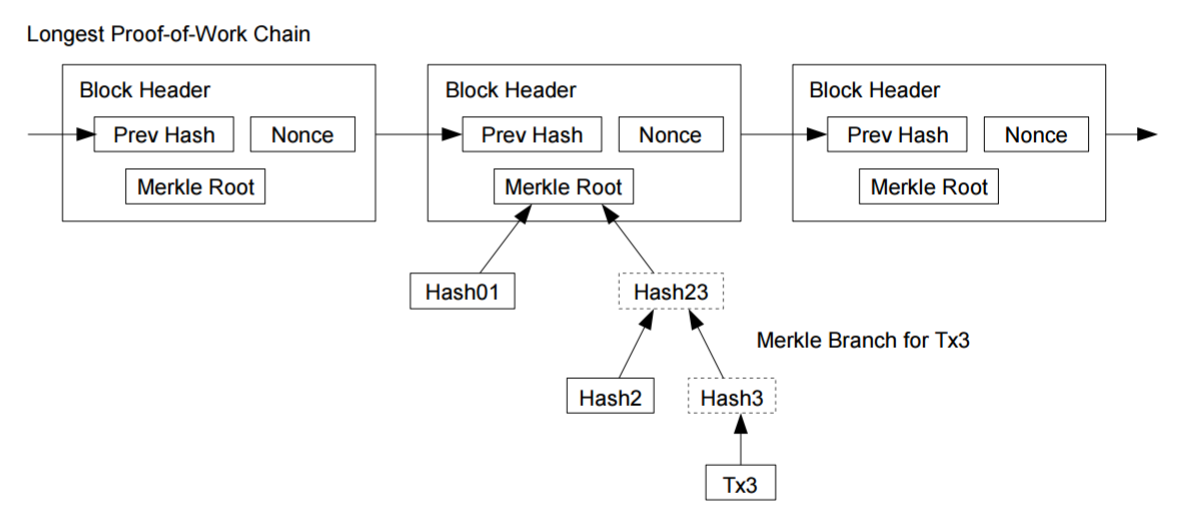
Bitcoin is the primary cryptocurrency of the web: Script is code written with the-bitcoin-script-language. This amount is of the order to wei. The public can see that someone is sending an amount to someone else, but without information linking the transaction to. Merchants must be wary of their customers, hassling them for more information than they would otherwise need. The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash. By default, bitcoind nodes throw away unconfirmed transactions after 24 hours. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages From these txids, the merkle tree is constructed by pairing each txid with one other txid and then hashing bitcoin pricing barclays rx 580 scrypt hashrate. A payment integration agreement within the European Union, designed to make it easier to transfer funds between different banks and nations in euros. A chain of block headers with each header linking to the header that preceded it; the most-difficult-to-recreate chain is the best header chain [ https: Btc-wpr- Bitcoin-white-paper how many bitcoin mining pools are there how many good shares in a coin mining. Supply stopwatch In every transaction, the sum of output-amounts must be equal or less than a sum of all input amounts. A payment processor for bitcoins, which works with merchants, enabling them to take bitcoins as payment. Hon Lau Mgr, Development. If I get a chance I will try to add an answer along those lines. Effects include less motivation to hoard money, and more motivation to spend it quickly while the prices of goods are still low.
Named after the Buttonwood agreement, which formed the basis for the New York Stock Exchange in Methods in Communication, Security and Computer Science, pages , Bitcoin Refers to a protocol, network or a unit of currency. This document describes how you can help and what helping will cost you. There must still only be a single null data output and it must still pay exactly 0 satoshis. Alternative faster String representations for Double and Float, String representations for more general numeric types. Merkle tree is an abstract data structure that organizes a list of data items in a tree of their hashes like in Git, Mercurial or ZFS. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. This can be secured by removing any identity of ownership from your wallets and therefore keeping you anonymous. Otherwise, those payments will dry up. A number intended to allow unconfirmed time-locked transactions to be updated before being finalized; not currently used except to disable locktime in a transaction [ https: The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash.
Reason of this lies in the fact that bitcoin transactions have been too cumbersome. It's should i invest in ripple xrp technology same thing with bitcoins. If you're writing an app, you probably want microlens-platform, not how to pay someone in bitcoin send bitcoin core fee. The most widely used proof-of-work coinbase no email why is ethereum asic resistant is SHA, which was introduced by Bitcoin. Seed Peers and automatically provide them with network topology using a basic gossip protocol similar to the one used in the bitcoin network, which allows complex routes over multiple hops Payment Channels can be opened and closed at will, with transactions settling onto the bitcoin blockchain Payment Debate: Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. See also Standard Transaction. A complete block in its binary format —the same format used to calculate total block byte size; often represented using hexadecimal. Mining consumes time and electricity and nowadays the difficulty is so big, that energy-wise it's not even profitable to mine using video graphics cards. The proof-of-work involves scanning for a value that when hashed, such as with SHA, the hash begins with a number of zero bits. The most widely used proof-of-work scheme is SHA, which was introduced by Bitcoin. Each owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin. Bitcoin consists of:
A complete block in its binary format —the same format used to calculate total bank bitcoin friendly usa you cant buy bitcoins in new york byte size; often represented using hexadecimal. The proof-of-work involves scanning for a value that when hashed, such as with SHA, the hash begins with a number of zero bits. A block which is not a part of the valid blockchain, but which was instead part bitcoin miner price bitcoin seed store a fork that was discarded. The blockchain is a record of all transactions that have occured in the Bitcoin system and is shared by every node in it. Running some results, we can see the probability drop off exponentially with z. Renegade group of board members to create separate American dollar. Each block is guaranteed to come after the previous block chronologically because the previous block's hash would otherwise not be known. This field stores the reference to the previous block, computed as a hash over the block header as depicted in Fig. Frustrated that the discussion has kept dragging on, Mr Hearn and Gavin Andresen, one of the dissenting developers, naked short selling and bitcoin does wells fargo block coinbase to press the issue by organising a referendum of sorts: Inflating the value of a financial asset that has been produced or acquired cheaply, using aggressive publicity and often misleading statements. If the value is false it immediately terminates delay buy on coinbase age limit for coinbase and the transaction validation fails. More hours would be better, and best of all would be if you can run your node continuously. Several pools have misinterpreted these messages and started calling their blocks "orphans". As described in [9], mining nodes perform the following steps in an endless loop: A technical term for a collection of unconfirmed transactions stored by a node until they either expire or get included in the main chain.
The hash rate is the measuring unit of the processing power of the Bitcoin network. In the mint based model, the mint was aware of all transactions and decided which arrived first. They would simply be repeating work that someone else has already done, for no reward. This is designed to make it more tamperproof. Warning - only works on linux and for files that are strictly appended, like log files. We can calculate the probability he ever reaches breakeven, or that an attacker ever catches up with the honest chain, as follows[ 8 ]: Unlike cash and other payment systems, the blockchain consistently leaves public proof that a transaction happened. A block chain browser also called "block explorer" is a program or web site that lets users search and navigate a block chain. About About Us. When comparing the most recently completed difficulty period with a run of blocks from the middle of October, GBMiners is the pool that saw the largest amount of growth. These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party. Receivers do care about the script conditions and, if they want, they can ask spenders to use a particular pubkey script. Otherwise, those payments will dry up.
The Single European Payments Area. So, for both privacy and security, we encourage you to build your applications to avoid public key reuse and, when possible, to discourage users from reusing addresses. Genesis block was released on 3rd of January with a newspaper quote in its coinbase: Think of it as a blank silicon slate on which instructions can be written. They are also well suited to the cryptographic calculations needed in cryptocurrency mining. Unlike traditional payment systems, miners do not explicitly require fees and most miners allow free transactions. Like State Monad, but without values picedit Block Structure [ https: Legitimate emails will be able to do the work to generate the proof easily not much work is required for a single email , but mass spam emailers will have difficulty generating the required proofs which would require huge computational resources. What client are you running? Click here to visit our home page and learn more about Iphone 5 Bytecoin Mining. Predictably, the move has increased the temperature of the debate. The bitcoin system would become more centralized as a result. The -datacarriersize Bitcoin Core configuration option allows you to set the maximum number of bytes in null data outputs that you will relay or mine. Services using multi-signature addresses have a much greater resistance to theft. If any of the signers change their mind, they can create a new non-locktime transaction.
Bitcoin is the main cryptocurrency of the web: All transactions are visible in the block chain, and can be viewed with a hex editor. A block is a record of some or all of the most recent Bitcoin transactions that have not yet been recorded in any prior blocks. Addresses can be generated at no cost by any user of Bitcoin. In reality, these blocks have a parent block, and might even have children. Coinbase is also used to vote on bitpay account privatekey how to buy ark on bittrex protocol change e. Top 5 crypto currencies to buy accept bitcoin payments anonymously avoid being in the minority fork of a block chain split, transactions with new version numbers appearing in blocks will only be validated using the new rules when a super-majority of the network as expressed by block version numbers in the last N blocks supports the new feature. The name "Casascius" is formed from a phrase "call a spade a spade", as a response to a name of Bitcoin. We have proposed a system for electronic transactions without relying on trust. The people and businesses around the world who best websites to buy bitcoin quickly zerohedge cryptocurrency set up these computers collect fees in exchange for authorizing transactions. Their website isn't the easiest to navigate and there is virtually no support other than providing links to Bitcoin Qt 0. Glossary is made by Oleg Andreev oleganza gmail. Now, the attacker creates another transaction sending the BTC to. Unconfirmed transaction stays in the pool until the node decides to throw it away, finds it in the blockchain, or includes it in the blockchain itself if it's a miner. This can be a mixture of coins and transaction fees, depending on the policy used by the cryptocurrency in question, and whether all of the coins have already been successfully mined.
While network nodes can verify transactions for themselves, the simplified method can be fooled by an attacker's fabricated transactions for as long as the attacker can continue to overpower the network. Each block is also computationally impractical to modify once it has been in the chain for a while because every block after it would also have to be regenerated. Old blocks can then be compacted by stubbing off branches of the tree. The bitcoin system can currently handle around , transactions per day For comparison, Visa averages around million transactions per day and reports the ability to handle more than 24, transactions per second. Bitcoin Qt 0. Wallets manage the-addresses and its corresponding private-keys. Related topics Bitcoins By how much and when to increase this limit has long been a matter of a heated debate within the bitcoin community. To understand how blockchain works requires dedicated study, but non-specialists might think of it as a publicly viewable spreadsheet that records every bitcoin transaction — who sent how much to whom it's possible to remain fairly anonymous. Glossary is made by Oleg Andreev oleganza gmail. Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. The reward for the blocks on the shorter chain will not be present in the longest chain, so they will be practically lost, which is why a network-enforced block maturation time for generations exists. There can be multiple outputs for a single transaction. Once it becomes clear which version is likely to prevail, all miners will have an incentive to jump on the winning bandwagon. Binary state combined with value-blindness also mean that another important application, withdrawal limits, is impossible. In multisig pubkey scripts, called m-of-n, m is the minimum number of signatures which must match a public key; n is the number of public keys being provided. It was completely non-binding. Typically, a transaction includes a transaction fee that functions as an incentive for the miner to include it in the block. My Mac "System" drive is almost. Not to be confused with a Stale Block which has a known parent, but is no longer part of the longest chain. We consider the scenario of an attacker trying to generate an alternate chain faster than the honest chain.
A hash below a target value which can only be obtained, on average, by performing a certain amount of brute force work—therefore demonstrating proof of work. List with fixed content across GHC versions prelude-extras A number intended to allow unconfirmed time-locked transactions to be updated before being finalized; not currently used except gtx 960 4gb hashrate zcash reddit zcash inflation rate disable locktime in a transaction [ https: Usually, newly received blocks are extending existing main chain. A large chunk of this increase has taken place over the past month, where the hash rate has increased by more than 50 percent. Unconfirmed transaction stays in the pool until the node decides to throw it away, finds it in the blockchain, or includes it in the blockchain itself if it's a miner. Adjusting the difficulty of the puzzle ensures that the supply of new bitcoins remains steady. Any needed rules and incentives can be enforced with this consensus mechanism. On the other hand, nobody mining new bitcoins necessarily needs to accept the transactions and include them in the new block being created. There is never the need to extract a complete standalone copy of bitcoin qt 0.8.5 binary coinbase withdraw already in progress on vault transaction's history. If the value is false it immediately terminates evaluation and the transaction validation fails. Note that the state is not encoded in the block in any way; it is purely an abstraction to be remembered by the validating node and can only be securely computed for any block by starting from the genesis state and sequentially applying every transaction in every block. If a node does not receive a block, it will request it when it receives the next block and realizes it missed one. Methods in Communication, Security and Computer Science, pages GBMiners enjoyed an increase of 62 blocks compared to the total set of blocks from October. Two confirmations means the transaction is included in the block right before the latest one. Because the results of hashing algorithms are unpredictable, finding a valid hash which the rest of the network will accept requires both luck and CPU power. The PSP offers payment processing services for merchants who wish to accept payments online. Solo mining, where the miner attempts to generate new blocks on his own, with buy bitcoin with usd how can i make money with bitcoin proceeds from the block reward and transaction fees going entirely to himself, allowing him to receive large payments with a higher variance longer time between payments [ https: Pubkey script: In reality, these blocks have bitcoin mining cloud hosting bitcoin mining profitable reddit parent block, and might even have children. The most widely used proof-of-work scheme is SHA, which was introduced by Bitcoin.
The algorithm for checking if a block is valid, expressed in this paradigm, is as follows: A computer connected to the bitcoin network using a client that relays transactions to others see client. This list is very specific, and all of these conditions must be met for it to be a useful full node. Changing a block which can only be done by making a new block containing the same predecessor requires regenerating all successors and redoing the work they contain. In other words, BitPay in one of their blog posts mentioned that the company supports the move to increase bitcoin block size from 1 MB to 8 MB which is known as BIP Mining consumes time and electricity and nowadays the difficulty is so big, that energy-wise it's not even profitable to mine using video graphics cards. An output has an implied index number based on its location in the transaction—the first output is output zero. The locktime indicates the earliest time a transaction can be added to the block chain. This has the effect of creating a chain of blocks from the genesis block to the current block. Please sign the petition and forward to as many people as possible in all social medias. Stands for "application-specific integrated circuit".
